About the Autonomous Identity API
Autonomous Identity provides a RESTful application programming interface (API) that lets you use HTTP request methods (GET, PUT, and POST) to interact with the system and its components. The API lets a developer make requests to send or receive data to an Autonomous Identity endpoint, a point where the API communicates with the system. The data that is sent or returned is in JavaScript Object Notation (JSON) format.
Autonomous Identity provides a Swagger client that you can access on the console.
Using Swagger
The Autonomous Identity installs with a Swagger client that lets you interact with the Autonomous Identity API and the configuration service API. Swagger is a popular software that provides design, build, test, and documentation tools for RESTful APIs.
-
Open a browser, and point it to
https://autoid-ui.forgerock.com/. Log in to the Autonomous Identity console. -
Open another browser tab, and point to
https://autoid-ui.forgerock.com/swagger/. You should see a default Swagger API page. -
Open another browser tab, and point to
https://autoid-ui.forgerock.com/api/swagger. You should see a raw text version of the API. -
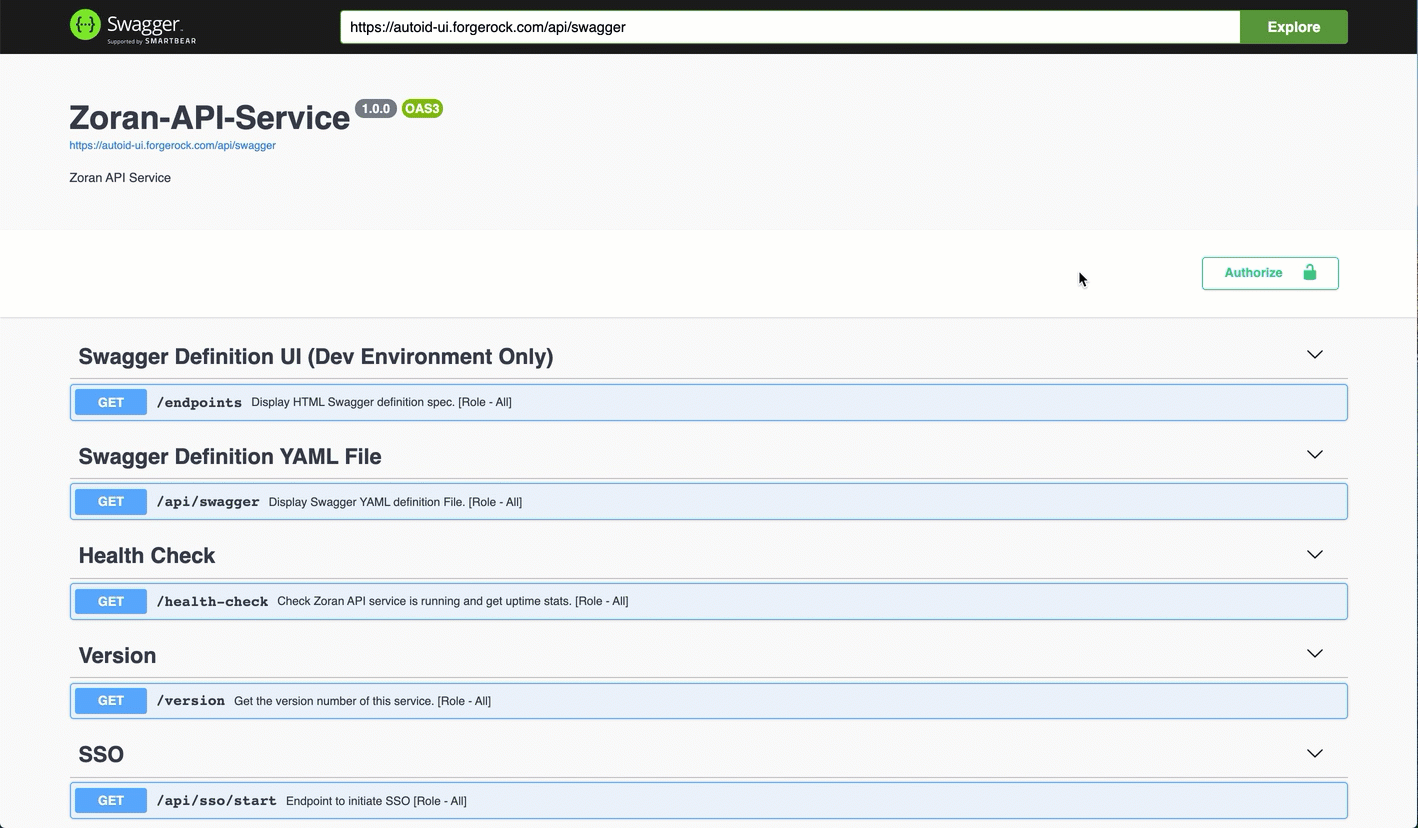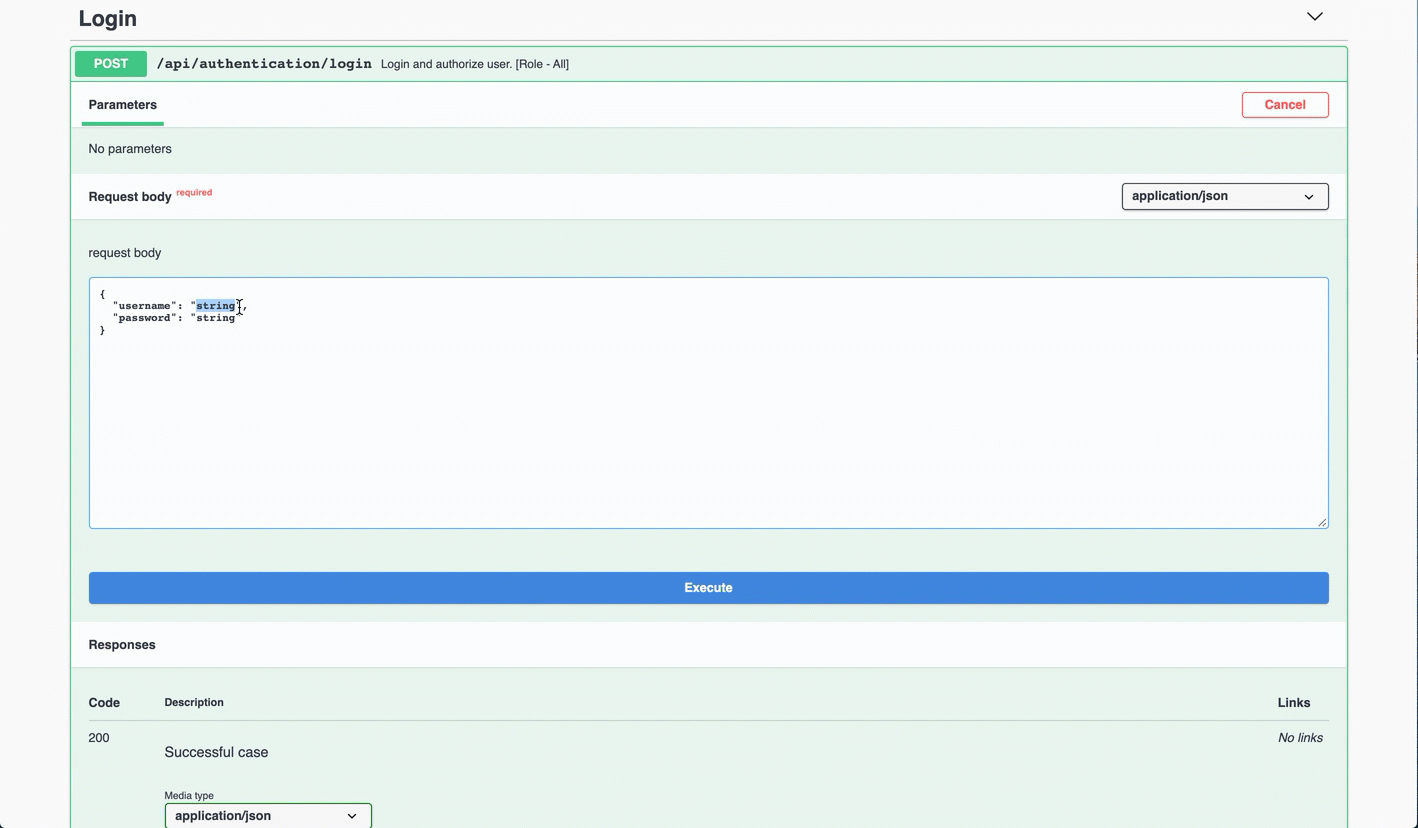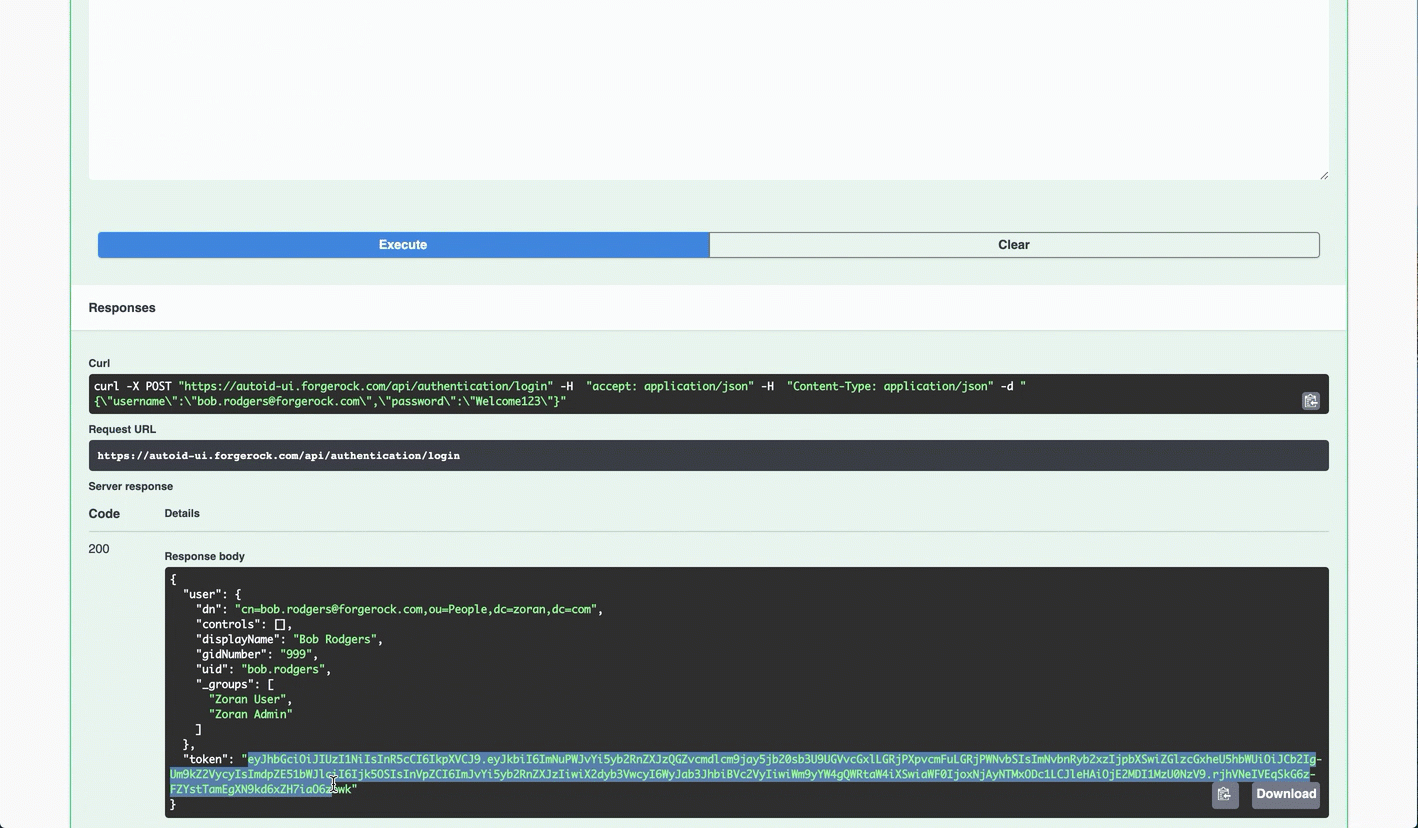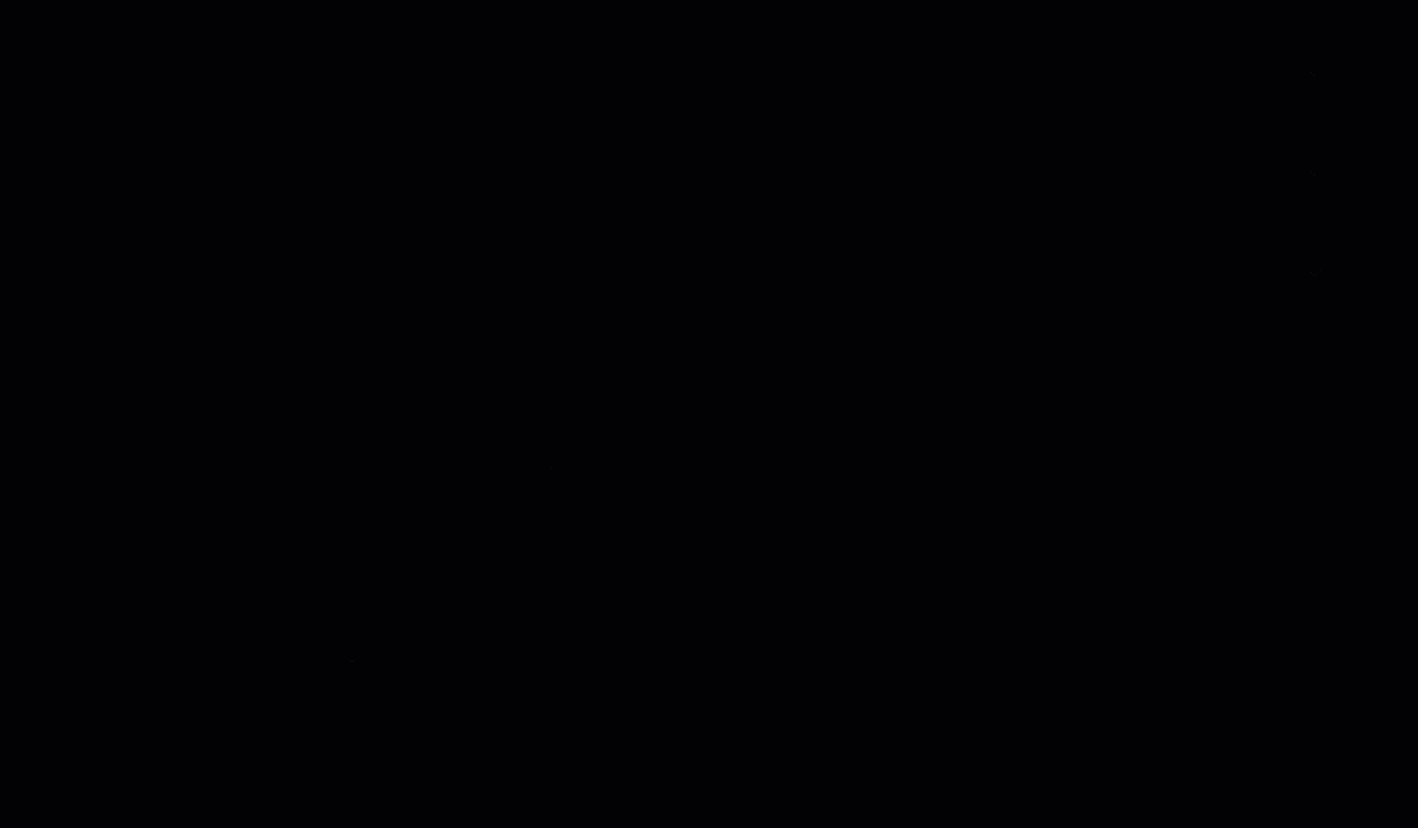
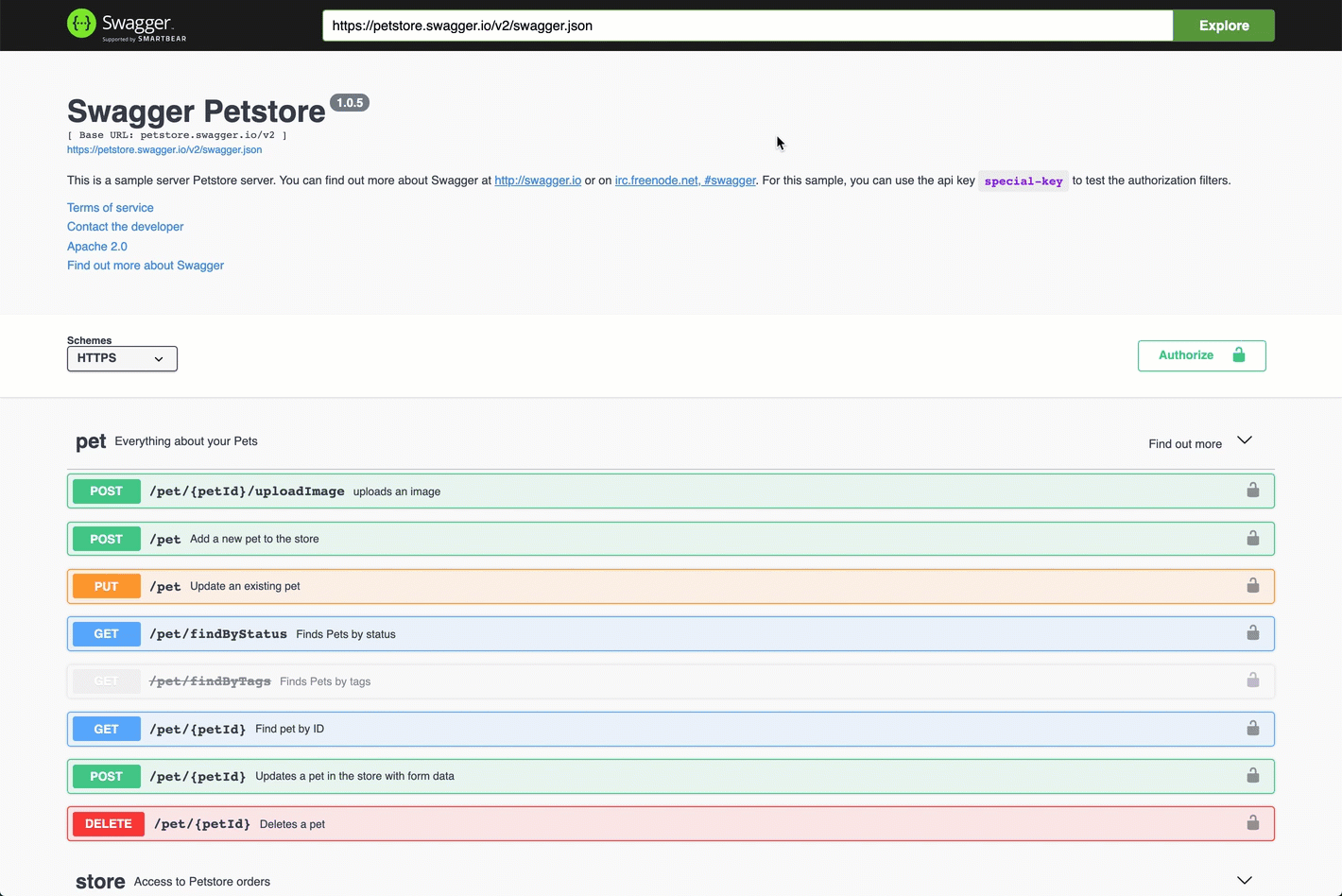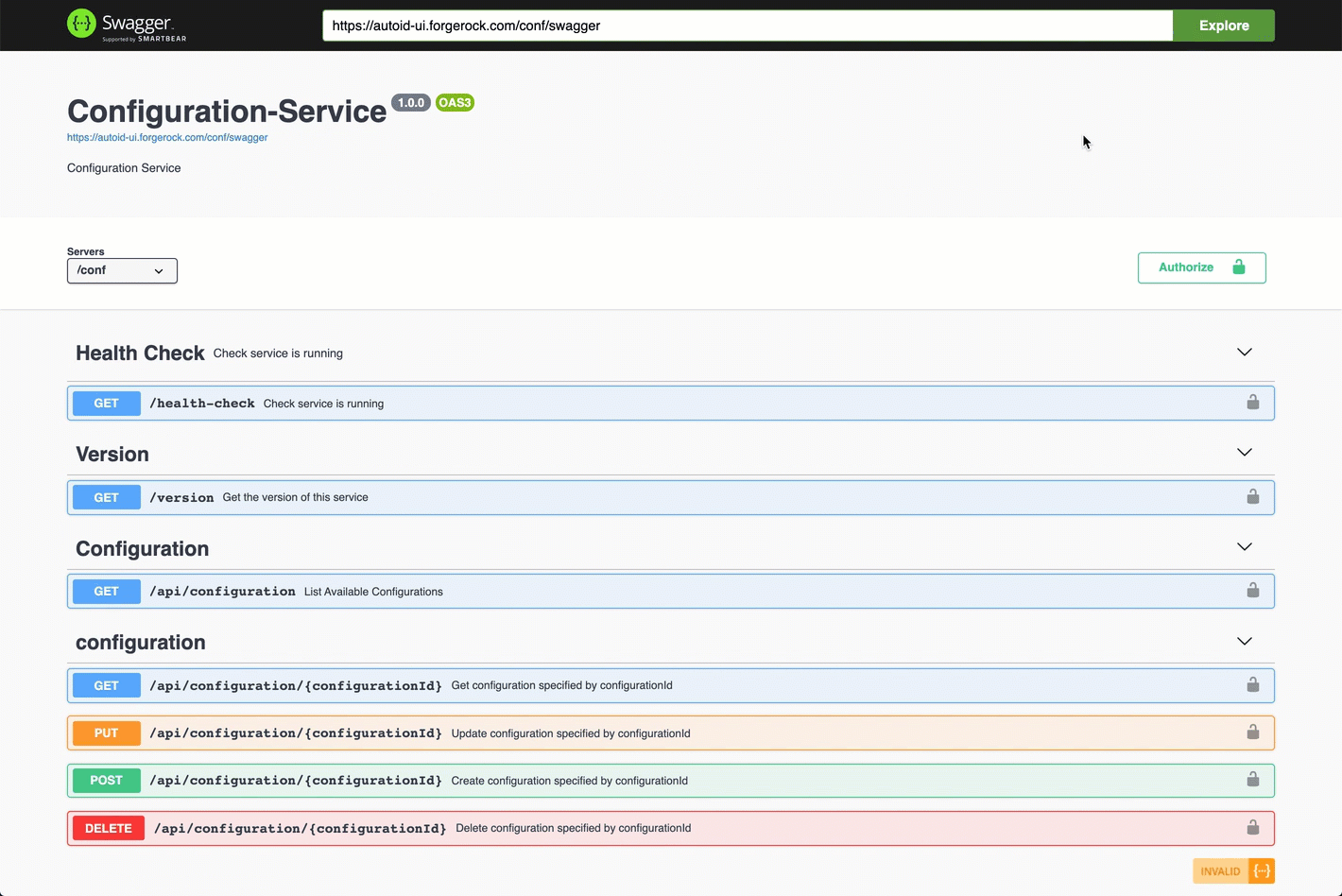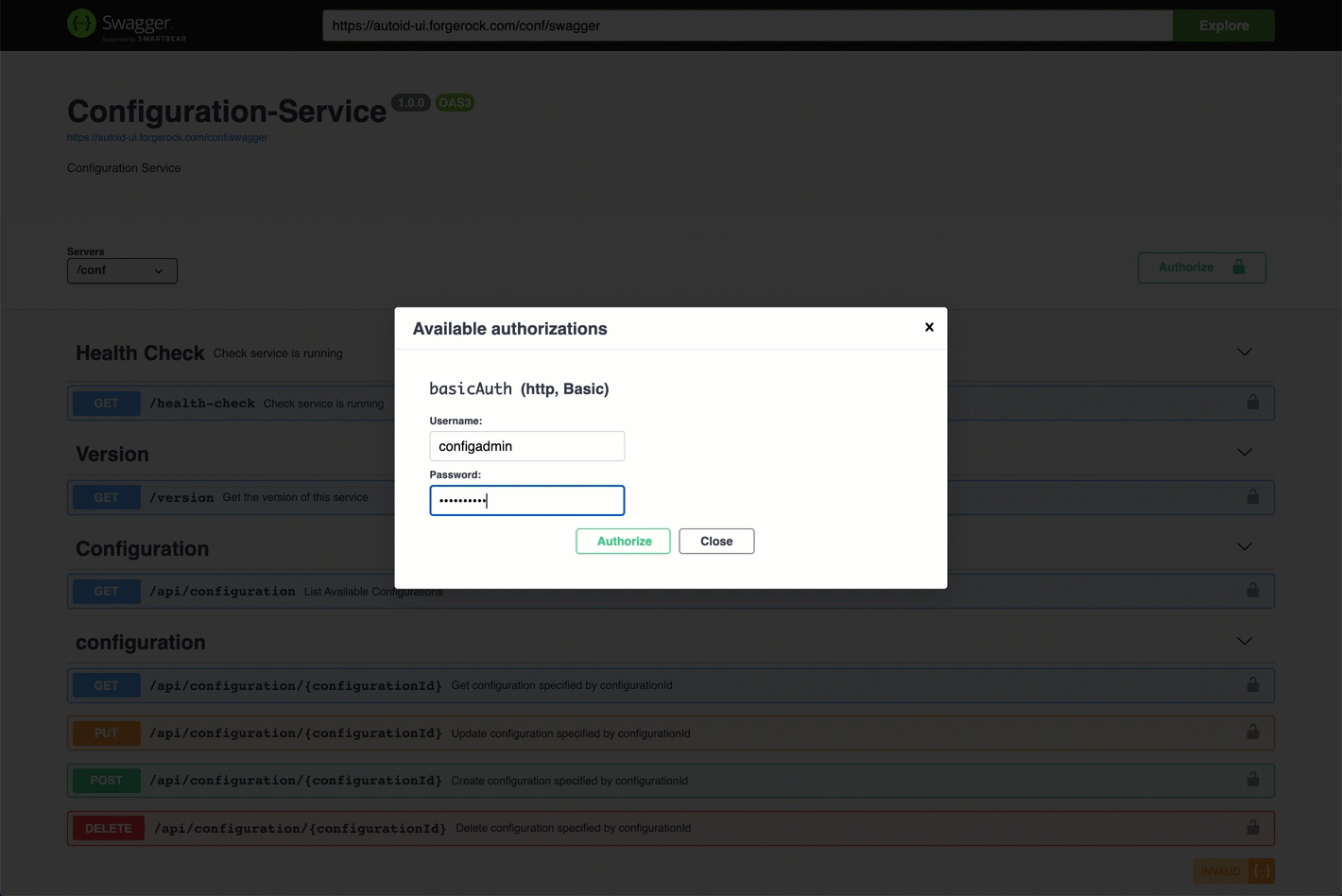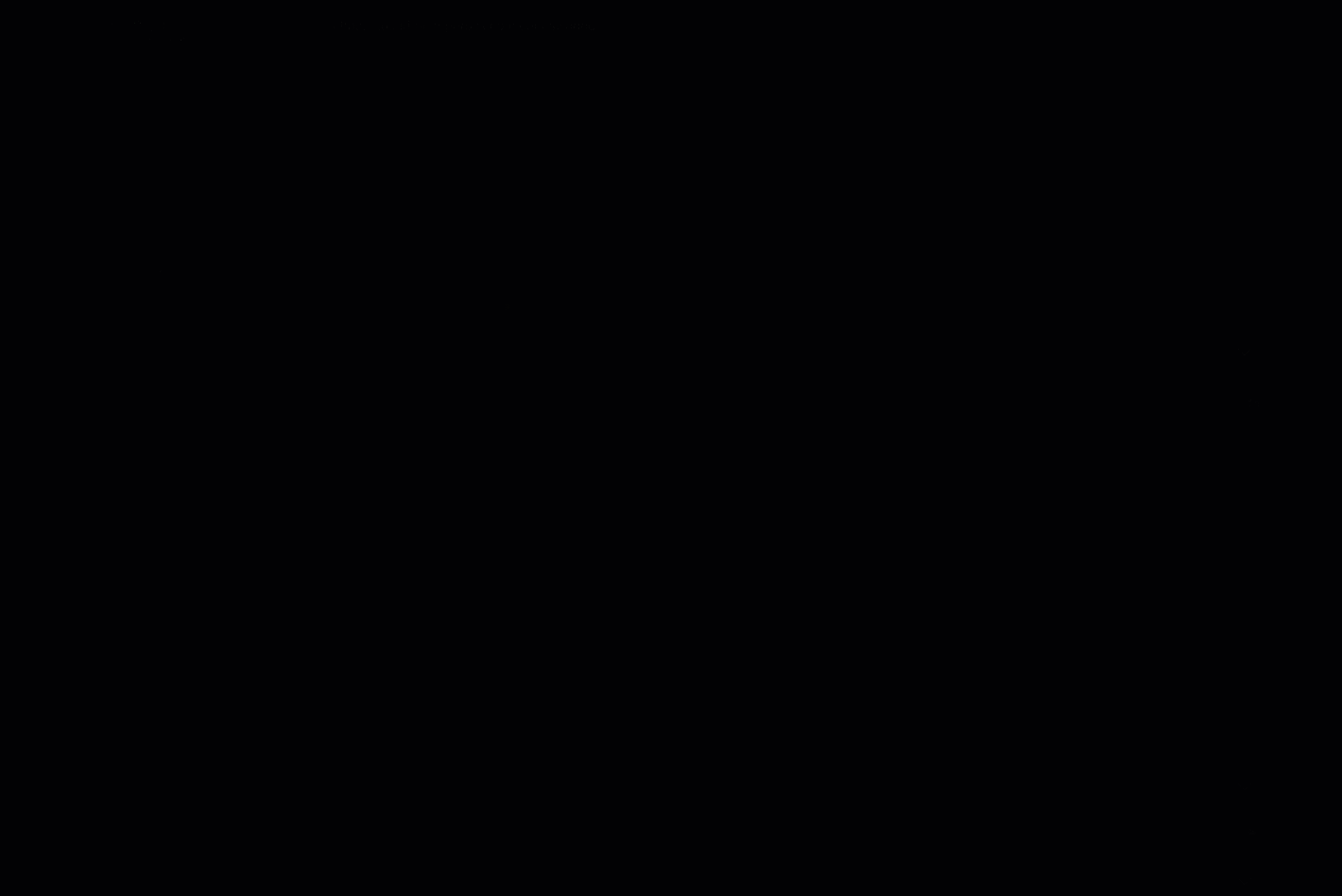
Go back to the Swagger page in step 2, and enter
https://autoid-ui.forgerock.com/api/swaggerin the field, and click Explore. You will see the Autonomous Identity API service.See it in action
-
Access the Swagger page as presented in Access the Autonomous Identity API on Swagger.
-
Open another browser tab, and point to
https://autoid-ui.forgerock.com/conf/swagger. You should see a raw test version of the API. -
Go back to the Swagger page in step 1, and enter
https://autoid-ui.forgerock.com/conf/swaggerin the field, and click Explore. You will see the Configuration Service API. -
At the top of the page, click Authorize. Enter
configadminand password. The password was set in the~/autoid-config/vault.ymlduring install. Click Authorize, and then close the dialog boxYou can now access the Configuration Service API endpoints in Swagger.
See it in action
Using API Keys
Autonomous Identity gives an administrator the ability to create API keys for those who want to access the system via the API. For more information, see Self Service.
To use an API token, you need both the tenant ID that the API key belongs to, and the API token itself.
Obtain the Tenant ID
In Autonomous Identity 2021.8.0 and later, the tenant ID is set as an environment variable that you can easily access.
-
On the target node, get the tenant ID.
$ env | grep TENANT_ID TENANT_ID=8700f5cb-eaca-461e-8c2e-245a25f2399d
API Key Examples
The following curl example illustrates how to use the API key to get a datasource ID for an ingestion job:
-
Obtain an API key from an administrator. See Create API Keys.
-
Obtain the tenant ID using the environment variable.
$ env | grep TENANT_ID TENANT_ID=8700f5cb-eaca-461e-8c2e-245a25f2399d
-
Query Autonomous Identity’s Java API Service (JAS) to obtain a data source ID using the API Key (for example, '1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1'):
curl 'https://autoid-ui.forgerock.com/jas/datasource/search' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/data-sources' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "query": { "sort": [ { "datasource_id.keyword": { "order": "desc" } } ], "size": 10, "track_total_hits": true, "query": { "match_all": {} } } }' \ --compressed \ --insecure
The response includes the datasource ID:
{ "took": 8, "timed_out": false, "_shards": { "total": 3, "successful": 3, "skipped": 0, "failed": 0 }, "hits": { "total": { "value": 1, "relation": "eq" }, "max_score": null, "hits": [ { "_index": "autonomous-iam_common_datasources_latest", "_type": "_doc", "_id": "259b80c7693e92c4c29bd64deac4cd99826d427027645c9413afdb3f083b891d8d34cefaebd5fcf098c066dc1a4da2879d8732d59bfd2e239a285184f8e7a35b", "_score": null, "_source": { "datasource_id": "2d7a6a76-469c-4035-b312-fb1daf104e98", "name": "Showcase-CSV-DS", "sync_type": "full", "icon": "apps", "isActive": true, "entityTypes": { "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/applications": { "uri": { "file": "file:/data/input/applications.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/assignments": { "uri": { "file": "file:/data/input/assignments.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/entitlements": { "uri": { "file": "file:/data/input/entitlements.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/identities": { "uri": { "file": "file:/data/input/identities.csv" } } }, "connectionSettings": { "csv": {} }, "metadata": { "contextId": "scripts", "entityType": "/common/datasources", "primaryKey": "2d7a6a76-469c-4035-b312-fb1daf104e98", "entityPath": "/common/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98", "entityDefinition": "datasources", "namespace": "/common", "branch": "actual", "created": "2021-08-25T03:53:33.634Z", "tenantId": "autonomous-iam" } }, "sort": [ "2d7a6a76-469c-4035-b312-fb1daf104e98" ] } ] } } -
Make sure your client that accesses the JAS configuration has something similar to the following:
public static final String CONFIG_JAS_API_TOKEN = "JAS_API_KEY"; public static final String CONFIG_JAS_TENANT_ID = "TENANT_ID";