Generate an API Key
Autonomous Identity gives an administrator the ability to generate API keys for those who want to access certain endpoints using REST. Administrators can create an API from the Self-Service page of the Autonomous Identity UI.
| As of this release, only the Ingest endpoints use the API key. |
|
To use an API token, you need both the tenant ID that the API key belongs to, and the API token itself. |
Obtain the Tenant ID
In Autonomous Identity 2021.8.0 and later, the tenant ID is set as an environment variable that you can easily access.
-
On the target node, get the tenant ID.
$ env | grep TENANT_ID TENANT_ID=8700f5cb-eaca-461e-8c2e-245a25f2399d
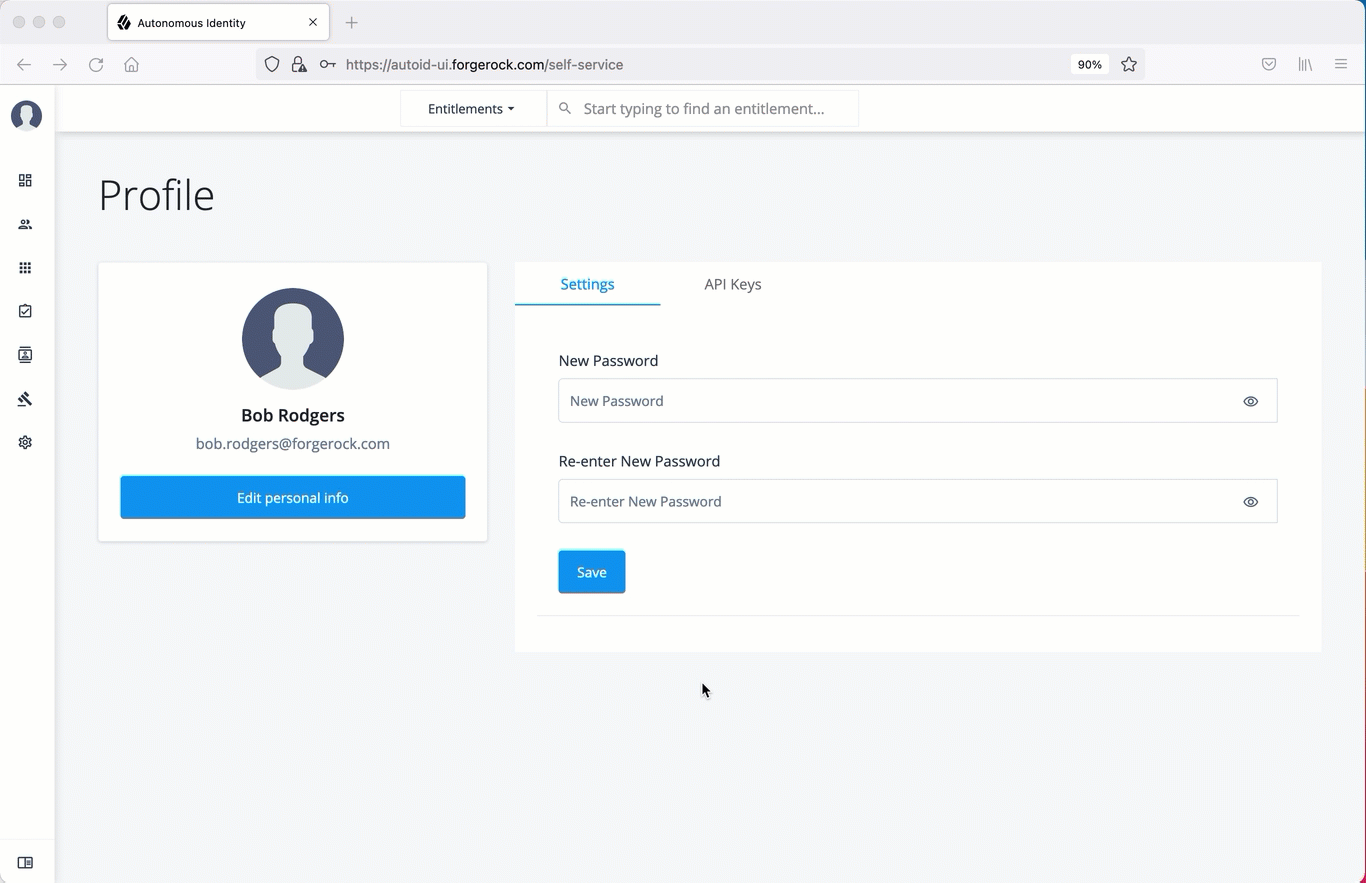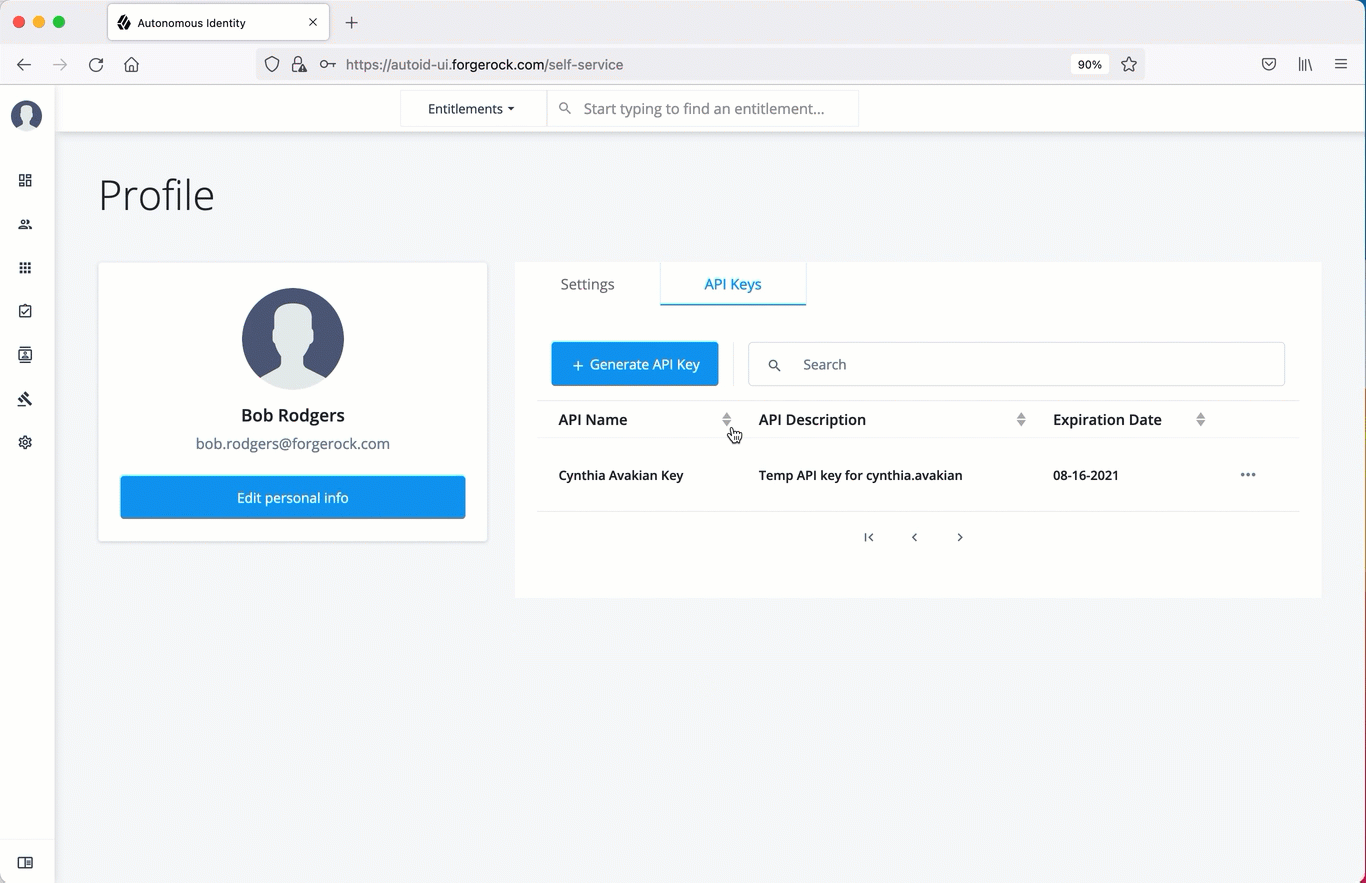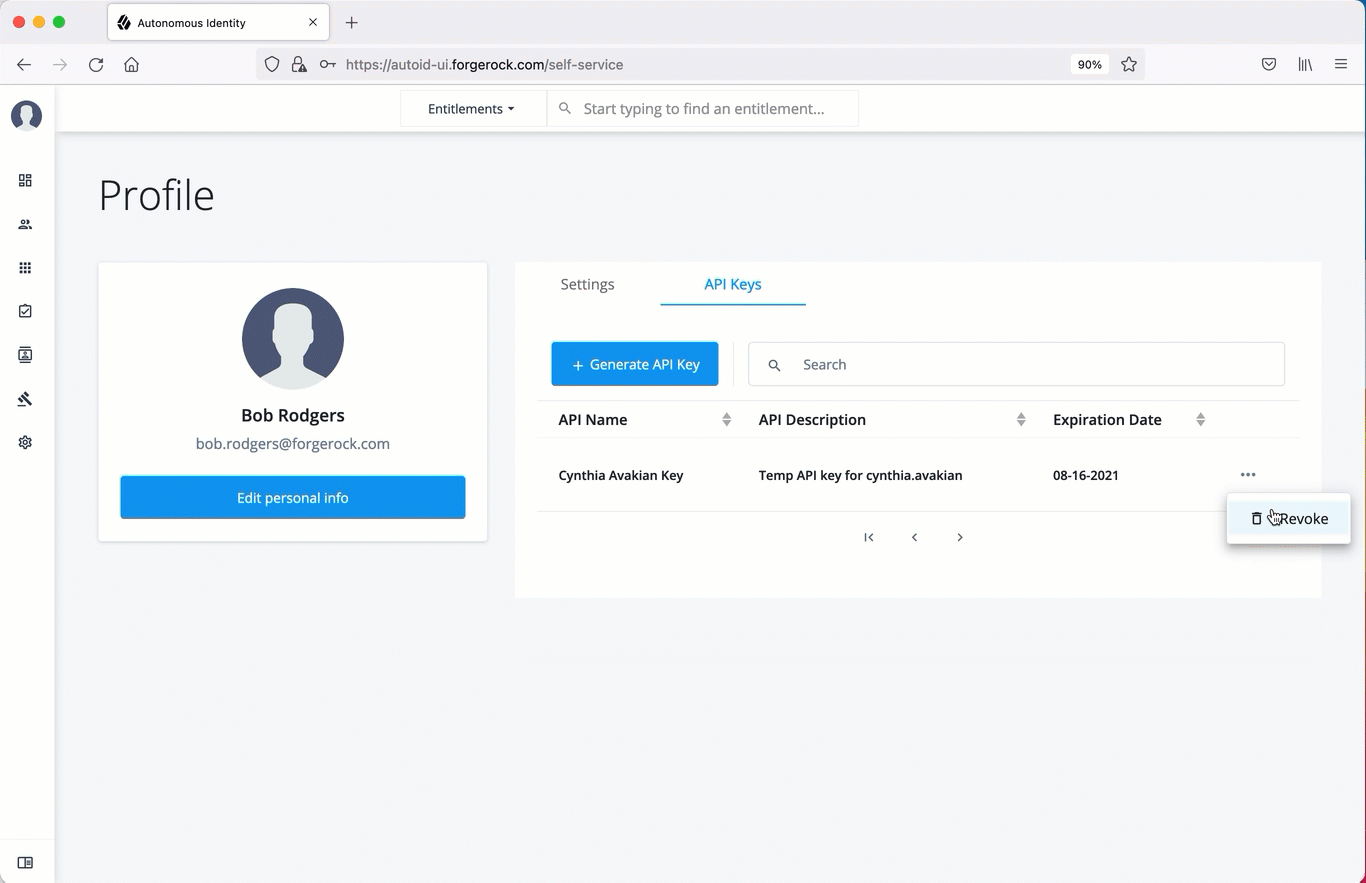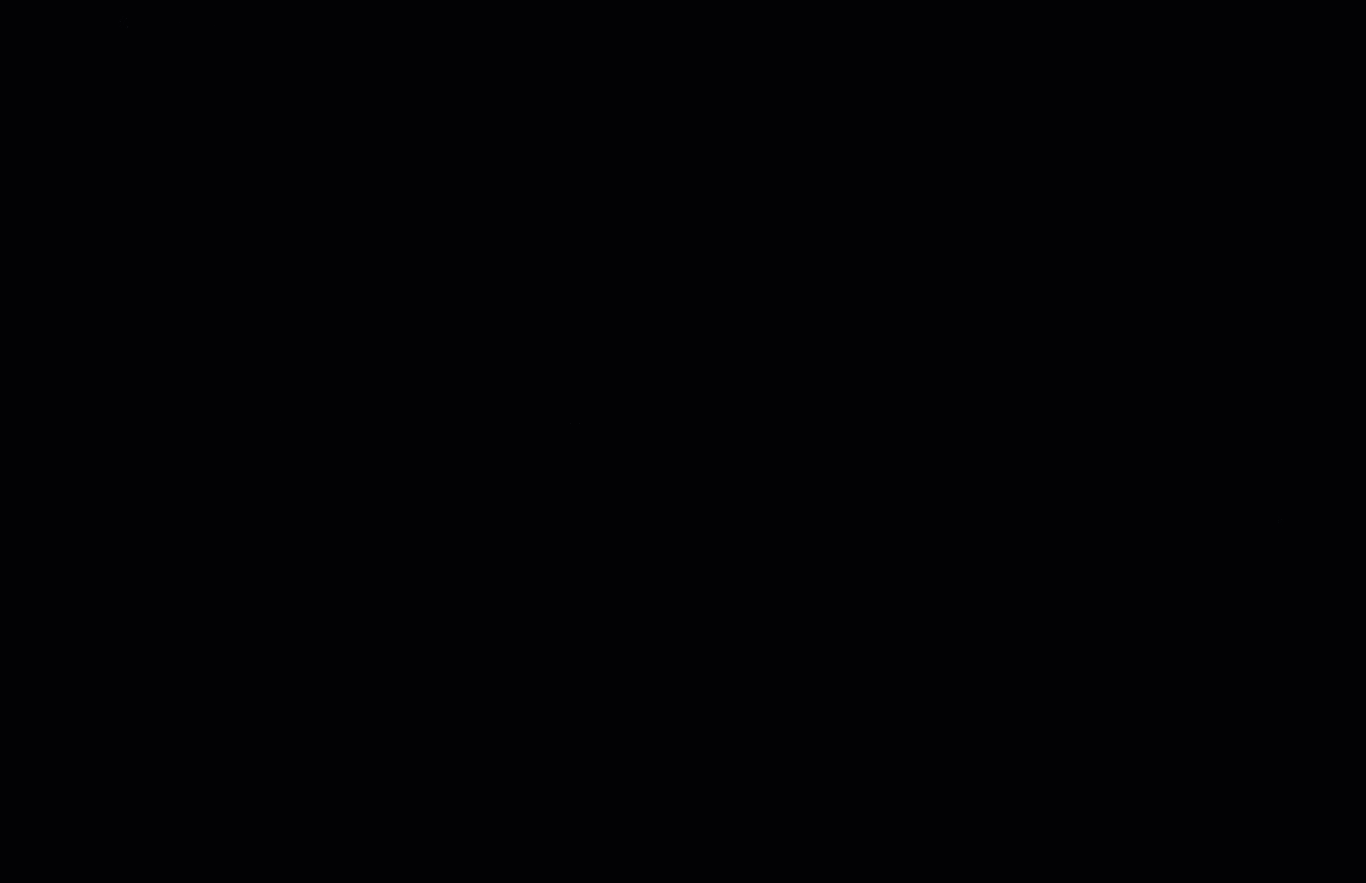
Create an API Key using the UI
Administrators can create API keys on the Self-Service page of the Autonomous Identity UI.
-
On the Autonomous Identity UI, click the admin drop-down on the top-left of the page.
-
Click Self Service.
-
Click the API Keys tab.
-
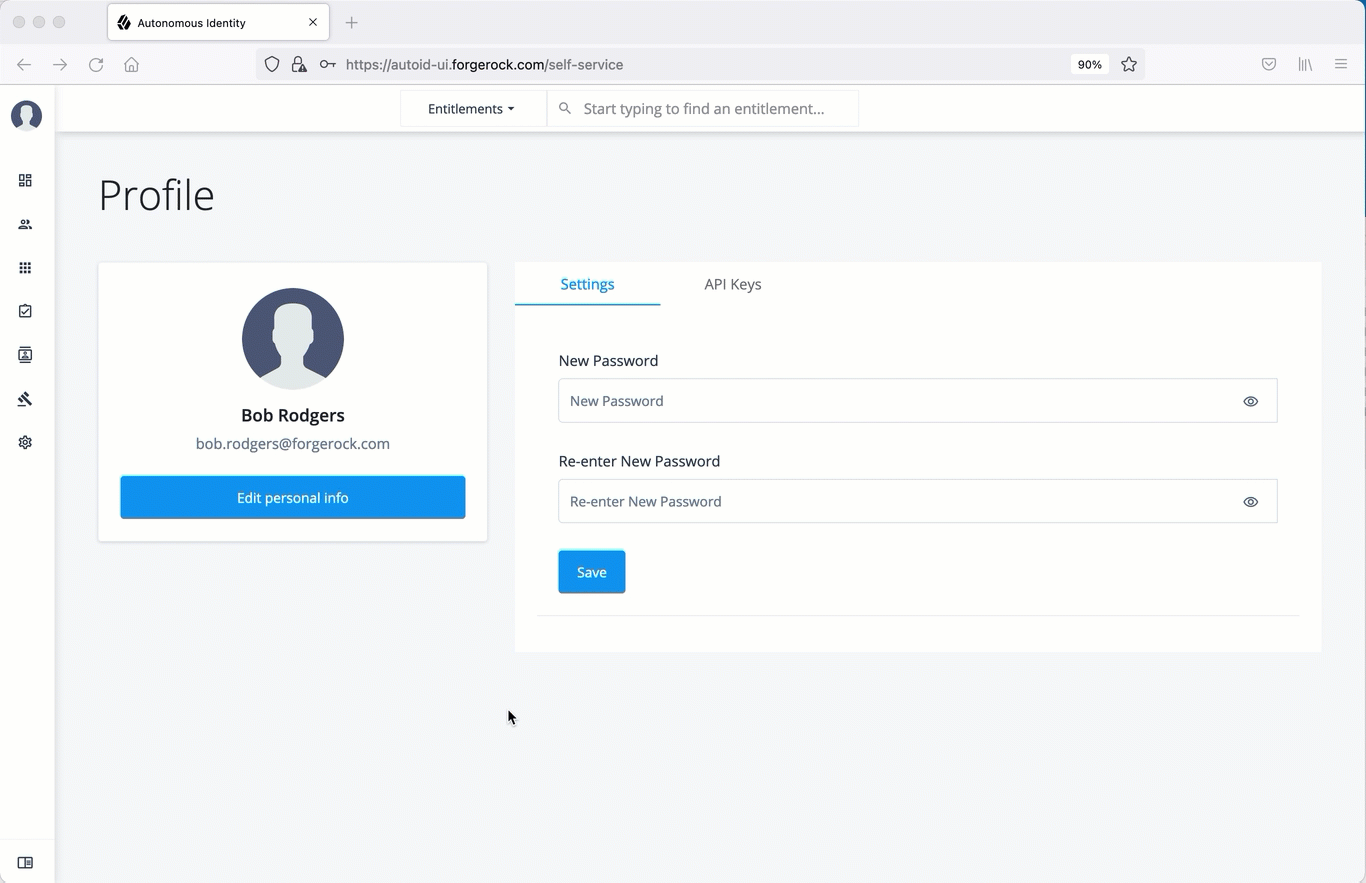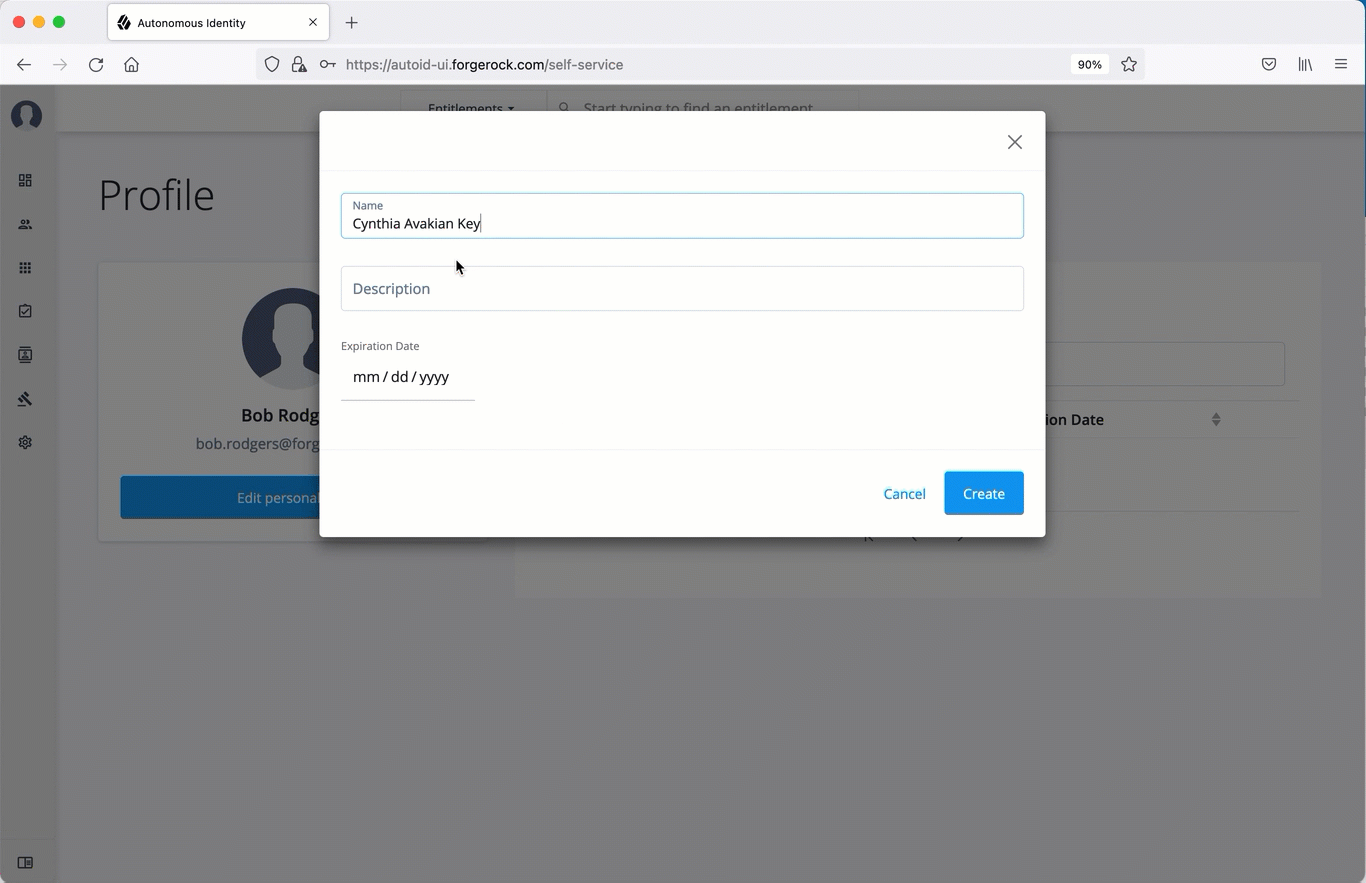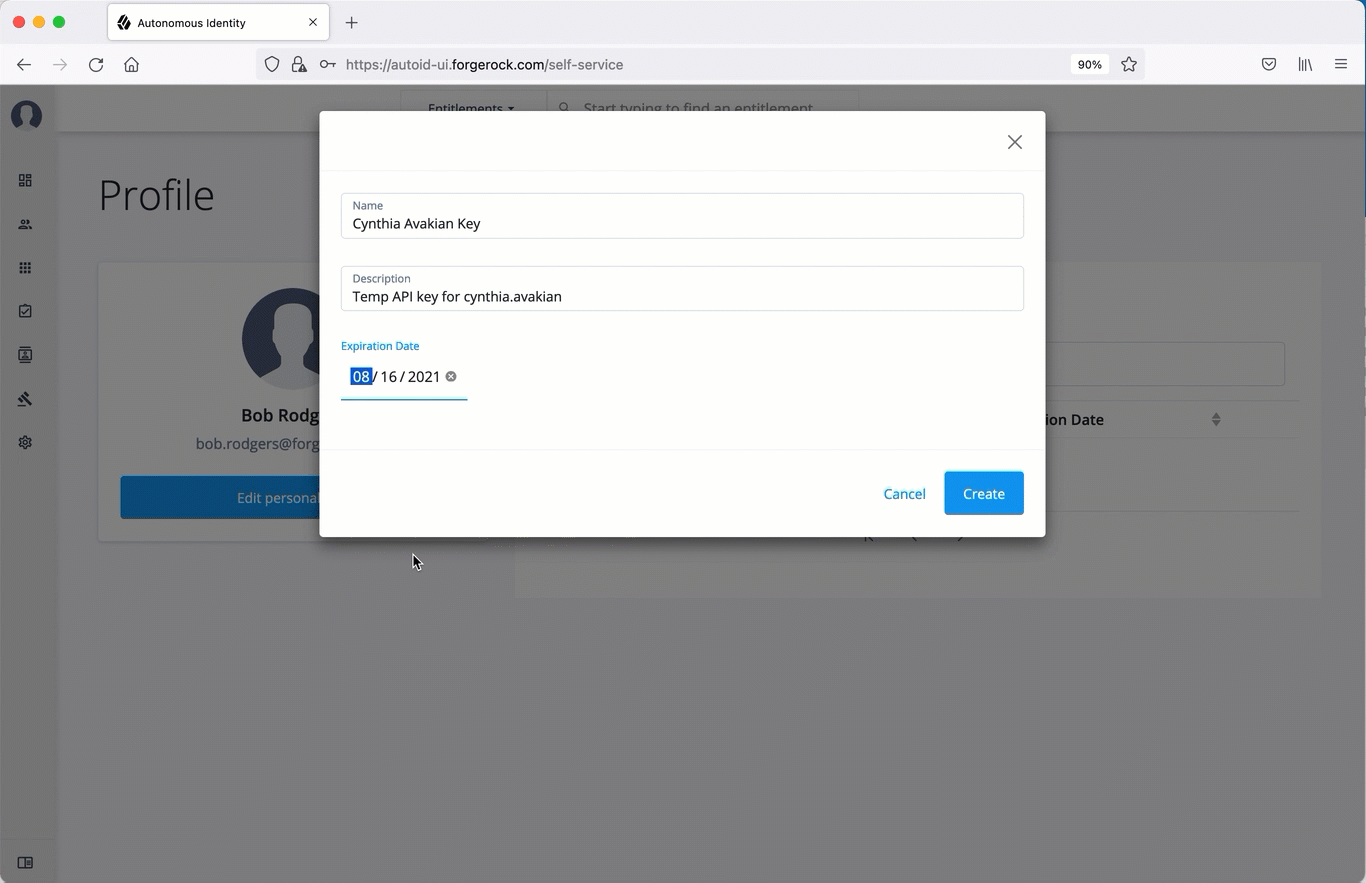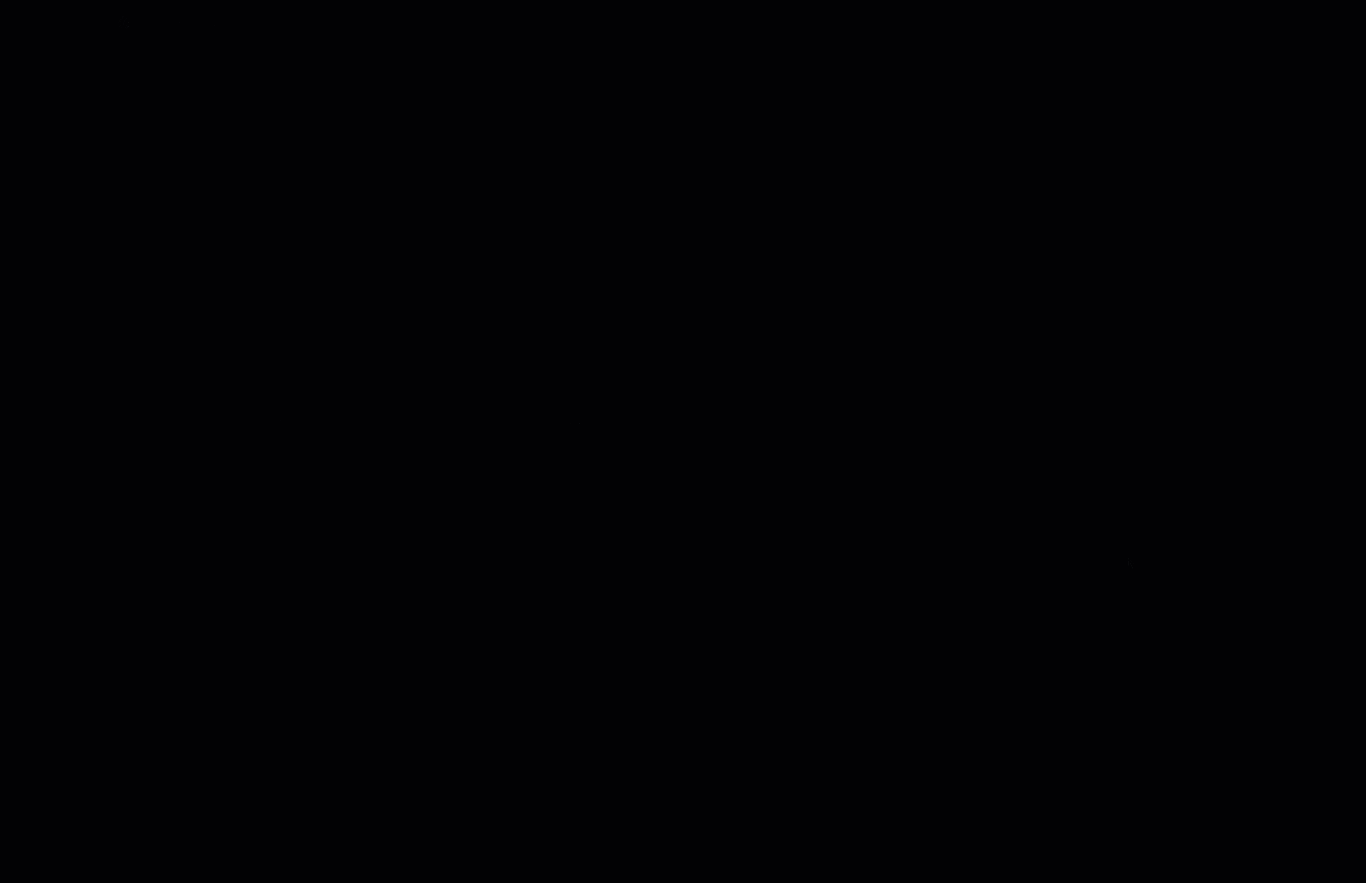
Click Generate API Key.
-
Set the name, description, and expiration date for API key, and then click Create.
-
Make sure to make a copy of the key in the box as it cannot be retrieved once the dialog box is closed. The new API key appears in the list of keys on the API Keys page.
See it in action
Deactivate API Keys using the UI
Administrators can revoke or delete API keys. Use the following procedure to revoke an API key.
-
On the Autonomous Identity UI, click the admin drop-down on the top-left of the page.
-
Click Self Service.
-
Click the API Keys tab.
-
In the Search field, enter the API key.
-
In the list of API keys, click the three dots, and select Revoke. This action deletes the API key for use.
See it in action
Create an API Key using Curl
Administrators can create API keys on the command line using curl commands.
-
Open a terminal, and create an authentication bearer token for an admin user:
curl -k -X POST \ https://autoid-ui.forgerock.com/api/authentication/login \ -H 'Content-Type: application/json' \ -d '{ "username": "bob.rodgers@forgerock.com", "password": "Welcome123" }'
The response is:
{ "user": { "dn": "cn=bob.rodgers@forgerock.com,ou=People,dc=zoran,dc=com", "controls": [], "displayName": "Bob Rodgers", "gidNumber": "999", "uid": "bob.rodgers", "_groups": [ "Zoran User", "Zoran Admin" ] }, "token": "token_value” } -
Set the
TOKENenvironment variable:export TOKEN=token_value
-
Generate a new API key:
curl -k -X POST \ https://autoid-ui.forgerock.com/api/admin/createApiToken \ -H "Authorization: Bearer $TOKEN" \ -H 'Content-Type: application/json' \ -d ' { "name": "Ingest Key", "description": "API key for ingestion endpoints", "expiration": "2022-01-02" }'
The response is:
{ "token": "19412ace-1d99-44b2-88e0-16136fc5c77a" }
API Key Examples
The following curl example illustrates how to use the API key to get a datasource ID for an ingestion job:
-
Obtain an API key from an administrator. See Create API Keys.
-
Obtain the tenant ID using the environment variable.
$ env | grep TENANT_ID TENANT_ID=8700f5cb-eaca-461e-8c2e-245a25f2399d
-
Query Autonomous Identity’s Java API Service (JAS) to obtain a data source ID using the API Key (for example, '1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1'):
curl 'https://autoid-ui.forgerock.com/jas/datasource/search' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/data-sources' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "query": { "sort": [ { "datasource_id.keyword": { "order": "desc" } } ], "size": 10, "track_total_hits": true, "query": { "match_all": {} } } }' \ --compressed \ --insecure
The response includes the datasource ID:
{ "took": 8, "timed_out": false, "_shards": { "total": 3, "successful": 3, "skipped": 0, "failed": 0 }, "hits": { "total": { "value": 1, "relation": "eq" }, "max_score": null, "hits": [ { "_index": "autonomous-iam_common_datasources_latest", "_type": "_doc", "_id": "259b80c7693e92c4c29bd64deac4cd99826d427027645c9413afdb3f083b891d8d34cefaebd5fcf098c066dc1a4da2879d8732d59bfd2e239a285184f8e7a35b", "_score": null, "_source": { "datasource_id": "2d7a6a76-469c-4035-b312-fb1daf104e98", "name": "Showcase-CSV-DS", "sync_type": "full", "icon": "apps", "isActive": true, "entityTypes": { "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/applications": { "uri": { "file": "file:/data/input/applications.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/assignments": { "uri": { "file": "file:/data/input/assignments.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/entitlements": { "uri": { "file": "file:/data/input/entitlements.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/identities": { "uri": { "file": "file:/data/input/identities.csv" } } }, "connectionSettings": { "csv": {} }, "metadata": { "contextId": "scripts", "entityType": "/common/datasources", "primaryKey": "2d7a6a76-469c-4035-b312-fb1daf104e98", "entityPath": "/common/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98", "entityDefinition": "datasources", "namespace": "/common", "branch": "actual", "created": "2021-08-25T03:53:33.634Z", "tenantId": "autonomous-iam" } }, "sort": [ "2d7a6a76-469c-4035-b312-fb1daf104e98" ] } ] } } -
Make sure your client that accesses the JAS configuration has something similar to the following:
public static final String CONFIG_JAS_API_TOKEN = "JAS_API_KEY"; public static final String CONFIG_JAS_TENANT_ID = "TENANT_ID";