Deploy a Lightweight Autonomous Identity
Autonomous Identity supports a flexible and scalable microservices architecture that you can deploy in any type of network environment: on-prem, cloud, multi-cloud, or hybrid cloud.
The deployment process is simple. Autonomous Identity provides a deployer script that you launch on a local server or laptop. The deployer pulls down the necessary images from the ForgeRock Google Cloud Repository (gcr.io) to install Autonomous Identity on the target node. From there, you run a few commands to complete the installation.
Important
To download the deployer, you must obtain a registry key to access the ForgeRock Google Cloud Repository. Only ForgeRock Autonomous Identity customers can obtain a registry key. For more information, contact ForgeRock.
For this example, we install a lightweight version of Autonomous Identity in a two-core 8GB virtual machine on a cloud platform, such as Google Cloud Platform (GCP), Amazon Web Services (AWS), Microsoft Azure, or others. The deployment includes the Docker-based microservices component and Apache Cassandra, but not Apache Spark. From there, you populate demo data by importing it into Cassandra and then display it on the Autonomous Identity UI console. This setup provides a way to deploy a system quickly for demonstration purposes.
This installation assumes that you set up the deployer script on a separate machine from the target. This lets you launch a build from a laptop or local server.
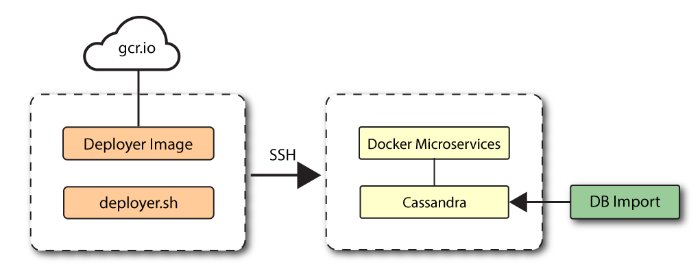
A simple diagram is shown below:
Figure 1: A lightweight single-node target deployment.
Important
This example setup is only for development or evaluation purposes and should not be used for production deployments.
Let's set up Autonomous Identity on CentOS 7. The following are some prerequisites:
Operating System. The target machine requires CentOS 7. The deployer machine can use any operating system as long as Docker is installed. For this guide, we use CentOS 7 as its base operating system.
Memory Requirements. Make sure you have enough free disk space on the deployer machine before running the
deployer.shcommands. We recommend at least a 40GB/partition with 14GB used and 27GB free after running the commands.Registry Requirements. Autonomous Identity provides a Docker image that creates a
deployer.shscript. The script downloads additional images necessary for the installation. To download the deployment images, you must first obtain a registry key to log into the ForgeRock Google Cloud Registry (gcr.io). The registry key is only available to ForgeRock Autonomous Identity customers. For specific instructions on obtaining the registry key, see How To Configure Service Credentials (Push Auth, Docker) in Backstage.
Set Up the Target Machine
The install assumes that you have CentOS 7 as your operating system. Check your CentOS 7 version.
$
sudo cat /etc/centos-releaseSet the user for the target machine to a username of your choice. For example,
autoid.#
sudo adduser autoidSet the password for the user you created in the previous step.
$
sudo passwd autoidConfigure the user for passwordless sudo.
$
echo "autoid ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/autoidAdd administrator privileges to the user.
$
sudo usermod -aG wheel autoidChange to the user account.
$
su - autoidInstall yum-utils package on the deployer machine. yum-utils is a utilities manager for the Yum RPM package repository. The repository compresses software packages for Linux distributions.
$
sudo yum install -y yum-utilsCreate the installation directory. Note that you can use any install directory for your system as long as your run the deployer.sh script from there. Also, the disk volume where you have the install directory must have at least 8GB free space for the installation.
$
mkdir ~/autoid-config
Set Up the Deployer Machine
Set up another machine as a deployer node. You can use any OS-based machine for the deployer as long as it has Docker installed. For this example, we use CentOS 7.
The install assumes that you have CentOS 7 as your operating system. Check your CentOS 7 version.
$
sudo cat /etc/centos-releaseSet the user for the target machine to a username of your choice. For example,
autoid.#
sudo adduser autoidSet the user password for the user you created in the previous step.
$
sudo passwd autoidConfigure the user for passwordless sudo. Replace "autoid" with the username for your system.
$
echo "autoid ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/autoidAdd administrator privileges to the user.
$
sudo usermod -aG wheel autoidChange to the user account.
$
su - autoidInstall yum-utils package on the deployer machine. yum-utils is a utilities manager for the Yum RPM package repository. The repository compresses software packages for Linux distributions.
$
sudo yum install -y yum-utilsCreate the installation directory. Note that you can use any install directory for your system as long as your run the deployer.sh script from there. Also, the disk volume where you have the install directory must have at least 8GB free space for the installation.
$
mkdir ~/autoid-config
Install Docker on the Deployer Machine
Install Docker on the deployer machine. We run commands from this machine to install Autonomous Identity on the target machine. In this example, we use CentOS 7.
On the target machine, set up the Docker-CE repository.
$
sudo yum-config-manager \ --add-repo https://download.docker.com/linux/centos/docker-ce.repoInstall the latest version of the Docker CE, the command-line interface, and containerd.io, a containerized website.
$
sudo yum install -y docker-ce docker-ce-cli containerd.ioEnable Docker to start at boot.
$
sudo systemctl enable dockerStart Docker.
$
sudo systemctl start dockerCheck that Docker is running.
$
systemctl status dockerAdd the user to the Docker group.
$
sudo usermod -aG docker ${USER}
Set Up SSH on the Deployer
On the deployer machine, run ssh-keygen to generate an RSA keypair, and then click Enter. You can use the default filename. Enter a password for protecting your private key.
$
ssh-keygen -t rsa -C "autoid"The public and private rsa key pair is stored in
home-directory/.ssh/id_rsaandhome-directory/.ssh/id_rsa.pub.Copy the SSH key to the
autoid-configdirectory.$
cp ~/.ssh/id_rsa ~/autoid-configChange the privileges to the file.
$
chmod 400 ~/autoid-config/id_rsaCopy your public SSH key,
id_rsa.pub, to the target machine's~/.ssh/authorized_keysfile. If your system does not have an/authorized_keysdirectory, create it using mkdir -p ~/.ssh/authorized_keys.On the target machine, set the privileges on your
~/.sshand~/.ssh/authorized_keys.$
chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keysOn the deployer machine, test your SSH connection to the target machine. This is a critical step. Make sure the connection works before proceeding with the installation.
$
ssh -i ~/.ssh/id_rsa autoid@34.70.190.144Last login: Sun Jun 14 23:23:36 2020 from 74.125.45.78If you successfully accessed the remote server, enter exit to end your SSH session.
Install Autonomous Identity
On the deployer machine, change to the installation directory.
$
cd ~/autoid-config/Log in to the ForgeRock Google Cloud Registry (gcr.io) using the registry key. The registry key is only available to ForgeRock Autonomous Identity customers. For specific instructions on obtaining the registry key, see How To Configure Service Credentials (Push Auth, Docker) in Backstage.
$
docker login -u _json_key -p "$(cat autoid_registry_key.json)" https://gcr.io/forgerock-autoidRun the create-template command to generate the
deployer.shwrapper. Note that the command sets the configuration directory on the target node to/config. The --user parameter eliminates the need to use sudo while editing the hosts file and other configuration files.$
docker run --user=`id -u` -v ~/autoid-config:/config -it gcr.io/forgerock-autoid/deployer:2020.6.2 create-templateMake the script executable.
$
chmod +x deployer.shThe create-template command creates a number of configuration files, including
ansible.cfg. Open a text editor and edit theansible.cfgto set up the remote user and SSH private key file location on the target node. Make sure that the remote_user exists on the target node.[defaults] host_key_checking = False remote_user = autoid private_key_file = id_rsaOpen a text editor and enter the target host's public IP addresses in the
~/autoid-config/hostsfile. Make sure to keep the Spark server entries blank as Spark is excluded from the deployment. The following is an example of the~/autoid-config/hostsfile:[docker-managers] 35.232.107.121 [docker-workers] 35.232.107.121 [docker:children] docker-managers docker-workers [cassandra-seeds] 35.232.107.121 [cassandra-workers] 35.232.107.121 [spark-master] [spark-workers] [analytics]If your external IP and internal IP addresses are different, for example, when deploying the target host in a cloud, define a mapping between the external IP address and the private IP address.
On the deployer node, add the
private_ip_address_mappingproperty in the~/autoid-config/vars.ymlfile. You can look up the private IP on the cloud console, or run sudo ifconfig on the target host. Make sure the values are within double quotes. The key should not be in double quotes and should have two spaces preceding the IP address.private_ip_address_mapping: external_ip: "internal_ip"For example:
private_ip_address_mapping: 34.72.28.214: "10.128.0.52"Open a text editor to see the Autonomous Identity passwords, located at
~/autoid-config/vault.yml.configuration_service_vault: basic_auth_password: Welcome123 openldap_vault: openldap_password: Welcome123 cassandra_vault: cassandra_password: Welcome123 cassandra_admin_password: Welcome123Encrypt the vault file that stores the Autonomous Identity passwords, located at
~/autoid-config/vault.yml. Make note of the vault password. You will be asked to enter it when running the encrypt-vault command.$
./deployer.sh encrypt-vaultThe encrypted passwords are saved to
/config/.autoid_vault_password. The/config/mount is internal to the deployer container.Download the images. This step downloads software dependencies needed for the deployment.
$
./deployer.sh download-imagesRun the deployer. This step builds the Docker microservices and Cassandra servers.
$
./deployer.sh run
Hostname Resolution
On the target machine, open a text editor and add an entry in the
/etc/hostsfile for the Autonomous Identity self-service and UI services.For example:
34.70.190.144 autoid-ui.forgerock.com autoid-selfservice.forgerock.com
Check the System
Open a browser, and point it to
https://autoid-ui.forgerock.com/.Log in as a test user:
bob.rodgers@forgerock.com. Enter the password for the user. On the Autonomous Identity UI console, notice that there is no data on the system yet. Logout when done.Check the status of Apache Cassandra.
$
/opt/autoid/apache-cassandra-3.11.2/bin/nodetool statusDatacenter: datacenter1 ======================= Status=Up/Down |/ State=Normal/Leaving/Joining/Moving -- Address Load Tokens Owns (effective) Host ID Rack UN 10.128.0.6 624.21 KiB 256 100.0% 0a13aa7f-ea2e-43b2-9323-136bdec915d2 rack1Enter exit to end your SSH session.
Set Up dbutils
On the deployer machine, run the install-dbutils command. This command creates a
dbutilsdirectory in the target instance's Cassandra seed node.$
./deployer.sh install-dbutils
Import the Demo Data
If you are setting up a fresh install using the demo data provided by ForgeRock, follow these steps.
Contact ForgeRock to obtain the demo data.
On the target machine, change to the
dbutilsdirectory.$
cd /opt/autoid/dbutilsUse the dbutils.py import command to populate the Autonomous Identity keyspace with the demo data.
$
python dbutils.py import /import-dirFor example:
$
python dbutils.py import ~/import/AutoID-dataOpen a browser, and point it to
https://autoid-ui.forgerock.com/.Log in as a test user:
bob.rodgers@forgerock.com. Enter the password for the user:Welcome123. You should see data populated on the Autonomous Identity UI.