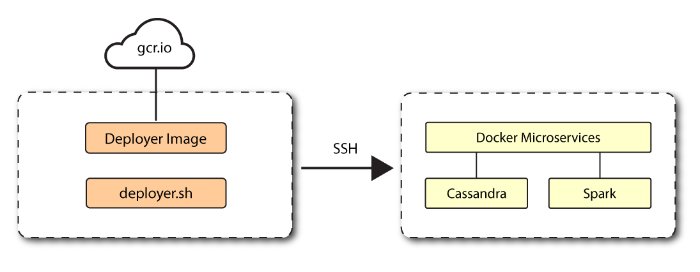
Install a Single Node Target
This chapter presents instructions on deploying Autonomous Identity in a single-target machine that has Internet connectivity. ForgeRock provides a deployer script that pulls a Docker container image from ForgeRock's Google Cloud Registry (gcr.io) repository. The image contains the microservices, analytics, and backend databases needed for the system.
This installation assumes that you set up the deployer script on a separate machine from the target. This lets you launch a build from a laptop or local server.
Figure 8: A single-node target deployment.
Let's deploy Autonomous Identity on a single-node target on CentOS 7. The following are prequisites:
Operating System. The target machine requires CentOS 7. The deployer machine can use any operating system as long as Docker is installed. For this guide, we use CentOS 7 as its base operating system.
Memory Requirements. Make sure you have enough free disk space on the deployer machine before running the
deployer.shcommands. We recommend at least a 40GB/partition with 14GB used and 27GB free after running the commands.Default Shell. The default shell for the
autoiduser must be bash.Deployment Requirements. Autonomous Identity provides a Docker image that creates a
deployer.shscript. The script downloads additional images necessary for the installation. To download the deployment images, you must first obtain a registry key to log into the ForgeRock Google Cloud Registry (gcr.io). The registry key is only available to ForgeRock Autonomous Identity customers. For specific instructions on obtaining the registry key, see How To Configure Service Credentials (Push Auth, Docker) in Backstage.
Set Up the Target Machine
The install assumes that you have CentOS 7 as your operating system. Check your CentOS 7 version.
$
sudo cat /etc/centos-releaseSet the user for the target machine to a username of your choice. For example,
autoid.$
sudo adduser autoidSet the password for the user you created in the previous step.
$
sudo passwd autoidConfigure the user for passwordless sudo.
$
echo "autoid ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/autoidAdd administrator privileges to the user.
$
sudo usermod -aG wheel autoidChange to the user account.
$
su - autoidInstall yum-utils package on the deployer machine. yum-utils is a utilities manager for the Yum RPM package repository. The repository compresses software packages for Linux distributions.
$
sudo yum install -y yum-utils
Set Up the Deployer Machine
Set up another machine as a deployer node. You can use any OS-based machine for the deployer as long as it has Docker installed. For this example, we use CentOS 7.
The install assumes that you have CentOS 7 as your operating system. Check your CentOS 7 version.
$
sudo cat /etc/centos-releaseSet the user for the target machine to a username of your choice. For example,
autoid.#
sudo adduser autoidSet the password for the user you created in the previous step.
$
sudo passwd autoidConfigure the user for passwordless sudo.
$
echo "autoid ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/autoidAdd administrator privileges to the user.
$
sudo usermod -aG wheel autoidChange to the user account.
$
su - autoidInstall yum-utils package on the deployer machine. yum-utils is a utilities manager for the Yum RPM package repository. The repository compresses software packages for Linux distributions.
$
sudo yum install -y yum-utilsCreate the installation directory. Note that you can use any install directory for your system as long as your run the deployer.sh script from there. Also, the disk volume where you have the install directory must have at least 8GB free space for the installation.
$
mkdir ~/autoid-config
Install Docker on the Deployer Machine
Install Docker on the deployer machine. We run commands from this machine to install Autonomous Identity on the target machine. In this example, we use CentOS 7.
On the target machine, set up the Docker-CE repository.
$
sudo yum-config-manager \ --add-repo https://download.docker.com/linux/centos/docker-ce.repoInstall the latest version of the Docker CE, the command-line interface, and containerd.io, a containerized website.
$
sudo yum install -y docker-ce docker-ce-cli containerd.ioEnable Docker to start at boot.
$
sudo systemctl enable dockerStart Docker.
$
sudo systemctl start dockerCheck that Docker is running.
$
systemctl status dockerAdd the user to the Docker group.
$
sudo usermod -aG docker ${USER}
Set Up SSH on the Deployer
On the deployer machine, change to the SSH directory.
$
cd ~/.sshOn the deployer machine, run ssh-keygen to generate an RSA keypair, and then click Enter. You can use the default filename. Enter a password for protecting your private key.
$
ssh-keygen -t rsa -C "autoid"The public and private rsa key pair is stored in
home-directory/.ssh/id_rsaandhome-directory/.ssh/id_rsa.pub.Copy the SSH key to the
autoid-configdirectory.$
cp ~/.ssh/id_rsa ~/autoid-configChange the privileges and owner to the file.
$
chmod 400 ~/autoid-config/id_rsaCopy your public SSH key,
id_rsa.pub, to the target machine's~/.ssh/authorized_keysfile. If your system does not have an/authorized_keysdirectory, create it using mkdir -p ~/.ssh/authorized_keys.$
ssh-copy-id -i id_rsa.pub autoid@<Target IP Address>On the deployer machine, test your SSH connection to the target machine. This is a critical step. Make sure the connection works before proceeding with the installation.
$
ssh -i ~/.ssh/id_rsa <username>@34.70.190.144Last login: Sun Jun 14 23:23:36 2020 from 74.125.45.78On the target machine, set the privileges on your
~/.sshand~/.ssh/authorized_keys.$
chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keysIf you successfully accessed the remote server, enter exit to end your SSH session.
Install Autonomous Identity
On the deployer machine, change to the installation directory.
$
cd ~/autoid-configLog in to the ForgeRock Google Cloud Registry (gcr.io) using the registry key. The registry key is only available to ForgeRock Autonomous Identity customers. For specific instructions on obtaining the registry key, see How To Configure Service Credentials (Push Auth, Docker) in Backstage.
$
docker login -u _json_key -p "$(cat autoid_registry_key.json)" https://gcr.io/forgerock-autoidRun the create-template command to generate the
deployer.shscript wrapper. Note that the command sets the configuration directory on the target node to/config. Note that the --user parameter eliminates the need to use sudo while editing the hosts file and other configuration files.$
docker run --user=$(id -u) -v ~/autoid-config:/config -it gcr.io/forgerock-autoid/deployer:2020.6.4 create-template... d6c7c6f3303e: Pull complete Digest: sha256:15225be65417f8bfb111adea37c83eb5e0d87140ed498bfb624a358f43fb48bf Status: Downloaded newer image for gcr.io/forgerock-autoid/autoid/dev-compact/deployer@sha256:15225be65417f8bfb111a dea37c83eb5e0d87140ed498bfb624a358f43fb48bf Config template is copied to host machine directory mapped to /configMake the script executable.
$
chmod +x deployer.shTo see the list of commands, enter
deployer.sh.$
./deployer.shUsage: deployer <command> Commands: create-template download-images import-deployer encrypt-vault decrypt-vault run create-tar install-docker install-dbutilsThe create-template command creates a number of configuration files, including
ansible.cfg. Open a text editor and edit theansible.cfgto set up the remote user and SSH private key file location on the target node. Make sure that theremote_userexists on the target node and that the deployer machine can ssh to the target node as the user specified in theid_rsafile.[defaults] host_key_checking = False remote_user = autoid private_key_file = id_rsaOpen a text editor and enter the target host's public IP addresses in the
~/autoid-config/hostsfile. Make sure the target machine's external IP address is accessible from the deployer machine. The following is an example of the~/autoid-config/hostsfile for a single-node target deployment:[docker-managers] 34.70.190.144 [docker-workers] 34.70.190.144 [docker:children] docker-managers docker-workers [cassandra-seeds] 34.70.190.144 [cassandra-workers] 34.70.190.144 [spark-master] 34.70.190.144 [spark-workers] 34.70.190.144 [analytics] 34.70.190.144If your external and internal IP addresses are different, for example, when deploying the target host in a cloud, define a mapping between the external IP address and the private IP address in the
~/autoid-config/vars.ymlfile.If your external and internal IP addresses are the same, you can skip this step.
On the deployer node, add the
private_ip_address_mappingproperty in the~/autoid-config/vars.ymlfile. You can look up the private IP on the cloud console, or run sudo ifconfig on the target host. Make sure the values are within double quotes. The key should not be in double quotes and should have two spaces preceding the IP address.private_ip_address_mapping: external_ip: "internal_ip"For example:
private_ip_address_mapping: 34.72.28.214: "10.128.0.52"Edit other properties in the
~/autoid-config/vars.ymlfile, specific to your deployment, such as the following:Domain name. For information, see Customize the Domain and Namespace.
UI Theme. Autonomous Identity provides a dark theme mode for its UI. Set the
enable_dark_themetotrueto enable it.Session Duration. The default session duration is set to 30 minutes. You can alter this value by editing the
jwt_expiryproperty to a time value in minutes of your choice.SSO. Autonomous Identity provides a single sign-on (SSO) feature that you can configure with an OIDC IdP provider. For information, see Set Up Single Sign-On.
The default Autonomous Identity URL will be:
https://autoid-ui.forgerock.com. To customize your domain name and target environment, see Customize the Domain and Namespace.Open a text editor and set the Autonomous Identity passwords for the configuration service, LDAP backend, and Cassandra database. The vault passwords file is located at
~/autoid-config/vault.yml.Note
Do not include special characters & or $ in
vault.ymlpasswords as it will result in a failed deployer process.configuration_service_vault: basic_auth_password: Welcome123 openldap_vault: openldap_password: Welcome123 cassandra_vault: cassandra_password: Welcome123 cassandra_admin_password: Welcome123Encrypt the vault file that stores the Autonomous Identity passwords, located at
~/autoid-config/vault.yml. The encrypted passwords will be saved to/config/.autoid_vault_password. The/config/mount is internal to the deployer container.$
./deployer.sh encrypt-vaultDownload the images. This step downloads software dependencies needed for the deployment and places them in the
autoid-packagesdirectory.$
./deployer.sh download-imagesRun the deployment.
$
./deployer.sh run
Resolve Hostname
After installing Autonomous Identity, set up the hostname resolution for your deployment.
Configure your DNS servers to access Autonomous Identity dashboard and self-service applications on the target node. The following domain names must resolve to the IP address of the target node:
<target-environment>-ui.<domain-name>and<target-environment>-selfservice.<domain-name>.If DNS cannot resolve target node hostname, edit it locally on the machine that you want to access Autonomous Identity using a browser. Open a text editor and add an entry in the
/etc/hostsfile for the self-service and UI services for each managed target node.target-ip-address <target-environment>-ui.<domain-name> <target-environment>-serlfservice.<domain-name>For example:
34.72.28.214 autoid-ui.forgerock.com autoid-selfservice.forgerock.comIf you set up a custom domain name and target environment, add the entries in
/etc/hosts. For example:34.72.28.214 myid-ui.abc.com myid-selfservice.abc.comFor more information on customizing your domain name, see Customize the Domain and Namespace.
Access the Dashboard
You can now access the Autonomous Identity console UI.
Open a browser, and point it to
https://autoid-ui.forgerock.com/(or your customized URL:https://myid-ui.abc.com).Log in as a test user:
bob.rodgers@forgerock.com. Enter the password:Welcome123.
Check Apache Cassandra
On the target node, check the status of Apache Cassandra.
$ /opt/autoid/apache-cassandra-3.11.2/bin/nodetool status
An example output is as follows:
Datacenter: datacenter1
=======================
Status=Up/Down
|/ State=Normal/Leaving/Joining/Moving
-- Address Load Tokens Owns (effective) Host ID Rack
UN 34.70.190.144 1.33 MiB 256 100.0% a10a91a4-96e83dd-85a2-4f90d19224d9 rack1
Check Apache Spark
SSH to the target node and open Spark dashboard using the bundled text-mode web browser
$
elinks http://localhost:8080You should see Spark Master status as ALIVE and worker(s) with State ALIVE
Access Self-Service
The self-service feature lets Autonomous Identity users change their own passwords.
Open a browser and point it to:
https://autoid-selfservice.forgerock.com/.
Run the Analytics
If the previous steps all check out successfully, you can start an analytics pipeline run, where association rules, confidence scores, predications, and recommendations are determined. Autonomous Identity provides a small demo data set that lets you run the analytics pipeline on. Note for production runs, prepare your company's dataset as outlined in Data Preparation.
SSH to the target node.
Check that the analytics service is running.
$
docker ps | grep analyticsIf the previous step returns blank, start the analytics. For more information, see Data Preparation.
$
docker start analyticsOnce you have verified that the analytics service has started, you can run the analytics commands. For more information, see Run the Analytics Pipeline.
If your analytics pipeline run completes successfully, you have finished your Autonomous Identity installation.