Enzoic specializes in cyber-security and fraud detection Cybersecurity is a complex and ever-evolving market. Compromised credentials remain a large risk for most organizations and the attackers are getting more sophisticated each year.
Organizations need solutions that combine cloud security expertise and innovative, easy-to-deploy tools to layer-in with other security measures.
Enzoic was created as a streamlined solution to detect compromised credentials with minimal friction for end users.
The Enzoic-Auth tree nodes are packaged as a jar file and the latest release can be download here. Once downloaded, copy the jar file to the ../web-container/webapps/openam/WEB-INF/lib
Below are the nodes that will be available after deploying the jar file:
This node will check compromised password using enzoic java client.
Configuration is:
- API Key : API Key to call enzoic api.
- Secret : Secret to call enzoic api
- Synchronous/Asynchronous : Flag to set flow as Synchronous or Asynchronous (should the user be granted immediate access or wait for the Enzoic API to return.
- Credential Check Timeout : Timeout for password ping api and it should be enter in MilliSeconds
- User Attribute : The attribute on the users profile which which will contain output for Asynchronous flow results . This attribute should be defined in AM identity store.
- Unique Identifier : The unique user identifying attribute to check against the Enzoic API.
- Local password file path : Local csv file location which contains compromised passwords.
- Local password Cache Expiration Time: The cache expiration for Local Password Check in seconds.
- Check Compromised Password : Boolean value to select whether to check password against local file or the Enzoic API.
This node will collect new password to reset the password.
Configuration is:
- Minimum Password Length : The minimum password length for new passwords.
This node will save new password for the user. There are no configurable attributes for it.
Applies retry logic if entered password for reset password node is also a compromise password. This is a built in ForgeRock Node
Configuration is:
- Retry Limit : The number of times to allow a retry.
Display message to the user.
Configuration is:
Message : Localisation overrides - as key fill shortcut for language (first will be used as default if not empty or "Default message" if empty), value is message for language defined by key.
Positve Answer : Localisation overrides - as key fill shortcut for language (first will be used as default if not empty or "Yes" if empty), value is positive answer for language defined by key.
Negative Answer : Localisation overrides - as key fill shortcut for language (first will be used as default if not empty or "No" if empty), value is negative answer for language defined by key.
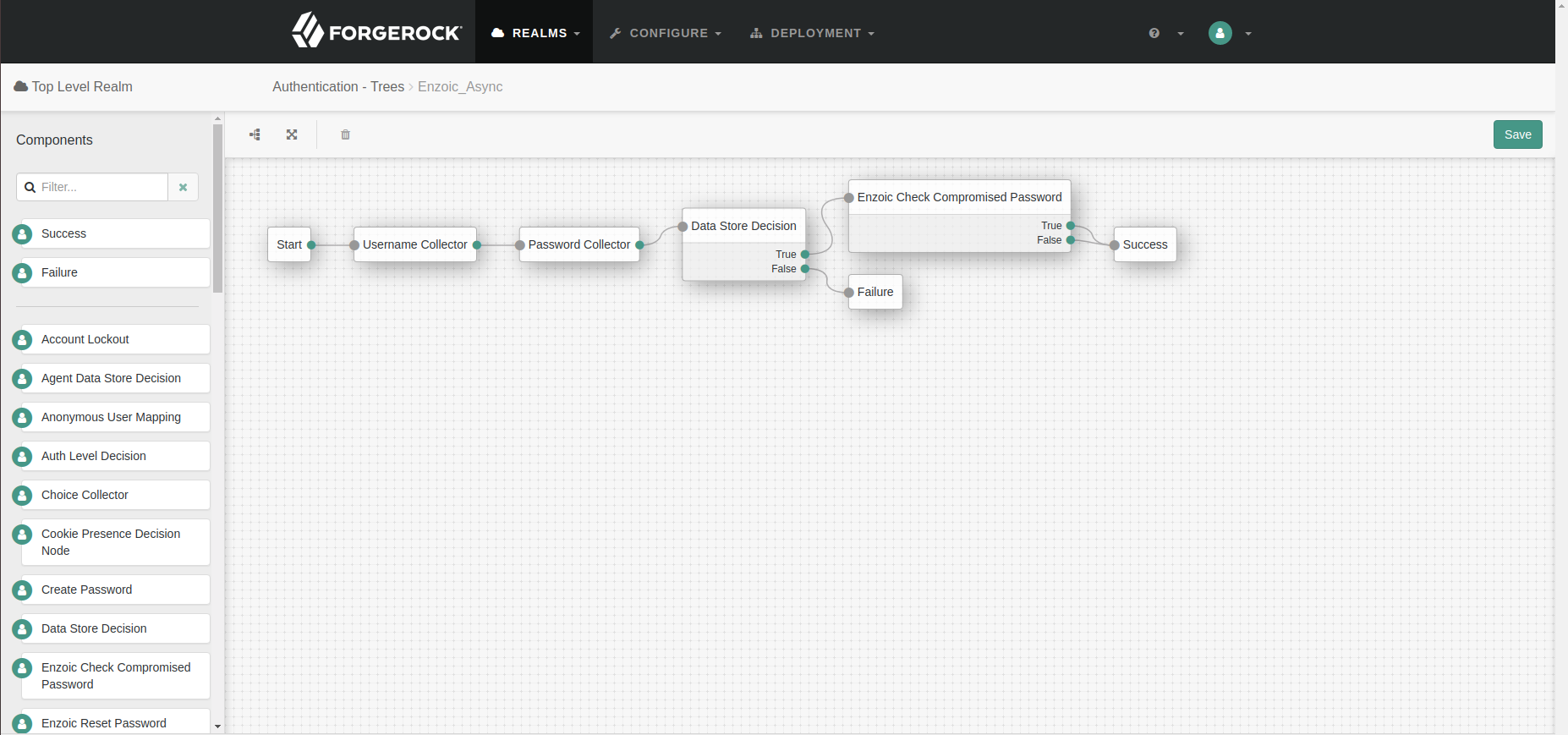
Enzoic Async Auth Tree : Enzoic Async Auth Tree will check password is compromised or not using Enzoic Password ping API and proceeds with login without waiting for response from Enzoic. If password is compromised then user attribute is updated as True and if not, User attribute is updated as False. The customer can check this attribute for future AuthN or AuthZ and configure the flow according to the value of this user attribute.
- Navigate to Realm > Authentication > Trees > Create Tree
The Enzoic Sync Auth Tree will check if the password is compromised using the Enzoic API. This tree then waits for a response from Enzoic before proceeding. If the password is compromised, the user will not able to login.
Configuration of Enzoic-Sync Auth Tree depicted below:
The Enzoic Async Auth Tree will check password is compromised using Enzoic API and proceeds with login without waiting for response. If the password is compromised then the user attribute is updated to True. If not, the user attribute is updated to False. The customer can check this attribute in future AuthN or AuthZ flows.
Configuration of Enzoic-Async Auth Tree depicted below: