Account Lockout node
The Account Lockout node locks or unlocks the authenticating user’s account profile.
The node also determines whether the account has been locked through both persistent (physical) lockout and duration lockout. For more information, refer to Account lockout for trees.
| You can also use the Account Active Decision node to check whether the account is locked at any point in the journey. |
Compatibility
| Product | Compatible? |
|---|---|
PingOne Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Inputs
This node requires the username property in the incoming node state.
It uses this information to access the account status in the user profile.
It also requires the realm property, which AM sets by default.
Configuration
| Property | Usage |
|---|---|
Lock Action |
Choose whether to |
Outcomes
Single outcome path; the node updates the account status according to the configured Lock Action:
LOCK-
The account is inactive and the user cannot authenticate.
UNLOCK-
The account is active and the user can authenticate.
Errors
If this node fails to set the account status, it logs a failed to set the user status inactive warning.
This node can also throw exceptions with the following messages:
| Message | Notes |
|---|---|
|
Failed to read the |
|
Failed to read the |
|
Failed to find the account profile with this |
|
Failed to update the account status; applies when locking and unlocking the account |
Example
The following simple example uses this node with the Retry Limit Decision node to lock an account after the set number of invalid attempts:
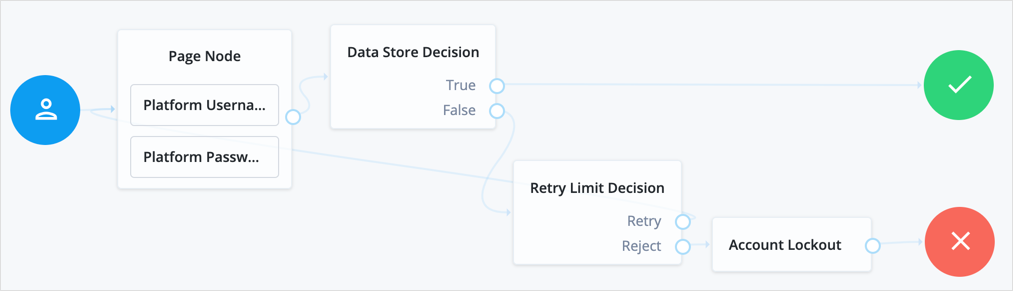
The Retry Limit Decision node Retry limit (default: 3) defines the number of failed attempts before lockout.
Before using a journey like this in deployment, adapt it to reset the retry count on successful authentication.