Step up the authentication level
When you step up the authentication level for an AM session, the authorization is verified and then captured as part of the AM session, and the user agent is authorized to that authentication level for the duration of the AM session.
This page uses the policies you created in Decisions in the same domain and Decisions in different domains, adding an authorization policy with an environment condition to step up the authentication level. Except for the paths where noted, procedures for single domain and cross-domain are the same.
After the user agent redirects the user to AM, if the user is not already authenticated they are presented with a login page. If the user is already authenticated, or after they authenticate, they are presented with a second page asking for an OTP verification code to step up the authentication level. You need a mobile device such as a phone to generate the OTP code.
Update AM settings
Before you start, set up one of the examples in Decisions in the same domain or Decisions in different domains.
-
In the AM admin UI, add a tree to step up authentication.
-
Select Authentication > Trees > + Create Tree.
-
Name the new tree
StepUpAuthentication. -
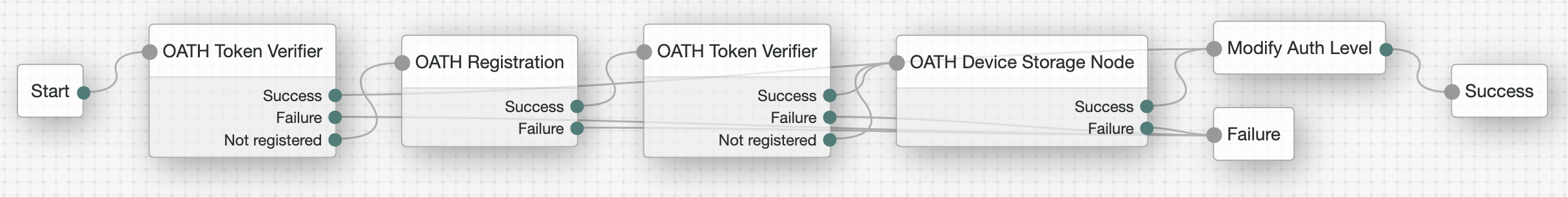
Add nodes to the tree as in the following image:
-
The OATH Token Verifier node has the default settings.
It validates the user’s OTP verification code or leads the unregistered user to register an OTP generator application.
-
The OATH Registration node registers an OTP generator application for the user.
-
The second OATH Token Verifier node verifies an initial OTP after registration.
-
The OATH Device Storage node stores the OTP generator application setting in the user’s profile.
-
Update the Modify Auth Level node to set Value to Add:
1, raising the authentication level.
-
-
Click Save.
-
-
Update the policy to use the new authentication tree.
-
Select a policy set:
-
For SSO, select Authorization > Policy Sets > PEP-SSO.
-
For CDSSO, select Authorization > Policy Sets > PEP-CDSSO.
-
-
In the policy, select Environments and add the following environment condition:
-
All of -
Type :
Authentication by Service -
Authenticate to Service :
StepUpAuthentication
-
-
Click and Save Changes.
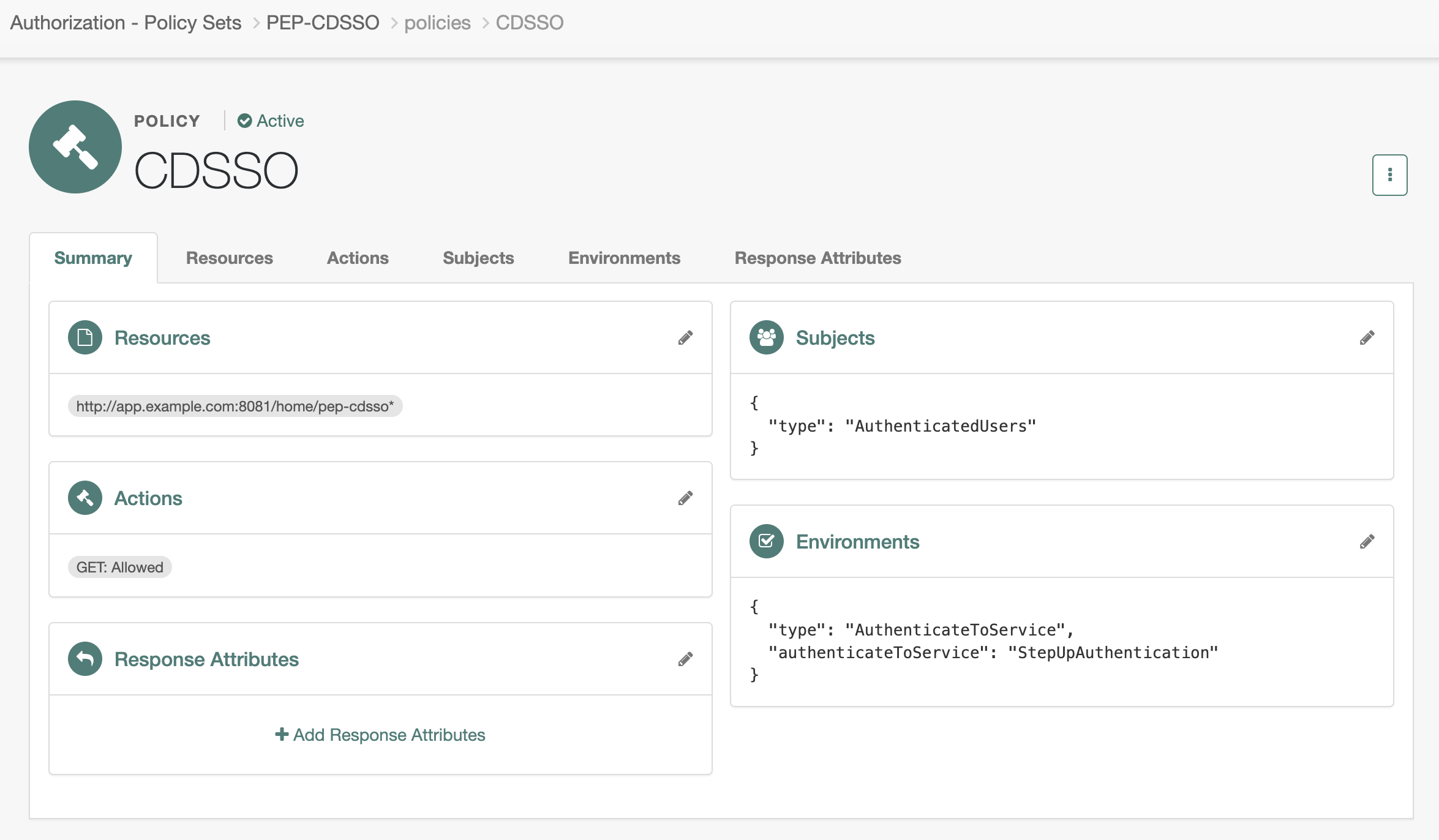
The summary of the policy looks similar to the following image:
-
Validation
-
In your browser’s privacy or incognito mode, go to the appropriate URL:
-
For SSO, go to https://ig.example.com:8443/home/pep-sso.
-
For CDSSO, go to https://ig.ext.com:8443/home/pep-cdsso.
-
-
Log in to AM as user
demo, passwordCh4ng31t.AM creates a session with the default authentication level
0, and PingGateway requests a policy decision.The updated policy requires authentication level
1, which is higher than the AM session’s current authentication level. AM issues a redirect with aAuthenticateToServiceConditionAdviceto authenticate at level1. -
If you haven’t registered an OTP generator application, follow the instructions in your browser to register one.
-
Enter the OTP verification code from the application you registered on your device.
AM upgrades the authentication level for the session to 1, and grants access to the sample application. If you try to access the sample application again in the same session, you don’t need to provide the verification code.