Configuring AM's Container for HTTPS
There are many ways to deploy and configure your environment for AM, but we recommend that you enforce HTTPS connections to AM. For more information about securing AM, see the Security Guide.
The container where AM runs requires a certificate in order to set up secure connections. You can install CA-signed or self-signed certificates in the container where AM runs. Remember that you must configure your applications to trust your self-signed certificates.
The following is an example about how to configure Apache Tomcat for HTTPS:
There are several ways of completing the tasks ahead, and it is beyond the scope of this document to explore them all. If this procedure does not suit your environment, refer to your CA vendor documentation, the keytool command documentation, or Java container documentation for more information.
Stop Apache Tomcat.
Ensure you have a keystore containing the appropriate certificates:
(Optional) If you have CA certificates, import them in a new keystore using the keytool command. For example, if you have root, intermediate, and primary certificates, import them in the same keystore you used when generating your certificate signing request (CSR):
$
keytool -importcert -alias root -file myrootCA.cert \ -keystore /path/to/tomcat_keystore.pfx -storetype PKCS12$keytool -importcert -alias intermediate -file myintCA.cert \ -keystore /path/to/tomcat_keystore.pfx -storetype PKCS12$keytool -importcert -alias mysite.example.com -file mypriCA.cert \ -keystore /path/to/tomcat_keystore.pfx -storetype PKCS12If you need a self-signed certificate, create a new self-signed key pair with the keytool command. For example:
$
cd /path/to/tomcat/conf/$keytool -genkey -alias openam.example.com -storetype PKCS12 -keyalg RSA -validity 730 \ -keysize 2048 -keystore tomcat_keystore.pfx -dname 'CN=openam.example.com' -ext 'san=dns:openam.example.com'
Create an SSL connector configuration in Apache Tomcat's
conf/server.xmlconfiguration file, and specify your keystore file, type, and password.Note that there are different types of SSL connectors, and that implementation details may change across Tomcat versions. This example creates a JSSE connector in Tomcat as provided as part of the Java runtime:
<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="200" SSLEnabled="true" scheme="https" secure="true" keystoreFile="/path/to/tomcat_keystore.pfx" keystoreType="PKCS12" keystorePass="keystore_password" clientAuth="false" sslProtocol="TLS" />You may need different settings depending on your configuration and version of Apache Tomcat. See the documentation for your version for more information.
Start Tomcat.
Verify that you can connect to Apache Tomcat on port 8443 over HTTPS.
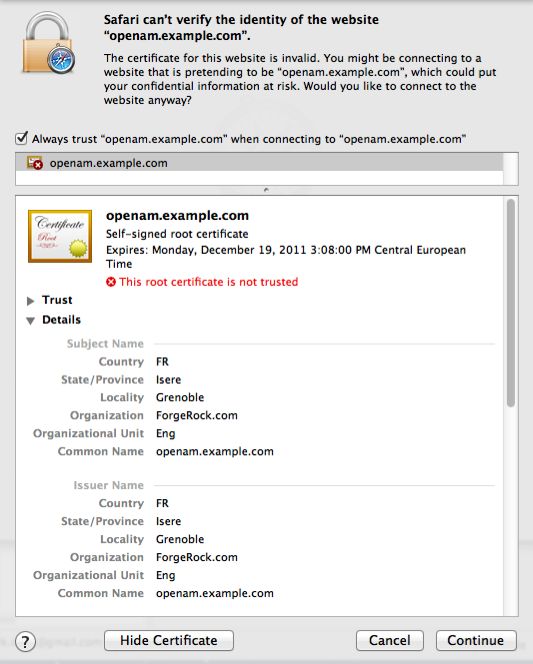
If you used self-signed certificates, your browser would not trust the certificate, because the certificate is self-signed and not signed by any of the CAs stored in your browser.
If you recognize the subject and issuer of your certificate, and so can choose to trust the certificate, save it into your browser's trust store.
Deploy and configure AM.
(Optional) To share the self-signed certificate in your container with other applications or servers, see "To Share Self-Signed Certificates".
[1] Alternatively, you can specify the trust store for a Java application, such as -Djavax.net.ssl.trustStore=/path/to/truststore.jks -Djavax.net.ssl.trustStorePassword=changeit.