Prepare for installation
Before you install
Consider the following before you install:
-
Install AM and Web Agent in different servers.
-
Make sure AM is running so that you can contact AM from the agent web server.
-
Install the web server before you install the agent.
-
Install only one Web Agent for each web server and configure as many agent instances as necessary.
-
For environments with load balancers or reverse proxies, consider the communication between the agent and AM servers, and between the agent and the client. Configure both AM and the environment before you install the agent. Learn more in Configure load balancers and reverse proxies.
Download and unzip Web Agent
Go to the BackStage download site and download an agent based on your architecture, and operating system requirements. Verify the checksum of the downloaded file against the checksum posted on the download page.
Unzip the file in the directory where you plan to store the agent configuration and log files. The following directories are extracted:
| Directory | Description | ||
|---|---|---|---|
|
The installation and configuration program |
||
|
Configuration templates used by the |
||
|
Configuration files, and audit and debug logs for individual instances of the agents. The directory is empty when first extracted.
|
||
|
Licensing information including third-party licenses. |
||
|
Shared libraries used by the agent. |
||
|
Log files written during installation. The directory is empty when first extracted. When the agent is running, the directory can contain the following files:
|
||
|
POST data preservation cache. The agent stores POST data preservation files temporarily. To change the directory, configure POST Data Storage Directory. |
Pre-installation tasks
-
In AM, add an agent profile as described in Create agent profiles. The example in this guide uses an agent profile in the top-level realm, with the following values:
-
Agent ID:
web-agent -
Agent URL:
http://www.example.com:80 -
Server URL:
https://am.example.com:8443/am -
Password:
password
-
-
In AM, add a policy set and policy as described in Policies in AM’s Authorization guide. The example in this guide uses a policy set and policy in the top-level realm, with the following values:
-
Policy set:
-
Name:
PEP -
Resource Types:
URL
-
-
Policy:
-
Name:
PEP-policy -
Resource Type:
URL -
Resource pattern:
*://*:*/* -
Resource value:
*://*:*/* -
Actions tab: Allow HTTP
GETandPOST -
Subjects tab: All Authenticated Users.
-
When you use your own policy set instead of the default policy set,
iPlanetAMWebAgentService, update the following properties in the agent profile: -
-
Configure AM to protect the CDSSO cookie from hijacking. For more information, refer to Restrict tokens for CDSSO session cookies in AM’s Security guide.
-
Create a text file for the agent password, and protect it. For example, use commands similar to these, but use a strong password and store it in a secure place:
-
Unix
-
Windows
$ cat > /secure-directory/pwd.txt password CTRL+D $ chmod 400 /secure-directory/pwd.txt
C:> type > pwd.txt password CTRL+Z
In Windows Explorer, right-click the password file, select Read-Only, and then click OK.
Although the agent accepts any password length and content, you are strongly encouraged to generate secure passwords. This can be achieved in various ways, for example, by using a password manager. -
-
If either of the following is true, set up the required environment variables:
-
AM is configured to perform client authentication
-
The agent web server is configured to validate AM’s server certificate
Learn more in Environment variables.
-
Create agent profiles
Use Web Agent profiles to connect to and communicate with Advanced Identity Cloud or AM.
| You can find additional details about creating an agent profile in Advanced Identity Cloud in Create an agent profile in Advanced Identity Cloud. |
Create an agent profile for a single agent instance
This section describes how to create an agent profile in the AM admin UI.
Alternatively, create agent profiles by using the
/realm-config/agents/WebAgent/{id} endpoint in the REST API.
Learn more in
REST API explorer in AM’s REST guide.
-
In the AM admin UI, select Realms > Realm Name > Applications > Agents > Web, and add an agent using the following hints:
- Agent ID
-
The ID of the agent profile. This ID resembles a username and is used during the agent installation. For example,
MyAgent.When AM is not available, the related error message contains the agent profile name. Consider this in your choice of agent profile name. - Agent URL
-
The URL where the agent resides. Learn more in Example installation for this guide.
In centralized configuration mode, the Agent URL populates the agent profile for services, such as notifications.
- Server URL
-
The full URL to an authorization server, such as AM. Learn more in Example installation for this guide.
If the authorization server is deployed in a site configuration (behind a load balancer), enter the site URL.
In centralized configuration mode, the Server URL populates the agent profile for use with login, logout, naming, and cross-domain SSO.
- Password
-
The password the agent uses to authenticate to an authorization server, such as AM. Use this password when installing an agent.
Although the agent accepts any password length and content, you are strongly encouraged to generate secure passwords. This can be achieved in various ways, for example, by using a password manager.
-
(Optional - From AM 7.5) Use AM’s secret service to manage the agent profile password. If AM finds a matching secret in a secret store, it uses that secret instead of the agent password configured in Step 1.
-
In the agent profile page, set a label for the agent password in Secret Label Identifier.
AM uses the identifier to generate a secret label for the agent.
The secret label has the format
am.application.agents.identifier.secret, where identifier is the Secret Label Identifier.The Secret Label Identifier can contain only characters
a-z,A-Z,0-9, and periods (.). It can’t start or end with a period. -
Select Secret Stores and configure a secret store.
-
Map the label to the secret. Learn more in AM’s Map and rotate secrets.
Note the following points for using AM’s secret service:
-
Set a Secret Label Identifier that clearly identifies the agent.
-
If you update the Secret Label Identifier:
-
If no other agent shares that secret mapping, AM updates any corresponding secret mapping for the previous identifier.
-
If another agent shares that secret mapping, AM creates a new secret mapping for the updated identifier and copies its aliases from the previously shared secret mapping.
-
-
If you delete the Secret Label Identifier, AM deletes any corresponding secret mapping for the previous identifier, provided no other agent shares that secret mapping.
-
When you rotate a secret, update the corresponding mapping.
-
Create an agent profile for multiple agent instances when post data preservation is enabled
By default, the POST data preservation load balancer cookie name and value is set by the agent profile. Therefore, each agent instance behind a load balancer requires its own agent profile.
In scalable environments, such as deployments with load balancing, or environments that run Kubernetes, resources are dynamically created and destroyed.
To facilitate the rapid creation and destruction of agent instances when post
data preservation is enabled, set the POST data preservation configuration
in agent.conf to map one agent profile to multiple agent
instances.
The configuration in agent.conf overrides the
configuration in AM for the following properties:
You can find an example in Map one agent profile to multiple agent instances when POST data preservation is enabled.
Create an agent profile group
Use agent profile groups when you set up multiple agents, and want to inherit settings from the group.
-
In the AM admin UI, go to Realms > Realm Name > Applications > Agents > Web.
-
Select the Groups tab, and add a group with the following settings:
-
Group ID: A name for the profile group.
-
Server URL: The URL of the AM server in which to store the profile.
-
Inherit properties from an agent profile group
-
Set up an agent profile and agent profile group, as described in Create an agent profile for a single agent instance and Create an agent profile group.
-
In the AM admin UI, select your agent profile.
-
On the Global tab, select Group, and select a group from the drop-down menu. The agent profile is added to the group.
-
For each setting in the Global tab, select or deselect the icon:
-
: Inherit this setting from the group
-
: Do not inherit this setting from the group
-
Authenticate agents to the identity provider
Authenticate agents to Advanced Identity Cloud
|
Web Agent is automatically authenticated to Advanced Identity Cloud by a non-configurable authentication module. Authentication chains and modules are deprecated in Advanced Identity Cloud and replaced by journeys. You can now authenticate Web Agent to Advanced Identity Cloud with a journey. The procedure is currently optional, but will be required when authentication chains and modules are removed in a future release of Advanced Identity Cloud. Learn more in Advanced Identity Cloud’s Journeys. |
This section describes how to create a journey to authenticate Web Agent to Advanced Identity Cloud. The journey has the following requirements:
-
It must be called
Agent -
Its nodes must pass the agent credentials to the Agent Data Store Decision node.
When you define a journey in Advanced Identity Cloud, that same journey is used for all instances of PingGateway, Java Agent, and Web Agent. Consider this point if you change the journey configuration.
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Click Journeys > New Journey.
-
Add a journey with the following information and click Create journey:
-
Name:
Agent -
Identity Object: The user or device to authenticate.
-
(Optional) Description: Authenticate an agent to Advanced Identity Cloud
The journey designer is displayed, with the
Startentry point connected to theFailureexit point, and aSuccessnode. -
-
Using the Filter nodes bar, find and then drag the following nodes from the Components panel into the designer area:
-
Zero Page Login Collector node to check whether the agent credentials are provided in the incoming authentication request and use their values in the following nodes.
This node is required for compatibility with Java agent and Web agent.
-
Page node to collect the agent credentials if they are not provided in the incoming authentication request and use their values in the following nodes.
-
Agent Data Store Decision node to verify that the agent credentials match the registered Web Agent agent profile.
Many nodes can be configured in the panel on the right side of the page. Unless otherwise stated, do not configure the nodes and use only the default values. -
-
Drag the following nodes from the Components panel into the Page node:
-
Platform Username node
-
Platform Password node
-
-
Connect the nodes as follows and save the journey:
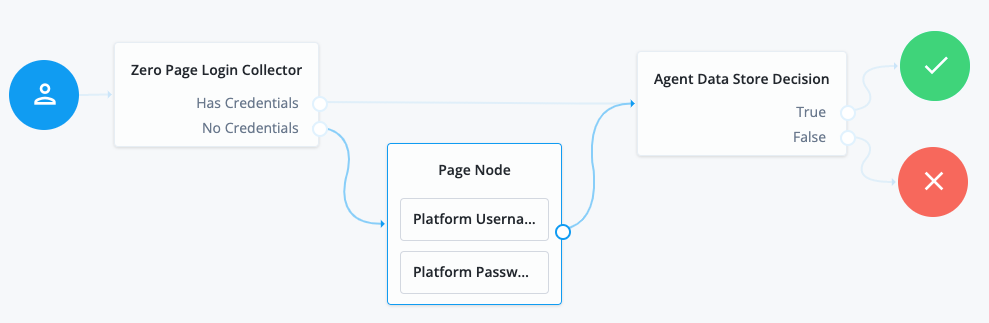
Authenticate agents to AM
Learn more in AM’s Authentication Nodes and Trees. |
This section describes how to create an authentication tree to authenticate Web Agent to AM. The tree has the following requirements:
-
It must be called
Agent -
Its nodes must pass the agent credentials to the Agent Data Store Decision node.
When you define a tree in AM, that same tree is used for all instances of PingGateway, Java Agent, and Web Agent. Consider this point if you change the tree configuration.
-
On the Realms page of the AM admin UI, choose the realm in which to create the authentication tree.
-
On the Realm Overview page, click Authentication > Trees > Create tree.
-
Create a tree named
Agent.The authentication tree designer is displayed, with the
Startentry point connected to theFailureexit point, and aSuccessnode.The authentication tree designer provides the following features on the toolbar:
Button Usage 
Lay out and align nodes according to the order they are connected.

Toggle the designer window between normal and full-screen layout.

Remove the selected node. Note that the
Startentry point cannot be deleted. -
Using the Filter bar, find and then drag the following nodes from the Components panel into the designer area:
-
Zero Page Login Collector node to check whether the agent credentials are provided in the incoming authentication request and use their values in the following nodes.
This node is required for compatibility with Java agent and Web agent.
-
Page node to collect the agent credentials if they are not provided in the incoming authentication request and use their values in the following nodes.
-
Agent Data Store Decision node to verify that the agent credentials match the registered Web Agent profile.
Many nodes can be configured in the panel on the right side of the page. Unless otherwise stated, do not configure the nodes and use only the default values. -
-
Drag the following nodes from the Components panel into the Page node:
-
Username Collector node, to prompt the user to enter their username
-
Password Collector node,to prompt the user to enter their password
-
-
Connect the nodes as follows and save the tree:
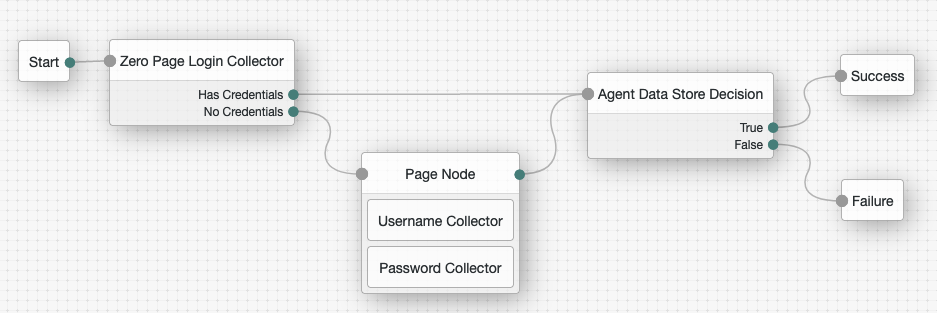
Check agents can connect to the identity provider
You can authenticate as the agent you created a profile for in Advanced Identity Cloud or AM to check the agent can connect successfully. A successful connection proves the agent can connect to Advanced Identity Cloud or AM, their credentials are correct, and a valid agent profile exists.
Authenticate as follows:
$ curl \
--request POST \
--header "X-OpenAM-Username: agent-id" \ (1)
--header "X-OpenAM-Password: password" \ (2)
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=2.1" \
'https://am.example.com:8443/am/json/realms/root/realms/alpha/authenticate?auth-service' (3)| 1 | Replace agent-id with the ID of the agent profile you created. |
| 2 | Replace password with the agent password. |
| 3 | Replace auth-service with either authIndexType=module&authIndexValue=Application or authIndexType=service&authIndexValue=Agent depending on whether you authenticate using the default non-configurable authentication module or a journey called Agent. |
If authentication is successful, the response includes the tokenId that corresponds to the agent session and the URL to which the agent would normally be redirected. For example:
{
"tokenId":"AQIC5wM...TU3OQ*",
"successUrl":"/am/console",
"realm":"/alpha"
}