Identity Cloud guide
ForgeRock® Identity Platform serves as the basis for our simple and comprehensive Identity and Access Management solution. We help our customers deepen their relationships with their customers, and improve the productivity and connectivity of their employees and partners. For more information about ForgeRock and about the platform, see https://www.forgerock.com.
This guide is for ForgeRock Identity Cloud evaluators, administrators, and architects. It provides examples of how to integrate your business application and APIs with Identity Cloud for Single Sign-On and API Security, with ForgeRock Identity Gateway.
Example installation for this guide
Unless otherwise stated, the examples in this guide assume the following installation:
-
Identity Gateway installed on
http://ig.example.com:8080, as described in Download and start IG. -
Sample application installed on
http://app.example.com:8081, as described in Using the sample application. -
The ForgeRock Identity Cloud, with the default configuration, as described in the ForgeRock Identity Cloud Docs.
When you are using the ForgeRock Identity Cloud, you need to know the value of the following properties:
-
The root URL of your ForgeRock Identity Cloud. For example,
https://myTenant.forgeblocks.com.The URL of the Access Management component of the ForgeRock Identity Cloud is the root URL of your Identity Cloud followed by
/am. For example,https://myTenant.forgeblocks.com/am. -
The realm where you work. The examples in this document use
alpha.Prefix each realm in the hierarchy with the
realmskeyword. For example,/realms/root/realms/alpha.
If you use a different configuration, substitute in the procedures accordingly.
Authenticate an IG agent to Identity Cloud
|
IG agents are automatically authenticated to Identity Cloud by a non-configurable authentication module. Authentication chains and modules are deprecated in Identity Cloud and replaced by journeys. You can now authenticate IG agents to Identity Cloud with a journey. The procedure is currently optional, but will be required when authentication chains and modules are removed in a future release of Identity Cloud. For more information, refer to Identity Cloud’s Journeys. |
This section describes how to create a journey to authenticate an IG agent to Identity Cloud. The journey has the following requirements:
-
It must be called
Agent -
Its nodes must pass the agent credentials to the Agent Data Store Decision node.
When you define a journey in Identity Cloud, that same journey is used for all instances of IG, Java agent, and Web agent. Consider this point if you change the journey configuration.
-
Log in to the Identity Cloud admin UI as an administrator.
-
Click Journeys > New Journey.
-
Add a journey with the following information and click Create journey:
-
Name:
Agent -
Identity Object: The user or device to authenticate.
-
(Optional) Description: Authenticate an IG agent to Identity Cloud
The journey designer is displayed, with the
Startentry point connected to theFailureexit point, and aSuccessnode. -
-
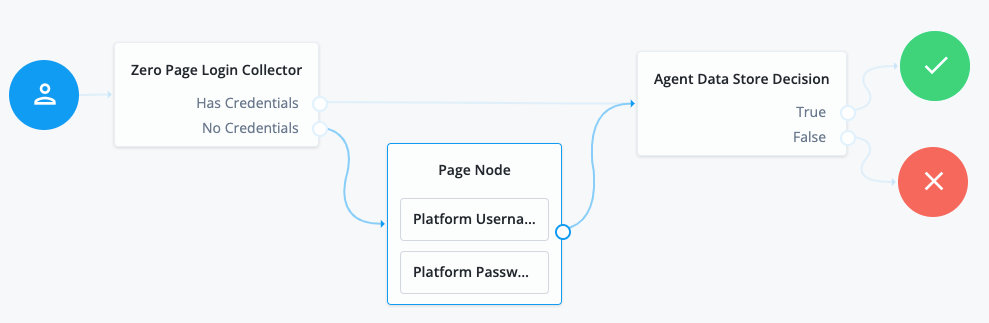
Using the Filter nodes bar, find and then drag the following nodes from the Components panel into the designer area:
-
Zero Page Login Collector node to check whether the agent credentials are provided in the incoming authentication request, and use their values in the following nodes.
This node is required for compatibility with Java agent and Web agent.
-
Page node to collect the agent credentials if they are not provided in the incoming authentication request, and use their values in the following nodes.
-
Agent Data Store Decision node to verify the agent credentials match the registered IG agent profile.
Many nodes can be configured in the panel on the right side of the page. Unless otherwise stated, do not configure the nodes, and use only the default values. -
-
Drag the following nodes from the Components panel into the Page node:
-
Platform Username node to prompt the user to enter their username.
-
Platform Password node to prompt the user to enter their password.
-
-
Connect the nodes as follows and save the journey:
Register an IG agent in Identity Cloud
This procedure registers an agent that acts on behalf of IG.
-
Log in to the Identity Cloud admin UI as an administrator.
-
Click verified_user Gateways & Agents > New Gateway/Agent > Identity Gateway > Next, and add an agent profile:
-
ID: agent-name
-
Password: agent-password
Use secure passwords in a production environment. Consider using a password manager to generate secure passwords.
-
-
Click Save Profile > Done. The agent profile page is displayed.
-
To add a redirect URL for CDSSO, go to the agent profile page and add the URL.
-
To change the introspection scope, click open_in_new Native Consoles > Access Management, and update the agent in the AM admin UI. By default, the agent can introspect OAuth 2.0 tokens issued to any client, in the realm and subrealm where it is created.
Set up a demo user in Identity Cloud
This procedure sets up a demo user in the alpha realm.
-
Log in to the Identity Cloud admin UI as an administrator.
-
Go to group Identities > Manage > settings_system_daydream Alpha realm - Users, and add a user with the following values:
-
Username:
demo -
First name:
demo -
Last name:
user -
Email Address:
demo@example.com -
Password:
Ch4ng3!t
-