SAML2 Authentication node
Integrates SAML v2.0 SSO into an AM authentication flow.
Use this node when deploying SAML v2.0 single sign-on in integrated mode (SP-initiated SSO only).
Regardless of the outcome, Account exists or No account exists,
if this node completes without failure, it sets the successURL parameter in the shared node state
to the value of the RelayState parameter in the request.
If the request does not provide a value for this parameter,
the node uses the default RelayState value configured in the service provider (SP).
You can dynamically provision an account on the SP if it does not exist, or you can link the remote account to a local account using the Write Federation Information node.
Before attempting to configure a SAML2 authentication node, ensure that:
-
You have configured a remote identity provider (IdP) and a hosted SP in a circle of trust in the same realm where the authentication node is configured.
-
The service provider is configured for integrated mode.
Refer to SSO and SLO in integrated mode.
Compatibility
| Product | Compatible? |
|---|---|
PingOne Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Outcomes
-
Account exists -
No account exists
If a user account is found that matches the federated account,
evaluation continues along the Account exists outcome;
otherwise, evaluation continues along the No account exists outcome.
Properties
| Property | Usage |
|---|---|
IdP Entity ID |
Specifies the name of the remote IdP. |
SP MetaAlias |
Specifies the local alias for the SP, in the format |
Allow IdP to Create NameID |
Specifies whether the IdP should create a new identifier for the authenticating user if none exists. For detailed information, refer to the section on the Default: |
Comparison Type |
Specifies a comparison method to evaluate authentication context classes or statements. The value specified in this property overrides the value set in the SP configuration in AM admin UI under Realms > Realm Name > Applications > Federation > Entity Providers > Service Provider Name > Assertion Content > Authentication Context > Comparison Type. Valid comparison methods are For more information about the comparison methods, refer to the section on the Default: |
Authentication Context Class Reference |
(Optional) Specifies one or more URIs for authentication context classes to be included in the SAML request. Authentication Context Classes are unique identifiers for an authentication mechanism. The SAML v2.0 protocol supports a standard set of authentication context classes, defined in Authentication Context for the OASIS Security Assertion Markup Language (SAML) V2.0. In addition to the standard authentication context classes, you can specify customized authentication context classes. Any authentication context class you specify in this field must be supported for the service provider. In the AM admin UI, go to Realms > Realm Name > Applications > Federation > Entity Providers > Service Provider Name > Assertion Content > Authentication Context. 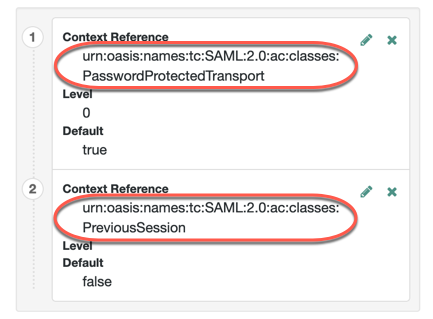
When specifying multiple authentication context classes, use the | character to separate the classes. For example: urn:oasis:names:tc:SAML:2.0:ac:classes:Password|urn:oasis:names:tc:SAML:2.0:ac:classes:TimesyncToken |
Authentication Context Declaration Reference |
(Optional) Specifies one or more URIs that identify authentication context declarations. When specifying multiple URIs, use the | character to separate the URIs. For more information, refer to the section on the |
Request Binding |
Specifies the format the SP will use to send the authentication request to the IdP. Valid values are Default: |
Response Binding |
Specifies the format the IdP will use to send the response to the SP. Valid values are Default: |
Force IdP Authentication |
Specifies whether the IdP forces authentication or if it can reuse existing security contexts. Default: Disabled |
Passive Authentication |
Specifies whether the IdP uses passive authentication or not. Passive authentication requires the IDP to only use authentication methods that do not require user interaction; for example, authenticating using an X.509 certificate. Default: Disabled |
NameID Format |
Specifies the SAML name ID format that will be requested in the SAML authentication request. For example: urn:oasis:names:tc:SAML:2.0:nameid-format:persistent urn:oasis:names:tc:SAML:2.0:nameid-format:transient urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified Default: |
For examples, refer to SSO and SLO in integrated mode.