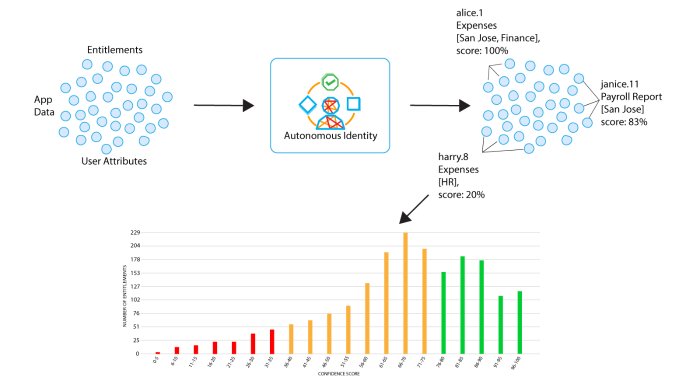
How Autonomous Identity Works
Autonomous Identity is an AI-based analytics engine that discovers, analyzes, and generates a complete profile of your company's entitlements.
Autonomous Identity looks at each entitlement and its relationship to the assigned user within the company. These relationships are modelled and assigned a single confidence score (from 0 to 100%) indicating the strength of correlation between the model and the assigned entitlement. The results are displayed on the UI console.
Figure 2: A simple conceptual diagram of Autonomous Identity
Let's Run a Simple Example
Let's run a simple example to see how Autonomous Identity models the entitlements and calculates confidence scores. Each company can decide the level and scope of the analysis. However, in most cases, the more data you analyze, the better the entitlement models.
Autonomous Identity processes the data in the following steps:
Data Ingestion
The process begins with data ingestion, where data is exported from application services, HR databases, and other sources and imported into Autonomous Identity using comma-separated values (.csv) formatted files. There are three general types of data files needed for analytics. Note that, in actual deployments, you set up seven data files consisting of HR data, entitlement data, application data and other mapping files to export to Autonomous Identity.
User Profile Data. Users profile data include those attributes that contain a subset of information from an HR system that is minimally required for entitlement analysis. Each user has a unique user ID and is represented in a single row within the file. Typically, the number of useful user profile attributes for successful modeling has been found to be between 7–15.
The following table shows a simple example of user profile data:
Table 1: User AttributesUSER ID CITY DEPT alice.1 San Jose Finance bob.2 San Jose Finance chris.3 San Jose Finance diane.4 San Jose HR ellen.5 San Jose HR fred.6 Austin HR gary.7 Austin HR harry.8 Austin HR irene.9 Dublin IT janice.10 Dublin Finance karen.11 San Jose Finance Entitlement Data. In another file, you import a list of entitlement data and any other descriptive information. The file may include information, such as full entitlement name, application name, entitlement or role owner, or any other information that helps with the machine learning.
The following table shows a simple example of entitlement data:
Table 2: Entitlement DataEntitlement APP_NAME APP_ID Payroll Report ADP adp-1 Expenses Expensify expensify-1 Access Data. The third type of data is a mapping file that connects the user to their assigned entitlement. The data can come from your IAM/IGA system. If a user has multiple entitlements, each row represents a single assigned mapping to each entitlement. Some examples could have user ID, entitlement name, flag if it is a high risk entitlement, another flag if the entitlement is assigned, and last usage.
The following table shows a simple example of user-to-entitlement data:
Table 3: User-to-Entitlement MappingUSR_KEY ENT HIGH_RISK LAST_USAGE alice.1 Payroll Report High 2020-06-06 17:11:07 alice.1 Expenses High 2020-06-06 17:11:07 bob.2 Payroll Report High 2020-06-06 17:11:07 bob.2 Expenses High 2020-06-06 17:11:07 chris.3 Payroll Report High 2020-06-06 17:11:07 chris.3 Expenses High 2020-06-06 17:11:07 diane.4 Payroll Report High 2020-06-06 17:11:07 ellen.5 Payroll Report High 2020-06-06 17:11:07 fred.6 Payroll Report High 2020-06-06 17:11:07 gary.7 Expenses High 2020-06-06 17:11:07 harry.8 Payroll Report High 2020-06-06 17:11:07 irene.9 Expenses High 2020-06-06 17:11:07 janice.10 Payroll Report High 2020-06-06 17:11:07 karen.11 Expenses High 2020-06-06 17:11:07
Training
Next, Autonomous Identity runs a two-stage training process to generate the association rules and confidence scores. An association rule is an IF-THEN rule that expresses patterns between random data variables in a large transaction set. For example, [San Jose, Finance] -> [Payroll Report] indicates that if a company's finance office is located in San Jose and a person works in that office and department, it is likely that they get access to the Payroll Report.
During stage one of the training, Autonomous Identity analyzes the user attribute data using machine learning algorithms to pattern-mine and create itemsets of rules. The frequency of occurrence is counted for each itemset. Only rules that appear three times or more are considered. Itemsets less than three are ignored.
Note
In a typical deployment, Autonomous Identity can create a million or more association rules for a company's dataset.
The following table shows the results of the initial training process:
| Itemset | Freq |
|---|---|
| [San Jose] | 6 |
| [Finance] | 5 |
| [HR] | 5 |
| [San Jose, Finance] | 4 |
| [Austin] | 3 |
| [Austin, HR] | 3 |
During this training run, the analytics engine creates a unique row in a table for each user and their assigned entitlements. In the example below, alice.1, bob.2, and chris.3 have multiple rows, one for each assigned entitlement. Again, only frequency sets (freqUnion) of three or more are considered.
The following table shows the results of the second training process:
| USER ID | CITY | DEPT | ENT |
|---|---|---|---|
| alice.1 | San Jose | Finance | Payroll Report |
| alice.1 | San Jose | Finance | Expenses |
| bob.2 | San Jose | Finance | Payroll Report |
| bob.2 | San Jose | Finance | Expenses |
| chris.3 | San Jose | Finance | Payroll Report |
| chris.3 | San Jose | Finance | Expenses |
| diane.4 | San Jose | HR | Payroll Report |
| ellen.5 | San Jose | HR | Payroll Report |
| fred.6 | Austin | HR | Payroll Report |
| gary.7 | Austin | HR | Expenses |
| harry.8 | Austin | HR | Payroll Report |
| irene.9 | Dublin | IT | Expenses |
| janice.10 | Dublin | Finance | Payroll Report |
| karen.11 | San Jose | Finance | Expenses |
Autonomous Identity applies the association rules to the entitlement mappings and calculates the risk confidence scores by dividing the freqUnion by frequency numbers (FreqUnion/Freq). The FREQ column show the number of occurrences of a rule from Table 5, for example, the rule [San Jose] appears 9 times. The FreqUnion is the union of a rule with an entitlement, for example, the union of the rule [San Jose] with the entitlement, Expenses, appears 4 times in Table 5. The confidence score indicates the scale from 0 to 100% to indicate the strength of each correlation. A confidence score of 100% indicates that the assigned entitlement is highly correlated to the user's job function. Only rules that appear three times or more are considered.
The following table shows the applied association rules:
| RULE | ENT | FREQ | FreqUnion | Confidence |
|---|---|---|---|---|
| [San Jose] | Payroll Report | 9 | 5 | 56% |
| [San Jose] | Expenses | 9 | 4 | 44% |
| [Finance] | Payroll Report | 8 | 4 | 50% |
| [Finance] | Expenses | 8 | 4 | 50% |
| [HR] | Payroll Report | 5 | 4 | 80% |
| [San Jose,Finance] | Payroll Report | 7 | 3 | 43% |
| [San Jose,Finance] | Expenses | 7 | 4 | 57% |
Next, Autonomous Identity must re-adjust the frequency numbers from the previous table as the occurrences of a rule are inflated due to multiple appearances of a user's entitlements (that is, one entitlement per row) as seen in Table 5. The re-adjustment provides a more accurate confidence score for each association rule.
The following are the results of the readjusted confidence scores:
| RULE | ENT | FREQ (Corrected) | FreqUnion | Confidence |
|---|---|---|---|---|
| [San Jose] | Payroll Report | 6 | 5 | 83% |
| [San Jose] | Expenses | 6 | 4 | 67% |
| [Finance] | Payroll Report | 5 | 4 | 80% |
| [Finance] | Expenses | 5 | 4 | 80% |
| [HR] | Payroll Report | 5 | 4 | 80% |
| [San Jose,Finance] | Payroll Report | 4 | 3 | 75% |
| [San Jose,Finance] | Expenses | 4 | 4 | 100% |
As-is Predictions
After the training process has determined the association rules for each entitlement, the analytics engine runs through an as-is predictions process, where user accesses are mapped to each entitlement using the association rules.
In the example, the user alice.1 has the following mapped entitlements, which are called justifications for their entitlement accesses.
The following table shows the results of the as-is-predictions process:
| USER ID | ENT | RULE | Confidence | FreqUnion |
|---|---|---|---|---|
| alice.1 | Payroll Report | [San Jose] | 83% | 5 |
| alice.1 | Payroll Report | [Finance] | 80% | 4 |
| alice.1 | Payroll Report | [San Jose, Finance] | 75% | 3 |
| alice.1 | Expenses | [San Jose] | 67% | 4 |
| alice.1 | Expenses | [Finance] | 80% | 4 |
| alice.1 | Expenses | [San Jose,Finance] | 100% | 4 |
The as-is predictions filter the justifications from the previous step using confidence score properties that are set in the configuration file. The maximum confidence score is set by the maxConf property. The minimum confidence score is set by the maxConf minus the pred_conf_window property, which is set to 5% in the configuration file by default. Thus, for this example, the maximum confidence and minimum confidence score filters for each entitlement is as follows:
The following table shows the result of the as-is-predictions:
| ENT | maxConf | Min |
|---|---|---|
| Payroll Report | 83% | 78% |
| Expenses | 100% | 95% |
Applying the filters in Table 9 to the mapped entitlements in Table 8, we get the following filtered assigned entitlements while discarding the rest. These filters are applied to all users in your analysis.
The following table shows the results for alice.1:
| USER ID | ENT | RULE | Confidence | FreqUnion |
|---|---|---|---|---|
| alice.1 | Payroll Report | [San Jose] | 83% | 5 |
| alice.1 | Payroll Report | [Finance] | 80% | 4 |
| alice.1 | Expenses | [San Jose, Finance] | 100% | 4 |
Finally, the highest freqUnion is used to find the users with a specific rule and entitlement access. All rules with the lower freqUnion values are filtered out to favor rules that apply to the largest number of employees within a company. This ensures that the most generalized rules are used for the analysis.
The following table shows the final as-is predictions for a user:
| USER ID | ENT | RULE | Confidence | FreqUnion |
|---|---|---|---|---|
| alice.1 | Payroll Report | [San Jose] | 83% | 5 |
| alice.1 | Expenses | [San Jose, Finance] | 100% | 4 |
Recommendations
The analytics process goes through a recommendations predictions process that takes the entitlement rules and identifies any users who should have access to the entitlement but do not. The analytics engine looks at each user's confidence score associated with the entitlement and if the confidence score exceeds a pre-configured threshold value, the recommendation are made for the user.
The process begins by assigning the entitlements to all users and removing already existing accesses. Autonomous Identity assigns the rules and confidence scores for these new assignments.
The following table shows the recommendations assigned to users who do not have a particular entitlement:
| USER ID | ENT | RULE | Confidence |
|---|---|---|---|
| diane.4 | Expenses | [San Jose] | 67% |
| ellen.5 | Expenses | [San Jose] | 67% |
| fred.6 | Expenses | [San Jose] | 67% |
| gary.7 | Payroll Report | [HR] | 80% |
| harry.8 | Expenses | [HR] | 20% |
| irene.9 | Payroll Report | no rule found | 0% |
| janice.10 | Expenses | [Finance] | 80% |
| janice.11 | Payroll Report | [San Jose] | 83% |
The analytics engine determines the rules and confidence scores that meet a threshold property, conf_thresh, which is set to 80% in the configuration file by default.
The following example shows the final recommendations:
| USER ID | ENT | RULE | Confidence |
|---|---|---|---|
| gary.7 | Payroll Report | [HR] | 80% |
| janice.10 | Expenses | [Finance] | 80% |
| janice.11 | Payroll Report | [San Jose] | 83% |
The results will be uploaded to the Cassandra database as a recommended new entitlement and appears on the UI console on the Recommendations screen.
Output to the UI Console
The final step of the process is for Autonomous Identity to display the confidence scores graphically on the UI as a distribution from low, medium, to high scores. The console lets you immediately identify the low confidence scores that could pose a potential security risk as well as the high confidence scores that can be automatically approved or certified. Autonomous Identity displays the attributes that justified each confidence score as well as other data to help you manage your entitlements.
You can run the analytics weekly or monthly to ensure near realtime assessment of your entitlements. This ensures that some entitlements can immediately be flagged if it goes stale and is no longer necessary.