Certificate Validation node
Validates a digital X.509 certificate collected by the Certificate Collector node.
Compatibility
| Product | Compatible? |
|---|---|
ForgeRock Identity Cloud |
|
ForgeRock Access Management (self-managed) |
|
ForgeRock Identity Platform (self-managed) |
Outcomes
True-
The node could validate the certificate.
When the outcome is
True, add a Certificate User Extractor node to extract the values of the certificate. False-
The node could not validate the certificate. The node will use this path when it cannot validate the certificate, and no more specific outcome is available.
Not found-
The Match Certificate in LDAP property is enabled, but the certificate was not found in the LDAP store.
Expired-
The Check Certificate Expiration property is enabled, and the certificate has expired.
Path Validation Failed-
The Match Certificate to CRL property is enabled, and the certificate path is invalid.
Revoked-
The OCSP Validation property is enabled, and the certificate has been revoked.
Properties
| Property | Usage |
|---|---|
Match Certificate in LDAP |
When enabled, AM matches the certificate collected with the one stored in an LDAP directory entry. This entry and additional security-related properties are defined later in the node. Default: Disabled |
Check Certificate Expiration |
When enabled, AM checks whether the certificate has expired. Default: Disabled |
Subject DN Attribute Used to Search LDAP for Certificates |
Specifies the attribute that AM uses to search the LDAP directory for the certificate. The search filter also uses the value of the Subject DN as it appears in the certificate. Default: |
Match Certificate to CRL |
When enabled, AM checks whether the certificate has been revoked according to a CRL in the LDAP directory. Related properties are defined later in the node. Default: Disabled. |
Issuer DN Attribute(s) Used to Search LDAP for CRLs |
Specifies which attribute and value in the certificate Issuer DN AM uses to find the CRL in the LDAP directory. If only one attribute is specified, the LDAP search filter used is For example, if the subject DN of the issuer certificate is Specify several CLRs for the same CA issuer in a comma-separated list (,) where the names are in the same order as they occur in the subject DN. In this case, the LDAP search filter used
is For example, if the subject DN of the issuer certificate is Default: |
HTTP Parameters for CRL Update |
Specifies parameters that AM includes in any HTTP CRL call to the CA that issued the certificate. If the client or CA contains the Issuing Distribution Point Extension, AM uses this information to retrieve the CRL from the distribution point. Add the parameters as key pairs of values in a comma-separated list (,).
For example, |
Cache CRLs in Memory |
(LDAP distribution points only) When enabled, AM caches CRLs. Default: Enabled |
Update CA CRLs from CRLDistributionPoint |
When enabled, AM updates the CRLs stored in the LDAP directory store
if the CA certificate includes either the Default: Enabled |
OCSP Validation |
When enabled, AM checks the revocation status of certificates using the Online Certificate Status Protocol (OCSP). The AM instance must have internet access, and you must configure OSCP for AM under Configure > Server Defaults > Security > Online Certificate Status Protocol Check. Default: Disabled |
LDAP Server Where Certificates are Stored |
Specifies the LDAP server that holds the certificates.
Enter each server in the AM servers can be associated with LDAP servers by writing multiple chains
with the format To configure a secure connection, enable the Use SSL/TLS for LDAP Access property. |
LDAP Search Start or Base DN |
Valid base DN for the LDAP search, such as |
LDAP Server Authentication User |
Specifies the DN of the service account that AM uses
to authenticate to the LDAP directory that holds the certificates.
For example, Default: |
LDAP Server Authentication Password |
Specifies the password of the user configured in the LDAP Server Authentication User property. |
Use SSL/TLS for LDAP Access |
Specifies whether AM should use SSL/TLS to access the LDAP. When enabled, AM must be able to trust the LDAP server certificate. Default: Disabled |
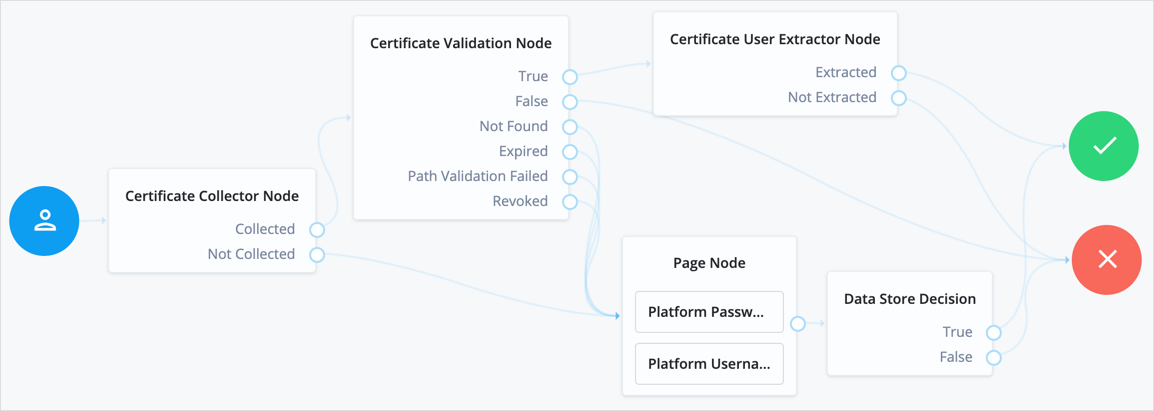
Example
The following is an example of how to use the certificate nodes in a ForgeRock Identity Platform authentication journey. Note that all the failure outcomes of the Certificate Validation node are linked so that the user provides a username and password, but you could choose different authentication methods for each outcome: