Creating Trees for Push Authentication
Push authentication uses the authentication trees to receive push notifications and to perform the actual authentication itself.
Authentication trees can be used for passwordless authentication using push notifications. When configured for passwordless authentication, the authentication flow asks the user to enter their user ID but not their password. A push notification is then sent to their registered device to complete the authentication by using the ForgeRock Authenticator app.
Before implementing passwordless push authentication, consider the "Limitations When Using Passwordless Push Authentication".
The procedure assumes the following:
Users will provide user IDs and passwords as the first step of multi-factor authentication.
This procedure assumes users have registered using an authentication chain. At this time, authentication trees do not support registering devices. For more information, see in "To Create a Chain for Push Authentication".
A push notification will be sent to the device as a second factor to complete authentication.
The following services are configured:
- ForgeRock Authenticator (Push) Service
Specifies the attribute in which to store information about the registered Push device, and whether to encrypt the data.
For detailed information about the available properties, see "ForgeRock Authenticator (Push) Service".
- Push Notification Service
Configures how AM sends push notifications to registered devices, including endpoints, and access credentials.
For information on provisioning the credentials required by the Push Notification Service, see How To Configure Service Credentials (Push Auth, Docker) in Backstage in the ForgeRock Knowledge Base.
For detailed information about the available properties, see "Push Notification Service".
To create a multi-factor authentication tree, perform the following steps:
Log in to the AM console as an AM administrator, for example
amAdmin.Select the realm that will contain the authentication tree.
Create the authentication tree as follows:
Select Authentication > Trees, and then click Create Tree.
The New Tree page appears.
Specify a name of your choosing, for example
myPushAuthTree, and then click Create.The authentication tree designer is displayed, with the Start entry point connected to the Failure exit point.
You can add nodes to the authentication tree by dragging the node from the Components panel on the left-hand side and dropping it into the designer area.
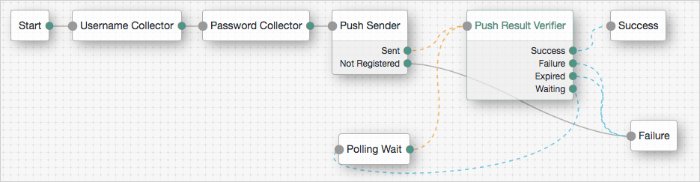
Add the following nodes to the authentication tree:
Connect the nodes as demonstrated in the following figure:
Save your changes.
Test your authentication tree as follows:
Logout of AM, and then navigate to a URL similar to the following:
https://openam.example.com:8443/openam/XUI/?realm=/&service=myPushAuthTree#loginA login screen prompting you to enter your user ID and password appears.
Follow the procedure described in "Testing Push Authentication" to verify that you can use the ForgeRock Authenticator app to perform multi-factor authentication. If the authentication tree is correctly configured, authentication is successful and AM displays the user profile page.
The procedure assumes the following:
Users will provide only their user IDs as the first step of multi-factor authentication.
This procedure assumes users have registered using an authentication chain. At this time, authentication trees do not support registering devices. For more information, see in "To Create a Chain for Push Authentication".
A push notification will be sent to the device as a second factor to complete authentication, without the need to enter the user's password.
The following services are configured:
- ForgeRock Authenticator (Push) Service
Specifies the attribute in which to store information about the registered Push device, and whether to encrypt the data.
For detailed information about the available properties, see "ForgeRock Authenticator (Push) Service".
- Push Notification Service
Configures how AM sends push notifications to registered devices, including endpoints, and access credentials.
For information on provisioning the credentials required by the Push Notification Service, see How To Configure Service Credentials (Push Auth, Docker) in Backstage in the ForgeRock Knowledge Base.
For detailed information about the available properties, see "Push Notification Service".
To create a multi-factor authentication tree for passwordless authentication, perform the following steps:
Log in to the AM console as an AM administrator, for example
amAdmin.Select the realm that will contain the authentication tree.
Create the authentication tree as follows:
Select Authentication > Trees, and then click Create Tree.
The New Tree page appears.
Specify a name of your choosing, for example
myPasswordlessAuthTree, and then click Create.The authentication tree designer is displayed, with the Start entry point connected to the Failure exit point.
You can add nodes to the authentication tree by dragging the node from the Components panel on the left-hand side and dropping it into the designer area.
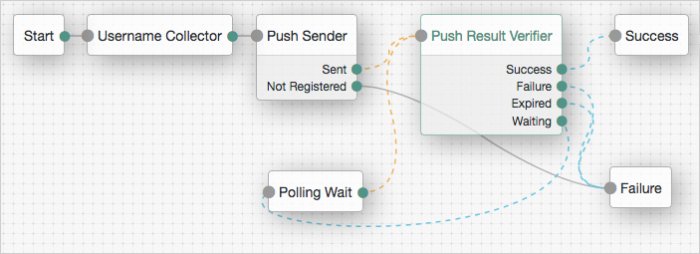
Add the following nodes to the authentication tree:
Success Node
Connect the nodes as demonstrated in the following figure:
Save your changes.
Test your authentication tree as follows:
Logout of AM, and then navigate to a URL similar to the following:
https://openam.example.com:8443/openam/XUI/?realm=/&service=myPasswordlessAuthTree/#loginA login screen prompting you to enter your user ID appears.
Follow the procedure described in "Testing Push Authentication" to verify that you can use the ForgeRock Authenticator app to perform multi-factor authentication. If the authentication tree is correctly configured, authentication is successful and AM displays the user profile page, without having to enter a password.