/json/users/{user}/uma/pendingrequests
AM-specific endpoint used to list, approve, or deny pending authorization requests on a resource.
| Action | HTTP Method |
|---|---|
| Approve,Approve All | POST |
| Deny, Deny All | POST |
| Query | GET |
Tip
Use the AM API Explorer for detailed information about this endpoint, and to test it against your deployed AM instance.
In the AM console, click the Help icon, and then go to API Explorer > users > {user} > uma > pendingrequests.
You must compose the path to the token endpoint addressing the specific realm where the token will be issued. For example, https://openam.example.com:8443/openam/json/realms/root/realms/subrealm1/users/{user}/oauth2/resources/labels.
To authenticate to the endpoint, send the SSO token of the resource owner as the value of the iplanetDirectoryPro header.
The endpoint supports the following actions:
- approve
Approves the permission request specified in the endpoint's URL. It does not grant the permission requested. Instead, it grants the scopes sent as a JSON document in the body of the
approvecall. For example:$
curl \ --request POST --header "iPlanetDirectoryPro: AQIC5wM2LY4S...Q4MTE4NTA2*" \ --header "Accept-API-Version: resource=1.0" \ --data { "scopes": [ "comment" ] } \ https://openam.example.com:8443/openam/json/realms/root/users/demo/uma/pendingrequests/0d7790de-9066-4bb6-8e81-25b6f9d0b8853?_action=approve- approveAll
Approves every pending permission request for the user, but does not grant the permissions requested. Instead, it grants the scopes sent as a JSON document in the body of the
approveAllcall. For example:$
curl \ --request POST --header "iPlanetDirectoryPro: AQIC5wM2LY4S...Q4MTE4NTA2*" \ --header "Accept-API-Version: resource=1.0" \ --data { "scopes": [ "comment" ] } \ https://openam.example.com:8443/openam/json/realms/root/users/demo/uma/pendingrequests?_action=approveAll- deny
Denies the permission request specified in the endpoint's URL. For example:
$
curl \ --request POST --header "iPlanetDirectoryPro: AQIC5wM2LY4S...Q4MTE4NTA2*" \ --header "Accept-API-Version: resource=1.0" \ https://openam.example.com:8443/openam/json/realms/root/users/demo/uma/pendingrequests/0d7790de-9066-4bb6-8e81-25b6f9d0b8853?_action=deny- denyAll
Denies every pending permission request for the user. For example:
$
curl \ --request POST --header "iPlanetDirectoryPro: AQIC5wM2LY4S...Q4MTE4NTA2*" \ --header "Accept-API-Version: resource=1.0" \ https://openam.example.com:8443/openam/json/realms/root/users/demo/uma/pendingrequests?_action=denyAll
AM returns an HTTP 200 message with an empty body if the request is successful, and an HTTP 500 message if not.
The endpoint also supports the _queryFilter parameter to request a list of pending permission requests for the user. Specify true to match every request, false to mach no request. For example:
$curl \ --request GET --header "iPlanetDirectoryPro: AQIC5wM2LY4S...Q4MTE4NTA2*" \ --header "Accept-API-Version: resource=1.0" \ https://openam.example.com:8443/openam/json/realms/root/users/demo/uma/pendingrequests?_queryFilter=true{ "result": [ { "_id": "0d3190ef-6901-654b-82pa-13a6h9d0b53452", "user": "bob", "resource": "My Resource Name", "when": 1607002810, "permissions": [ "download" ] } ], "resultCount": 1, "pagedResultsCookie": "10d7790de", "totalPagedResultsPolicy": "EXACT", "totalPagedResults": 0, "remainingPagedResults": 0 }
AM also provides built-in user pages in the UI to view pending resource access requests:
AM supports an UMA workflow in which a user can request access to a resource that has not been explicitly shared with them. The resource owner receives a notification of the request and can choose to allow or deny access.
Manage pending requests for access to resources by using the steps below:
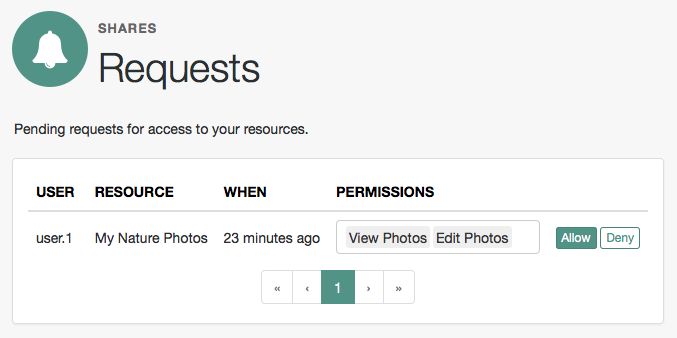
Log in to AM as the resource owner, and then go to Shares > Requests.
The Requests page is displayed:
Review the pending request, and take one of the following actions:
Click Allow to approve the request.
Tip
You can remove permissions from the request by clicking the permission, then press either Delete or Backspace. Select the permission from the drop-down list to return it to the permissions granted to the resource owner.
The required UMA policy will be created, and optionally, the requesting party will be notified that they can now access the resource.
The requesting party can view a list of resources to which they have access by navigating to Shares > Resources > Shared with me.
Click Deny to prevent the requesting party from accessing the resource. The pending request is removed, and the requesting party will not be notified.
After allowing or denying access to a resource, an entry is created in the History page.
To view a list of actions that have occurred, go to Shares > History.