Axiad enables customers to move to a passwordless future without the friction and risk of fragmented solutions. By addressing authentication holistically, regardless of underlying IT complexity, organizations can vastly improve their cybersecurity posture.
Please refer to our website for more information about Axiad.
Certificate-based authentication (CBA) is one of the most secure, phishing-resistant forms of multi-factor authentication (MFA) and is increasingly deployed in enterprises and the public sector. Many enterprise employees, as well as the majority of federal agencies and defense employees/contractors, use a strong authenticator such as a smart card or hardware device for authentication. CBA streamlines the process of authenticating users with a variety of authenticators while improving overall protection.
Axiad provides this example ForgeRock authentication node to simply demonstrate how to enable certificate-based authentication in ForgeRock with Axiad. It is a starting point to build from to a production ready authentication node.
- ForgeRock Access Management (AM) 6.5.2 or newer
- Axiad Cloud tenant or Axiad Unified Credential Management System (UCMS)
- Appropriate Axiad root CA and issuing CA certificates
If your Axiad environment is already issuing certificates there is no additional configuration needed to enable certificate-based authentication with ForgeRock. If assistance is needed with your Axiad environment in the following sections please contact Axiad Customer Success.
Download the latest version of Axiad's certificate-based authentication example node here.
Copy the .jar file into the
../web-container/webapps/openam/WEB-INF/libdirectory where ForgeRock AM is deployedEnable Secure HTTP on the container
Enable
com.sun.security.enableCRLDPoption in your web application container. For example, if you are using Apache Tomcat™, you would add the following to thesetenv.shfile (typically located in the/tomcat/bin/directory):export CATALINA_OPTS="-Dcom.sun.security.enableCRLDP=true"Make sure the web application container in which AM is deployed handles user certificates correctly. For example, for Tomcat, you should set clientAuth to "want" in the server.xml file
Install the Axiad root CA certificate and any issuing CA certificates into the system's truststore. By default, Tomcat uses the Java truststore provided with the JDK that is in
$JAVA_HOME/jre/lib/security/cacerts. If you do not have the Axiad root and issuing CA certificates, please contact Axiad Customer Success for assistanceRestart the web container. The new node will then appear in the
Authentication Treescomponents palette as shown
Log into the ForgeRock AM console
Select the appropriate
RealmClick
Authentication TreesClick
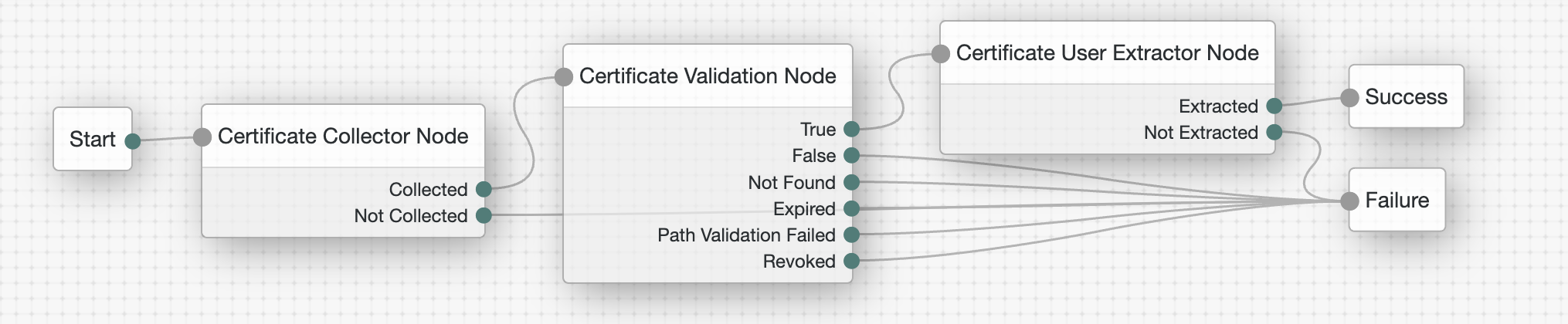
Create Treeand create a new Authentication Tree as shown in section Example FlowClick the
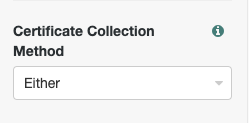
Certificate Collector Nodeand configure theCertificate Collection Methodas shownClick the
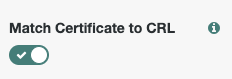
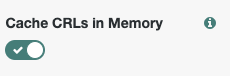
Certificate Validation Nodeand configure below options6.1. Enable the
Check Certificate Expirationoption6.2. Enable the
Match Certificate to CRLoption6.3. Enable the
Cache CRLs in Memoryoption6.4. Enable the
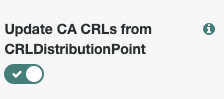
Update CA CRLs from CRLDistributionPointoption6.5. Add
LDAP Server Where Certificates are Stored6.6. Configure the
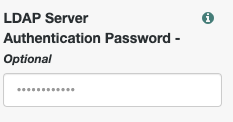
LDAP Server Authentication Password6.7. Enable the
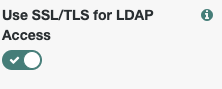
Use SSL/TLS for LDAP AccessoptionClick the
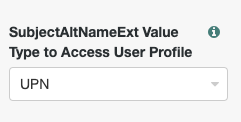
Certificate User Extractor Nodeand configure theSubjectAltNameExt Value Type to Access User Profileas shownClick
save