Access review
Users can find the UI context for Identity Governance by navigating to /governance from your IDM server URL. Once logged in, the user can find the Administrator dashboard by clicking on the Dashboard link in the Administration section of the navigation sidebar, or alternatively by navigating directly to /governance/#/admin/dashboard.
| Identity Governance does not support internal users for administrative or end-user tasks. To access the product functionality correctly, you must be logged in as a managed user. Internal users will be redirected to a page informing them of this policy. |
Dashboard Overview
To access the Administrator Dashboard, log into Identity Governance as a user with the governance-administrator authorization role. Select Dashboard in the navigation side bar menu under Review Administration.
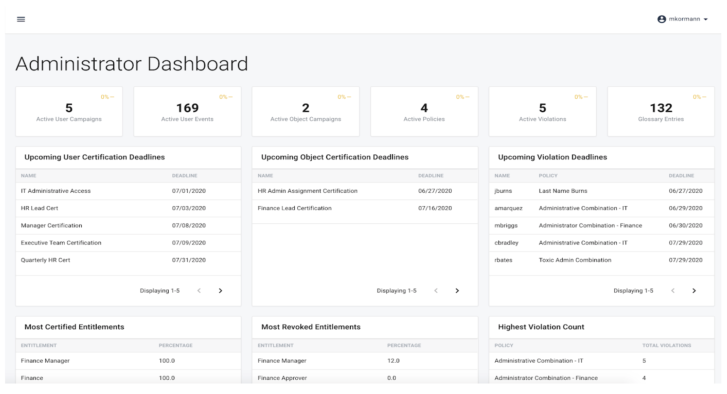
The administrator dashboard offers admin users an overview of the entire state of the Review portion of Identity Governance, presenting statistics on the current count of total certifications, events, and more, as well as some analytical information to keep the administrators up to date on the decisions being made by certifiers.
The statistics shown on the dashboard are updated in one of two ways. Some, which are less intensive on the system to calculate on demand, are loaded in at the time the dashboard is accessed. Others, which look through the entire certification history of the system, are calculated via a scheduled script and are stored in the repository at a configurable interval. The script schedule is defined in the file schedule-script_adminDashboard.json in the openidm/conf directory, where the schedule can be updated to run as often as desired.
The following metrics are displayed as part of the dashboard:
-
Name. title of the metric shown
-
Description. Brief explanation of what the metric shows
-
Action. hether metric is clickable or interactive in some way
-
Key. Reference key for the metric, can be referenced in adminDashboard API call to retrieve a single metric
| Name | Description | Action | Key |
|---|---|---|---|
Active User Campaigns |
Number of current user certification campaigns in flight |
No |
activeUserCampaigns |
Active User Events |
Number of current individual user events in flight (where event is each task within a campaign) |
No |
activeUserEvents |
Active Object Campaigns |
Number of current object certification campaigns in flight |
No |
activeObjectCampaigns |
Active Policies |
Number of active policies defined in the system |
No |
activePolicies |
Active Violations |
Number of current violation tasks with a status of 'in-progress' awaiting action |
No |
activeViolations |
Glossary Entries |
Number of entries defined in the Identity Glossary |
No |
glossaryEntries |
Upcoming User Certification Deadlines |
Table of active user certifications, ordered by most recent upcoming stage deadline |
Yes |
upcomingUserCertificationDeadlines |
Upcoming Object Certification Deadlines |
Table of active object certifications, ordered by most recent upcoming stage decline |
Yes |
upcomingObjectCertificationDeadlines |
Upcoming Violation |
Table of active violations, ordered by most recent upcoming deadline |
Yes |
upcomingViolationDeadlines |
Most Certified Entitlements |
Table of entitlements that have been certified and signed-off, sorted by the percentage of outcomes that are marked as 'certify' |
Yes |
mostCertifiedEntitlements |
Most Revoked Entitlements |
Table of entitlements that have been certified and signed-off, sorted by the percentage of outcomes that are marked as 'revoke.’ |
Yes |
mostRevokedEntitlements |
Highest Violation Count |
Table of policies, sorted in descending order by the number of violations that have been found against the policy. |
No |
highestViolationCount |
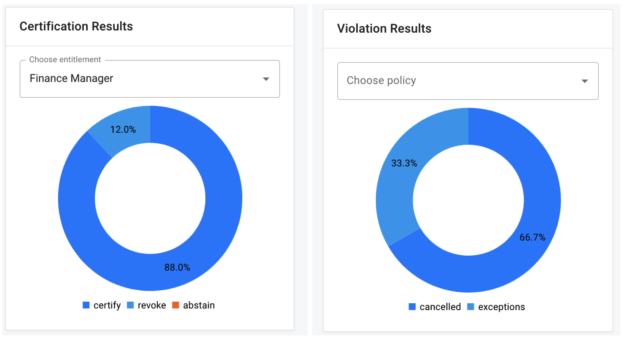
Certification Results |
This chart allows the admin to see the complete breakdown of all certified entitlements within the system, grouped by the certification decision that was made against them. |
Yes |
certificationResults |
Violation Results |
This chart allows the admin to see the complete breakdown of all violations acted on within the system, grouped by the decision that was made against them. |
Yes |
violationResults |
Metric Display Types
Metrics are displayed on the dashboard using one of three different display types, each of which is described below.
Stat Card
The top row of metrics on the dashboard are all displayed as stat cards. This display is used for basic counts or totals of things within the Access Review environment such as Active User Campaigns or total Glossary Entries.
A single stat card displays the metric value centered on the card, with the title displayed along the bottom. The percentage on the top right of the card shows the difference in value between the most recent scheduled run of the admin dashboard script and the current value. Note that the longer the time period between iterations of the scheduled script, the more informative these numbers tend to be.
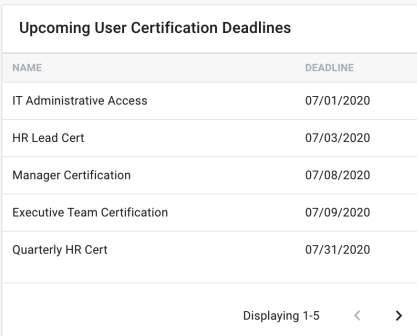
Table
Dashboard metrics that are displayed within a table view offer a paginated and interactive view to a sorted list of campaigns, violations, or entitlements within the system. The tables are all defaulted to show five (5) rows per page, and can be individually advanced through sorted pages by using the navigation arrows found at the bottom right of the table.
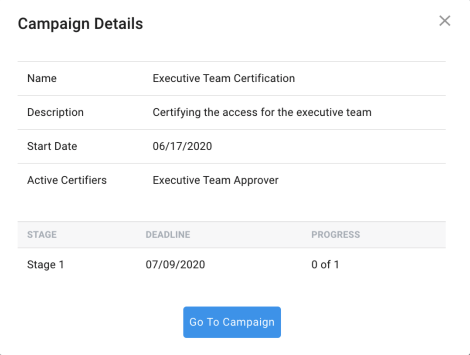
Most of the tables within the view offer the ability to click on a given row and view more information about the item chosen. Tables of certifications offer you a brief preview of the certification campaign, as well as a button that will take the administrator directly to the administration view of the campaign.
Violation tables, when clicked, will show the administrative view of a violation that is available to admins when accessed from the Policies and Violations table.
Finally, the entitlement tables will display the standard metadata screen view when clicked. This information is grabbed directly from the corresponding glossary entry for the certified entitlement.
Pie Chart
Metrics displayed via a pie chart show the division of entitlement certification of violation details. Upon initial installation, these charts will not appear populated until certifications and/or violations have been created and signed-off/completed and a scheduled scan of the adminDashboard script has been run. Each chart contains a select box above the chart that allows administrators to target an entitlement or policy in order to see the data that pertains only to that single object.
User and Object Certifications
User and object certifications target individual users or managed objects for certification. Certifications allow one or more certifiers to review a target’s attributes and properties from the IDM schema. For user certifications, attributes and access defined within a linkey system may be reviewed in the applications section, and for object certifications glossary metadata as defined in the Identity Glossary can be certified. Certifiers can make a certification decision as to whether they want to certify or revoke a given entitlement, or abstain from making a choice entirely.
Creating New Certification Definitions
Create a user certification:
-
For User Certifications, navigate to the User Certifications screen by clicking on its link on the navigation sidebar.
-
From the User Certifications page, click the New Certification button in the actions row of the table.
-
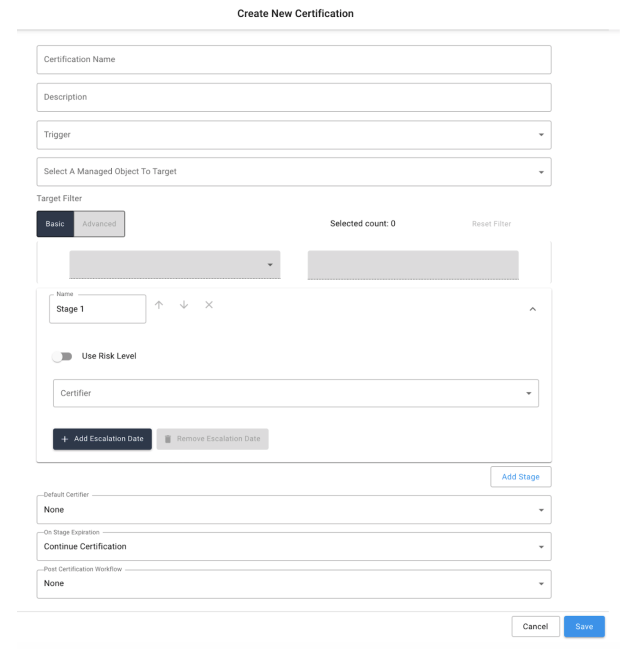
On the Create New Certification screen, fill in each of the required fields. Additional details on the available fields are presented below.
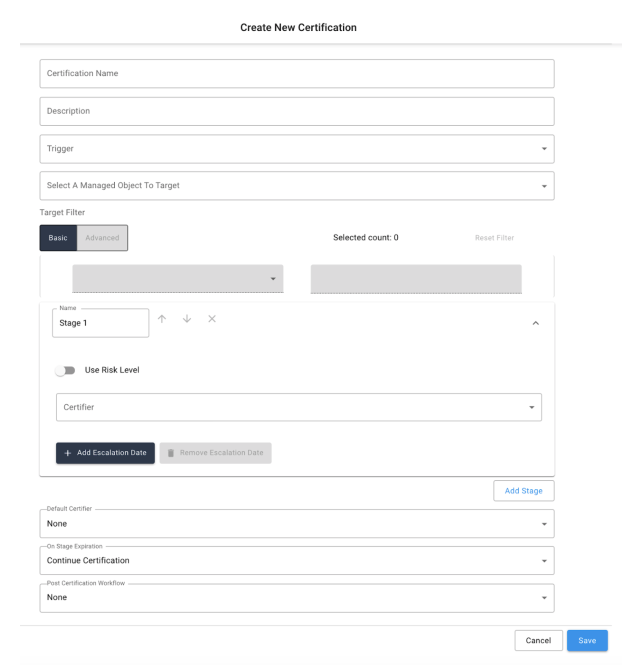
-
Certification Name. (Required). Title for the certification that will appear on all summary pages.
-
Description. Provides additional details about the purpose of the certification for certifiers.
-
Trigger. (Required). Identifies when the certification is created. Options are:
-
Ad-Hoc. Generates a new certification immediately after submitting the current form and can only be triggered once.
-
Scheduled. Generates a new certification each time a specified time duration has passed. When selecting the
Scheduledoption, additional fields become available, allowing duration to be specified. Note: For more information on scheduling events, refer to section Scheduling Events. -
Event-based. Generates a certification based upon criteria evaluated when a user’s attributes or managed object is updated. After selecting an Event-based trigger, select ‘Open Expression Builder’ under Event Trigger to identify the criteria for triggering certification generation. Note: For more information on building expressions, refer to section Expression Builder.
-
-
Target Object Type. (Object Certifications Only). Object certifications must specify which managed object type will be targeted in the campaign. A certification can target any number of instances of the chosen object type, but it can only target one type per campaign. All managed objects within the system are eligible to be targeted by an object certification with the exception of ‘user’ (which is handled separately.) As noted in other places within this document, it is highly recommended that any object type you wish to target in a campaign have at a minimum a name and description as part of its schema properties in order to display properly within the certification screens.
-
Target Filter. (Required). Identifies filter for targeting a specific subset of users for the certification. The current number of users that are currently targeted by the given expression is displayed next to the ‘User Filter’ text. The ‘Reset Filter’ option is available on the right-hand side of the filter, which will restore the filter to its default state. The filter uses the two following categories: Basic and Advanced.
-
Basic. Upon selecting, the left dropdown is populated with the following options:
-
User/Single Object. Allows certification to be filtered to target only one specific user or managed object. Upon selecting, the right input box becomes available to enter in a username or object name.
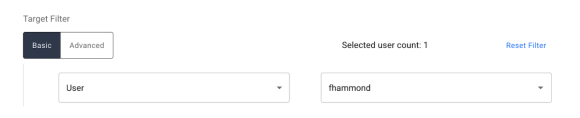
-
Users with manager. (User Certifications Only). Allows certification to be filtered to any user with a specified manager. Upon selecting, the right input box becomes available to enter in a username corresponding to the manager.
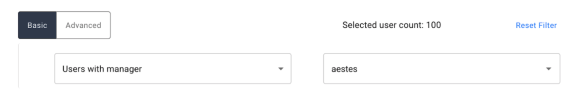
-
Users with application. (User Certifications Only). Allows certification to be filtered to any user assigned to a specified application. Upon selecting, the right select box becomes available to select the name of the connected application.
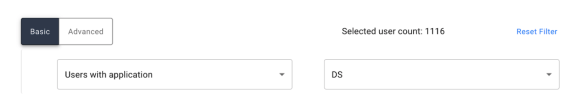
-
All Users/Every Object. Allows certification to be run with no filter and target all users/objects of the type selected.
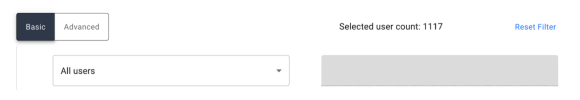

-
Filter by provisioning/authorization role. (User Certifications Only). Allows certification to be filtered to any user assigned to a specified instance of either a provisioning role or an authorization role. Upon selecting, the right input box becomes available to enter in the name of the role.
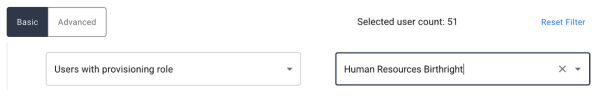
-
-
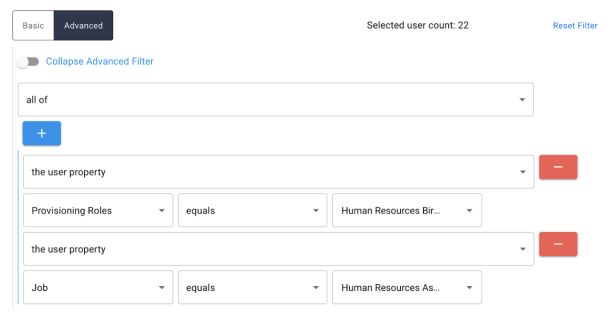
Advanced. Upon selecting, the advanced expression builder is displayed. The following options for creating a custom expression are available within the certification creation advanced target filter. For a more detailed description of what the individual options determine, refer to section Expression Builder.
-
User/Object property. Choose from any user attribute
-
User application. (User Certifications Only). Allows choice of any connected application to be selected from the dropdown menu
-
All of. Match all of the nested rows.
-
Any of. Match at least one of the nested rows.
-
None of. Negate the expression in the nested row.
-
All users/Every object. Select all users.
-
-
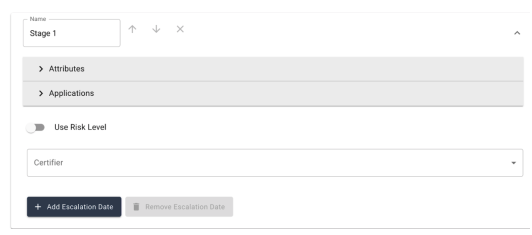
Certification Stages. A certification may have one or more stages. Each selected certifier is responsible for one stage, and additional stages may be added as needed (by selecting the ‘Add Stage’ button.), while selecting. Optionally, stage names may be modified by editing the text within the Name input field.
-
Stage icons. Name Input: Change the stage name
-
Up/Down arrows (next to the stage name): Change the stage order
-
‘X’ icon: remove a specific stage
-
Caret: (at the top left of each stage): collapse/expand details for a given stage
-
-
Entitlement Filter. Specifies the entitlements/access that will appear to certifiers within the given stage. For user certifications, the attributes/applications that appear in these sections correspond to those that are defined with a key of certifiable set to true in the glossary metadata. For object certifications, the entire managed object schema for the selected type will be available to choose as certifiable in any campaign.
-
Attributes. The entitlements on the user or object that are tracked and stored by IDM; the managed object properties defined on the object’s schema. Basic attributes and single object relationships are included in a certification stage via a basic checkbox. Multi-valued relationship objects are chosen and included as shown below:

-
Relationships. When a relationship attribute is selected, add and remove buttons appear below the attribute name, allowing a complex target expression to be built. The number of objects currently selected is displayed to the right. If no expression is specified, all possible options are selected.

When choosing to filter a multi-valued relationship, the administrator is decided which values of the managed object will be eligible for inclusion within this certification. Any objects that match this filter and belong to a target as part of the selected attribute will appear in the campaign, while those excluded by the filter won’t, even if a target user has that relationship. The following operators are available:
-
Equals - Exact match of property
-
Contains - Property value contains string
-
Does Not Contain - Negation of above
-
Starts With - Property value starts with string
-
Does Not Start With - Negation of above
-
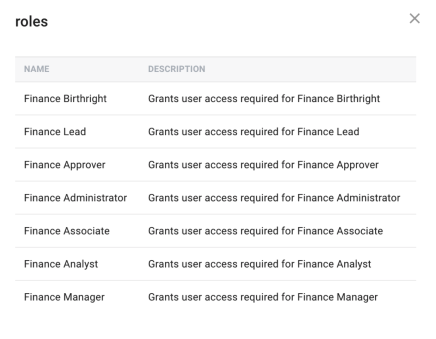
Selected Roles: Clicking on the number of objects currently selected on the top right of the attribute row will display the targeted screen. This screen shows the names and descriptions of the items selected.
-
-
-
Applications. (User Certifications Only). The external applications and user data that are tracked by IDM through a connected system. To populate the applications list with certifiable systems, a glossary system entry must be created for the connector and assigned a key of certifiable. In addition, the attributes that can be certified must also correspond to a system-attribute entry with a key of certifiable set to true.
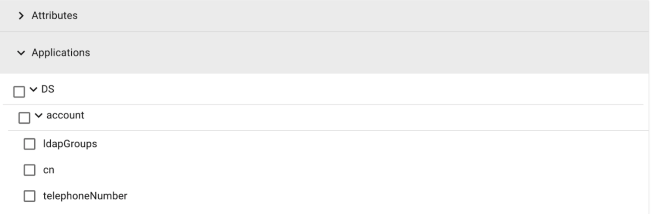
-
Metadata. (Object Certifications Only). The entries within the Identity Glossary entry for the targeted managed object(s). Since the keys and entries that exist within the glossary are entirely arbitrary and could contain any given values across multiple instances of the same object, the administrator has the option to either not certify metadata at all, or to include all existing metadata to be certified by the certifier(s).
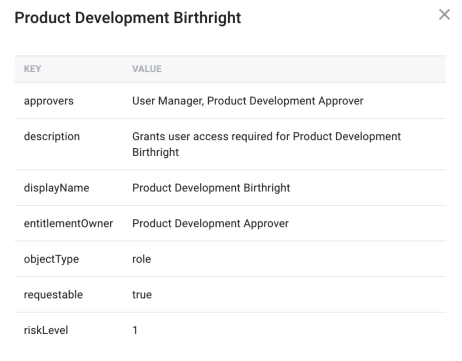
-
-
Risk Level. Specifies a filter for the entitlements within the given stage. Only certifications with entitlements that match the specified levels of risk will be generated. For more information on how Low, Medium and High risk levels are defined, see System Settings. Risk level on an entitlement basis is defined within the identity glossary. Relationships to managed objects will use the corresponding glossary entry of type object, while managed user properties with specific values will use glossary entries of type identity-value to define their risk.

The following results will occur from selecting the listed filter combination:
-
Use Risk Level off. Risk level will not be considered when filtering entitlements in a given campaign. Entitlements with a risk level defined at any level, as well as entitlements without a risk level defined will be included.
-
Use Risk Level on, one box selected. Only items that match that risk level range will be included.
-
Use Risk Level on, two boxes selected. Only items that match either level selected will be included.
-
Use Risk Level on, all selected. All items that have a risk level defined will be included in certification. Entitlements without a risk level defined will be excluded.
-
-
Certifier. (Required). Identifies to whom the certification stage will be assigned once generated, with the following available options:
-
User. User certifier will assign the generated certification stage to a specific user and a single user will certify all targets. When specifying a user, autocomplete will help identify the user login for the assignment.

-
Group. Certifier assigns generated certification stage to a group of specified users. All targets will be certified by users with the given group role attribute. To specify a group, select an available role in the choose certifier drop-down menu. See the section in the post-installation steps on membership property for information on how group membership is determined.

-
User Manager. Certifier assigns generated certification stage to users designated by the Manager attribute. Their managers will certify all targets.
-
Previous Certifier’s Manager. Certifier assigns generated certification to the manager of the user specified in the preceding stage. Note that this option will be disabled for the first stage in the sequence, or if the preceding stage has the Certifier field set to ‘Group.’
-
Entitlement Owner. (User Certifications Only). Certifier assigns generated certification to the entitlement owner of the included entitlements. The certification targets for the stage will be split among the users/roles who are set as the owner of the entitlement in the Access Review Glossary (glossary key of entitlementOwner, with a type of managed object.) This option will allow for multiple certifiers to be assigned a subset of entitlements for a given certification within a stage.
-
Glossary Key. (Object Certifications Only). This option allows administrators to specify any glossary key of their choosing to become the certifier for the selected stage. This allows for any defined key, or multiple keys using subsequent stages, to be certifiers for entitlements in a given stage. As with entitlement owner certifications, if a given entitlement has the defined key in its glossary entry, that key is defined as type managed object, and that managed object is a user or role, then that person or role will be assigned as the certifier. If the entitlement does not have the entry defined as described above, the entitlement will not be included in the stage or will go to the default certifier if specified.
-
-
Deadline. (Required). Specifies how long certification stage should remain active. After the specified date or duration, the certification stage will expire. Certification will then either 1) move to the next stage or 2) expire and become unavailable for modification, based on which option has been specified for the ‘On Stage Expiration’ field.
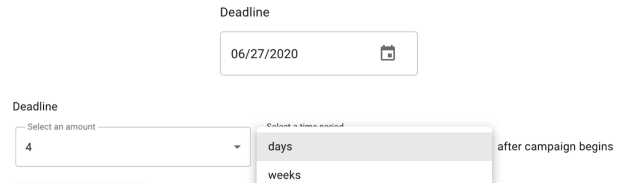
-
Escalation Schedule. Administrators are now able to define a configured schedule of escalation notifications that are delivered to a specific party at a specific time period before the certification expires.
-
Add an escalation date. To add an escalation notification to the schedule, simply click the ‘Add Escalation Date’ button located on the stage form beneath the deadline field. This will populate a single instance of the escalation form which consists of the following fields:
-
Amount. The numeric value that combines with the chosen time period to determine the time before the certification expires that the notification will be sent.
-
Time period. Days or weeks before certification expires.
-
Escalation owner type. Who will be notified of the escalation. Choice of either user, group, or manager. Manager in this case refers to the manager of the certifier for the given user events.
-
Choose escalation owner. If owner type is user or group, select the user or role that will receive the notification.
In order to add an additional escalation date the preceding form must be completed before the add button is enabled again. Escalation dates must be added in order of furthest from the deadline to closest.
-
-
Escalation Schedule. Administrators are now able to define a configured schedule of escalation notifications that are delivered to a specific party at a specific time period before the certification expires.
To add an escalation notification to the schedule, simply click the ‘Add Escalation Date’ button located on the stage form beneath the deadline field. This will populate a single instance of the escalation form which consists of the following fields:

-
Amount. The numeric value that combines with the chosen time period to determine the time before the certification expires that the notification will be sent.
-
Time period. Days or weeks before certification expires.
-
Escalation owner type. Who will be notified of the escalation. Choice of either user, group, or manager. Manager in this case refers to the manager of the certifier for the given user events.
-
Choose escalation owner. If owner type is user or group, select the user or role that will receive the notification.
In order to add an additional escalation date the preceding form must be completed before the add button is enabled again. Escalation dates must be added in order of furthest from the deadline to closest.
-
-
Remove escalation date. To remove the most recent escalation date, click on the ‘Remove Escalation Date’ found next to the add button.
-
-
Default Certifier. Specifies a default certifier for the entire campaign. If a default certifier is set, then stage events with no owner will be assigned to that certifier. If no default certifier is set, events with no owner will receive the status ‘No Certifier'. If no default certifier is set, events with no owner will receive the status ‘No Certifier.’
-
On Stage Expiration. If a stage is not completed before the deadline, the events of that stage will be marked as expired. The ‘On Stage Expiration’ field determines how the same events in subsequent stages are affected.

-
Continue Certification. The expired event(s) will not be affected in the next stage of the campaign; the next certifier will be able to take action as they would normally.
-
Expire Throughout. The event(s) will be expired for all future stages within the campaign. This will prevent any future certifiers of the campaign to take action on the event.
-
-
Post Certification Workflow. Identifies an automated remediation task for handling revocations from the certification. Note: For more information on remediation tasks, refer to section Remediation Tasks.

-
-
Modifying Certification Definitions
-
To modify an existing certification definition, click on the User or Object Certifications link under the administrative section of the side navigation bar.
-
Choose either the Scheduled or Triggered tabs.
-
The table will be populated with all existing scheduled or triggered certification definitions that exist within the system.
-
To modify a given certification, click on the row that contains the desired campaign to open up the edit screen. This screen will be the same as the one used for creating certifications, with the certification data from the given campaign populated.
-
Once you have finished making your adjustments to the certification, click Save at the bottom of the form to complete the update. Note: For additional information on fields to update on this form, refer to section Creating New Certification Definitions.
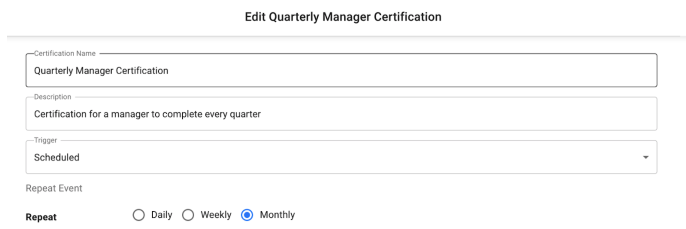
Certification Tables
To review the different certifications tables, click on the User or Object Certifications link under the Administrative section of the side navigation bar. The information below will describe the columns and functionality of each of the existing tables.
-
Active Certifications
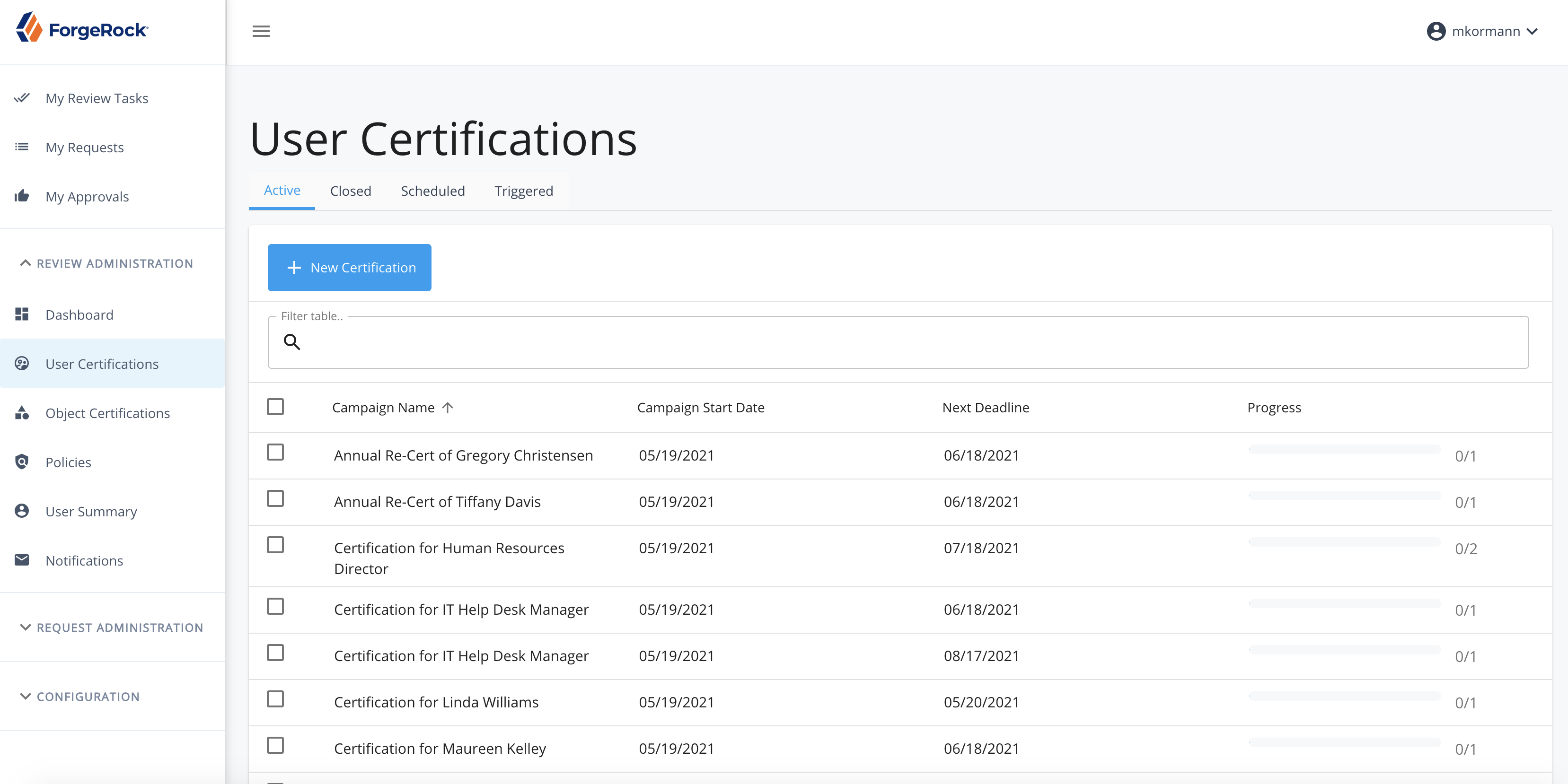
-
Action Buttons
-
New Certification. Create a new certification campaign.
-
Cancel Certification. Cancel an in-progress campaign.
-
-
Display Columns
-
Campaign Name
-
Description: Name of the active campaign
-
Searchable: Yes
-
Sortable: Yes
-
-
Object Type (Object certifications only).
-
Description: Type of managed object the campaign is targeting
-
Searchable: Yes
-
Sortable: Yes
-
-
Campaign Start Date
-
Description: Date the campaign was initially kicked off
-
Searchable: No
-
Sortable: Yes
-
-
Next Deadline
-
Description: Deadline of the earliest active stage (future stages may have a deadline further out than this date.)
-
Searchable: No
-
Sortable: Yes
-
-
Progress
-
Description: Shows the number of events completed out of the total number of events across all stages of the campaign. Note that to be considered completed, an event must be reviewed and signed-off by the certifier.
-
Searchable: No
-
Sortable: No
-
-
-
-
Closed Certifications
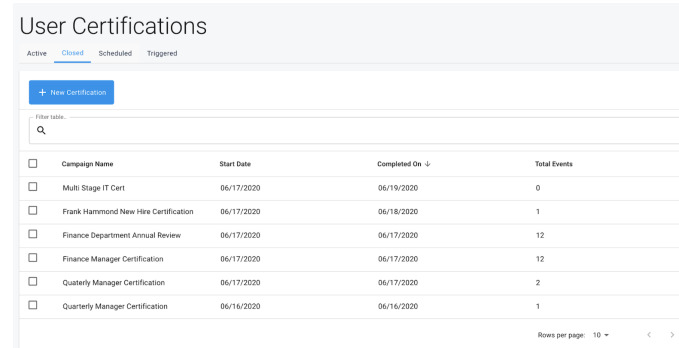
-
Action Buttons
-
New Certification
-
-
Display Columns
-
Campaign Name
-
Description: Name of the closed campaign
-
Searchable: Yes
-
Sortable: Yes
-
-
-
Object Type (Object certifications only)
-
Description: Type of managed object the campaign is targeting
-
Searchable: Yes
-
Sortable: Yes
-
-
Campaign Start Date
-
Description: Date the campaign was initially kicked off
-
Searchable: No
-
Sortable: Yes
-
-
Completed On
-
Description: Date that the last stage of the campaign was completed and signed-off
-
Searchable: No
-
Sortable: Yes
-
-
Total Events
-
Description: Total events in campaign
-
Searchable: No
-
Sortable: No
-
-
-
Scheduled Certifications
-
Action Buttons
-
New Certification
-
Cancel Certification
-
-
Display Columns
-
Campaign Name
-
Description: Name of the scheduled campaign
-
Searchable: Yes
-
Sortable: Yes
-
-
-
Next Run Date
-
Description: Date that the scheduled campaign will start based on its defined scheduler object
-
Searchable: No
-
Sortable: Yes
-
-
-
Triggered Certifications
-
Action Buttons
-
New Certification
-
Cancel Certification
-
-
Display Columns
-
Campaign Name
-
Description: Name of the scheduled campaign
-
Searchable: Yes
-
Sortable: Yes
-
-
-
Canceling Active Campaigns
To cancel an active campaign from the “Active” tab, check the checkbox next to the row of the campaign or campaigns that you wish to cancel. Note that once at least one row selected, the cancel certification button in the table’s action row will become enabled. Once this button is clicked the administrator will be asked to confirm their choice, and if done so, the certification campaigns will be cancelled.
Deleting Certification Definitions
Deleting a certification definition from the scheduled or triggered tab of a Certifications page works exactly as described above for cancellation of active campaigns.
Reviewing Active Certifications
From the active certifications tab of the User or Object Certifications table, search or sort the table until you find the desired campaign that you wish to review. Clicking on that certifications row will take you to the administrator certification list for that campaign.
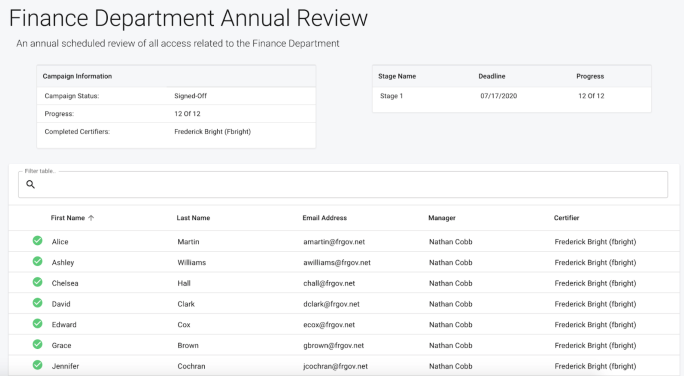
Select a certification from the Active Certifications list to display additional information. The following details will be displayed:
-
Campaign Name. Name of the campaign
-
Campaign Description. Description of the campaign
-
Campaign Information. Displays a summary of the campaign with the following information:
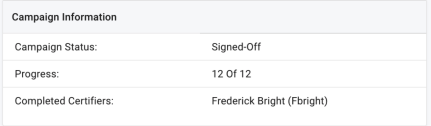
-
Campaign Status. Identifies the current state of the certification. Values may include In-Progress, Cancelled, Signed-off, or Expired
-
Progress. The number of campaign events signed-off against the total number of events in the campaign
-
Active Certifiers. Any certifier with an in-progress event assigned to them that is part of the given campaign. Note this does not include certifiers with a pending (future stage) event assigned to them.
-
Completed Certifiers. Any certifier that has completed and signed-off on an event that is part of the given campaign.
-
-
Stage Information. Displays a breakdown of each stage within the certification campaign with the following information:
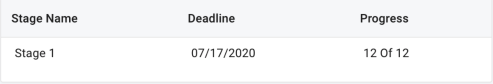
-
Stage Name. Name assigned to the stage
-
Deadline. Date that stage is set to or did expire
-
Progress. The number of stage events signed-off against the total number of events in the stage
-
-
Stage Stepper. Shows a chronological visual of the certification stages. By selecting a stage node, the page will be updated to reflect data for the selected stage.

-
Target List. List containing all targets for the certification. Each line contains a summary of the targeted user or object with the following information:
-
Status icon. The status of the current target’s event for the selected stage. The following statuses are possible:
-
Pending
-
Incomplete
-
Certified
-
Certified, signed off
-
Revoked
-
Revoked, signed off
-
Abstained
-
Abstained, signed off
-
Cancelled
-
No Certifier
-
Expired
Each status is displayed via a circular icon, and may have a different color or fill depending on the individual status. Certified statuses will be colored green, revoked colored red, and abstained colored yellow. The difference between when a normal value and the signed-off version of that value is displayed, the normal version will be displayed when all actions on an event have been completed, but the certifier has not yet signed off on it. After sign-off, the signed off version of the icon will be displayed. This allows the administrator to have a little more insight at this level into the progress of the campaign even before any sign offs occur.

Note that each icon will display a tooltip with the display status text if the administrator hovers over the icon.
-
-
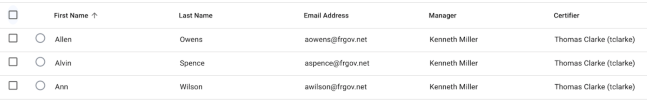
Displayable Target Info Columns. The information that displays in the certification list table may vary depending on certification type and the special displayInUserInfo key in the glossary on identity objects.
For object certifications these displayable columns will always be name and description, so it’s highly recommended that these attributes exist on any custom managed object that you wish to certify
For user certifications, the displayable columns will always include at least the user’s givenName, sn, and email address, as well as any user attribute that has a glossary entry of type identity in the glossary and the displayInUserInfo boolean key set to true. Note that this key will not prevent you from displaying relationship attributes in the target list table, however with the exception of manager these attributes are not supported to display properly.
-
Claimed By. If the certifier for the given stage is a group, this column will display to inform the administrator as to which single user, if any, has claimed the given event.
-
Certifier. The user or role who is the certifier for the target event.
-
Reassigning Active Certification Events
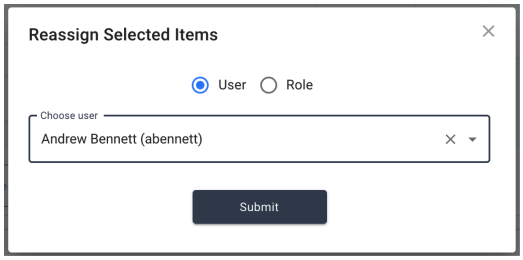
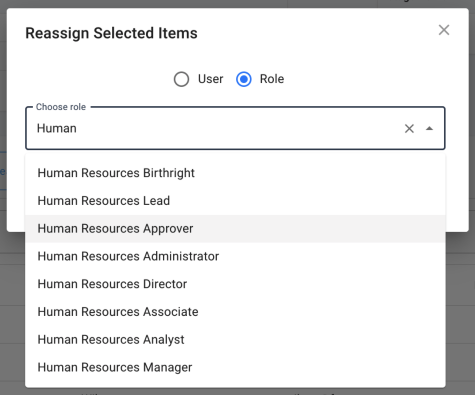
Administrators have the ability to reassign active or pending certification events from the certification list for a given campaign. The admin has the option to either reassign all given events within a given campaign, or to select one or more rows within the target list table and reassign only those selected. The buttons to reassign the events are found in the action buttons section of the certification list table.

Once the administrator has clicked on one of the available buttons to reassign, a small dialog box will appear with a few options for selecting the new certifier. The administrator can choose to reassign to an individual user or a group. When searching for a user, the administrator can use any of the properties made available and searchable via the User Name Display Format setting, while group roles are searchable by name.
| Reassignment of Entitlement Owner user certifications can not be done on the certification list page. For reassignment of these certifications, you can use the User Summary page reassignment function when the entitlement owner is a user. For role entitlement owners, it is recommended to add an appropriate user to the role assigned, or to reconfigure your glossary data to reflect the appropriate owner and recreate the certification to ensure integrity of the certification process. |
Reviewing Active Events
Select a target from the certification target list to display the complete event details view of the certification in a dropdown page. This is the same interface that is displayed to the end users when certifying a target, with some slight adjustments to what actions are available. The following information is displayed:
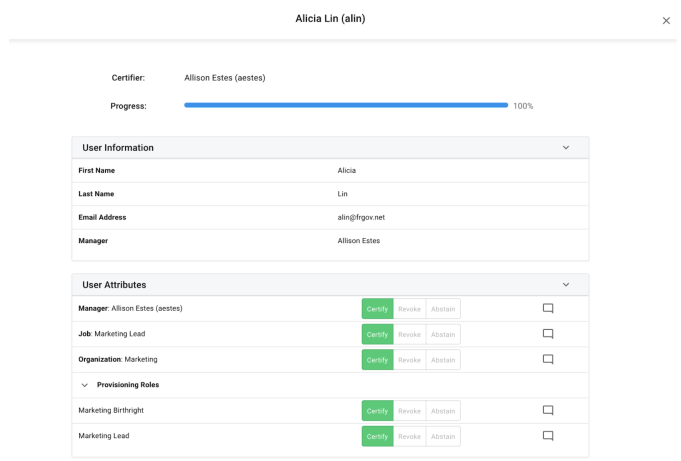
-
Event Details. The section at the top of the page will display details about the given event’s certification progress. It will include some or all of the following information:
-
Stage Selector. If the campaign has multiple stages, the stage stepper selection bar will be shown to allow the administrator to toggle between stages.
-
Certifier. The certifier for the event, if a single user or role
-
Active Certifiers. If an entitlement owner certification, shows the certifiers for the event that are active (have tasks to complete).
-
Claimed By. If the event has a role certifier and is claimed, displays the single user who has claimed it
-
Completion Date. Date and time that the event was signed off
-
Progress Bar. The progress bar for the event
-
-
User Information. Details a summary of the target of the event with the following information. Note that more attributes may appear in user certifications if the displayInUserInfo boolean key is set to true on the glossary entry for the identity attributes:
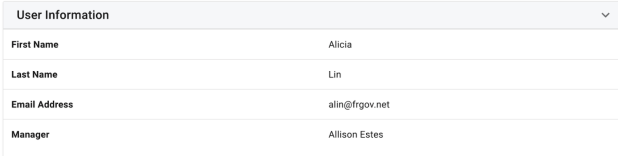
-
User certifications
-
First Name: First name of the target user
-
Last Name: Last name of the target user
-
Email Address: Contact information of the target user
-
Identity attributes set to display as described above
-
-
Object certifications
-
Name: Name of the object
-
Description: Description of the object
-
-
-
User/Object Attributes. Contains attributes to be certified for the target of the event. Attributes that are single-valued will be listed in a Name: Value format, while attributes that are multi-valued will appear underneath a parent row with the attribute name listed. These attributes with parent rows can be collapsed and expanded by clicking on the expand icon to the left of the attribute name.
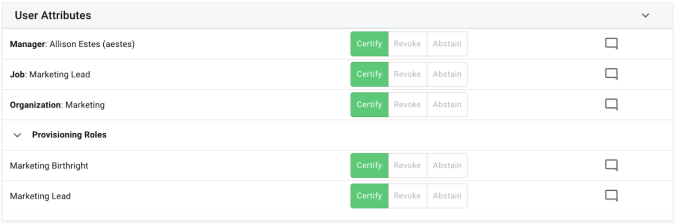
Each row contains the following information:
-
Attribute Name and/or Value
-
Each attribute name and value is clickable by the administrator to see any attached metadata that belongs to the given item. Those items that do not have a corresponding glossary entry will display a page informing the administrator that no entry exists. Note that in object certifications, only the value will allow for displaying metadata as individual object schema attributes do not have direct metadata definitions.
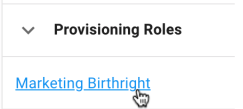
For object certifications, when certifying an object that has a relationship to an out-of-the-box ForgeRock managed assignment, the display of those entitlements within the certification table is slightly altered from any other type of entitlement. For each assignment, any entry in the attributes property of that assignment will be displayed in a readable format below the assignment name. This allows the certifiers to see exactly what access is being provisioned via this assignment, in order to make their decision easier. 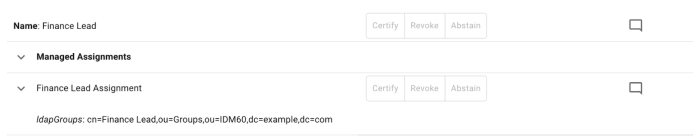
-
-
Certification Action Buttons. These buttons, disabled for administrators, will show the result of the certification action taken on each item if one has been made. If no button is selected and filled, then no decision has been made for that item. The buttons included are listed below:
-
Certify
-
Revoke
-
Abstain
-
-
Comment Icon. The comment icon will either be unfilled if no current comments exist, or have mini comment lines inside of the icon to indicate there are existing comments (pictured below). The administrator can click on the comment icon to display the existing comments, and also to add a new comment to that entitlement.

-
-
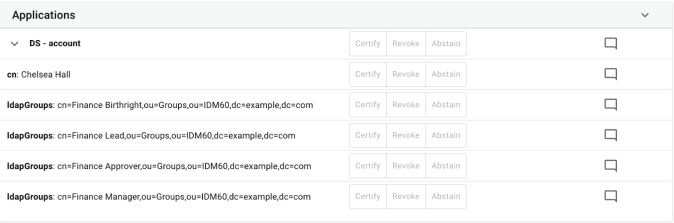
Applications (User Certifications only). Contains attributes within connected systems to be certified for the target user.
-
Attribute Name and/or Value. Each attribute name and value is clickable by the administrator to see any attached metadata that belongs to the given item. Those items that do not have a corresponding glossary entry will display a page informing the administrator that no entry exists.
-
Certification Action Buttons. These buttons, disabled for administrators, will show the result of the certification action taken on each item if one has been made. If no button is selected and filled, then no decision has been made for that item. The buttons included are listed below:
-
Certify
-
Revoke
-
Abstain
-
-
Comment icon. The comment icon will either be unfilled if no current comments exist, or have mini comment lines inside of the icon to indicate there are existing comments (pictured below). The administrator can click on the comment icon to display the existing comments, and also to add a new comment to that entitlement.
For more information on Comments, refer to section Comments. 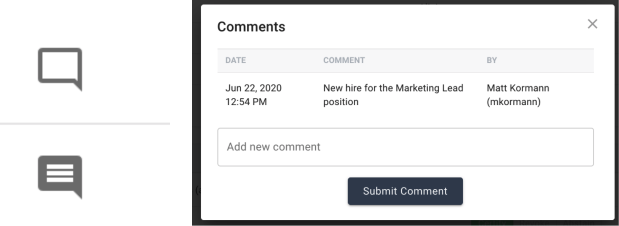
-
-
Metadata (Object Certifications only). Contains each metadata entry that exists within the glossary entry for the target object.
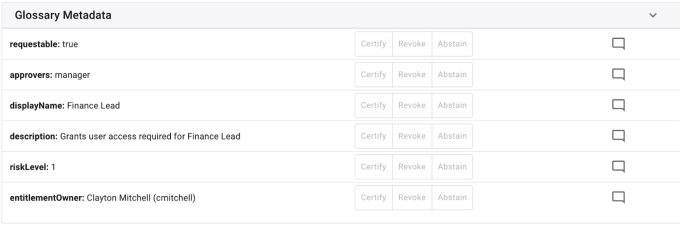
-
Metadata Key and Value. Displays the glossary entry in [Key]: [Value] format for the certifier to act on. Those entries in the glossary that are of type managed object will be converted to a displayable format if possible.
-
Certification Action Buttons. These buttons, disabled for administrators, will show the result of the certification action taken on each item if one has been made. If no button is selected and filled, then no decision has been made for that item. The buttons included are listed below:
-
Certify
-
Revoke
-
Abstain
-
-
Comment icon. The comment icon will either be unfilled if no current comments exist, or have mini comment lines inside of the icon to indicate there are existing comments (pictured below). The administrator can click on the comment icon to display the existing comments, and also to add a new comment to that entitlement.
For more information on Comments, refer to section Comments. 
-
Reviewing Closed Certifications
From the closed certifications tab of the User or Object Certifications table, search or sort the table until you find the desired campaign that you wish to review. Clicking on that certification’s row will take you to the administrator certification list for that campaign.

Select a certification from the Closed Certifications list to display additional information on the campaign. The following details will be displayed:
-
Campaign Name. Name of the campaign
-
Campaign Description. Description of the campaign
-
Campaign Information. Displays a summary of the campaign with the following information:

-
Campaign Status. Identifies the current state of the certification. Values may include In-Progress, Cancelled, Signed-off, or Expired
-
Progress. The number of campaign events signed-off against the total number of events in the campaign
-
Completed Certifiers. Any certifier that has completed and signed-off on an event that is part of the given campaign.
-
-
Stage Information. Displays a breakdown of each stage within the certification campaign with the following information:

-
Stage Name. Name assigned to the stage
-
Deadline. Date that stage is set to or did expire
-
Progress. The number of stage events signed-off against the total number of events in the stage
-
-
Stage Stepper. Shows a chronological visual of the certification stages. By selecting a stage node, the page will be updated to reflect data for the selected stage.

-
Target List. List containing all targets for the certification. Each line contains a summary of the targeted user or object with the following information:
-
Status icon. The status of the current target’s event for the selected stage. The following statuses are possible:
-
Pending
-
Certified, signed off
-
Revoked, signed off
-
Abstained, signed off
-
Cancelled
-
No Certifier
-
Expired
Each status is displayed via a circular icon, and may have a different color or fill depending on the individual status. Certified statuses will be colored green, revoked colored red, and abstained colored yellow. The difference between when a normal value and the signed-off version of that value is displayed, the normal version will be displayed when all actions on an event have been completed, but the certifier has not yet signed off on it. After sign-off, the signed off version of the icon will be displayed. This allows the administrator to have a little more insight at this level into the progress of the campaign even before any sign offs occur.

Note that each icon will display a tooltip with the display status text if the administrator hovers over the icon.
-
-
Displayable Target Info Columns. The information that displays in the certification list table may vary depending on certification type and the special displayInUserInfo key in the glossary on identity objects.
For object certifications these displayable columns will always be name and description, so it’s highly recommended that these attributes exist on any custom managed object that you wish to certify
For user certifications, the displayable columns will always include at least the user’s givenName, sn, and email address, as well as any user attribute that has a glossary entry of type identity in the glossary and the displayInUserInfo boolean key set to true. Note that this key will not prevent you from displaying relationship attributes in the target list table, however with the exception of manager these attributes are not supported to display properly.
-
Claimed By. If the certifier for the given stage is a group, this column will display to inform the administrator as to which single user, if any, has claimed the given event.
-
Certifier. The user or role who is the certifier for the target event.

-
To see additional information on the individual certification events for a closed campaign, simply click on the target row in the certification list and the event details page will dropdown to view. All information contained within the event details reflects the same format and styling as described in section Reviewing Active Events.
Policies
Policies allow the administrator to define a set of criteria and schedule to determine violations within the identity system, as well as providing the ability to either grant exceptions to those violations or remediate the appropriate access. To manage violations, the administrator should create a policy with a defined expression for a given combination of access that violates a business rule, create a policy scan to generate violations from that policy and monitor any exceptions granted from certifiers. Configure scheduled policy scans to scan for violations on a regular basis or configure reactive policy scans to scan a user for violations whenever a user is updated.
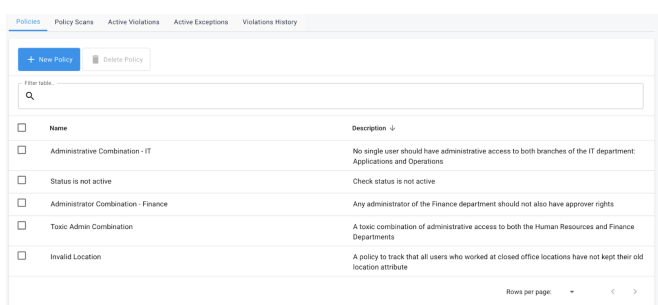
Policy Tables
-
Action Buttons
-
New Policy. Create a new policy.
-
Delete Policy. Delete an existing policy object.
-
-
Display Columns
-
Policy Name
-
Description: Name of the policy
-
Searchable: Yes
-
Sortable: Yes
-
-
Description: Description of the policy
-
Searchable: Yes
-
Sortable: Yes
-
-
Policy Scans
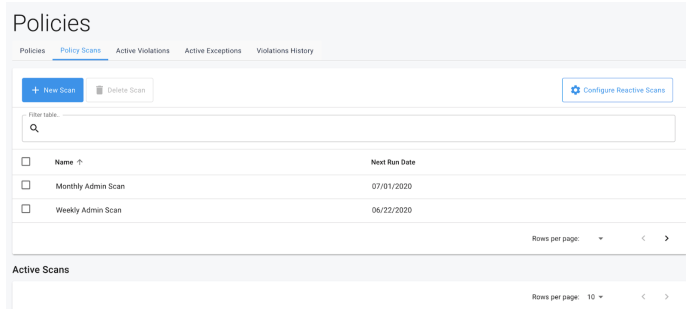
The policy scan and active scan tables have the following properties:
Scheduled Table:
-
Action Buttons:
-
New Scan. Create a new policy scan.
-
Delete Scan. Delete an existing policy scan.
-
-
Display Columns
-
Policy Name
-
Description: Name of the policy
-
Searchable: Yes
-
Sortable: Yes
-
-
Next Run Data
-
Description: Next date policy scan is scheduled to run
-
Searchable: No
-
Sortable: Yes
-
-
Active Violations
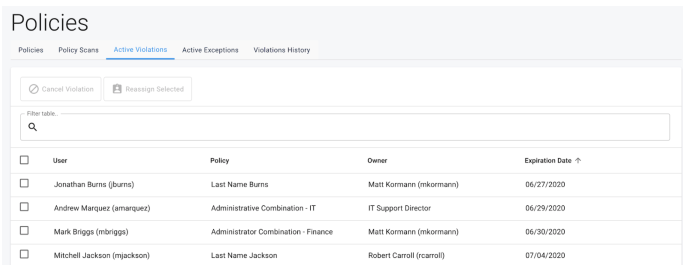
-
Action Buttons:
-
Cancel Violation. Cancel the selected violation(s)
-
Reassign Selected. Reassign the selected violation(s) to a different owner
-
User
-
Description: User who violated the policy
-
Searchable: Yes, by username
-
Sortable: no
-
-
Policy
-
Description: Name of the policy that was violated
-
Searchable: Yes
-
Sortable: Yes
-
-
Owner
-
Description: User or role who owns the policy violated
-
Searchable: No
-
Sortable: Yes
-
-
Expiration Date
-
Description: Date the violation task will expire
-
Searchable: No
-
Sortable: Yes
-
-
Active Exceptions
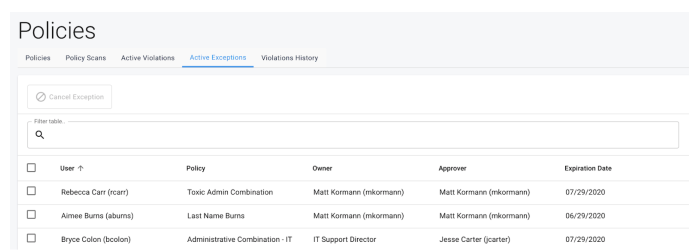
-
Action Buttons:
-
Cancel Exception. Cancel the selected exception(s).
-
-
Display Columns
-
User
-
Description: User who violated the policy
-
Searchable: Yes, by username
-
Sortable: no
-
-
Policy
-
Description: Name of the policy that was violated
-
Searchable: Yes
-
Sortable: Yes
-
-
Owner
-
Description: User or role who owns the violation exception
-
Searchable: No
-
Sortable: Yes
-
-
Expiration Date
-
Description: Date the violation exception will expire
-
Searchable: No
-
Sortable: Yes
-
-
Violation History
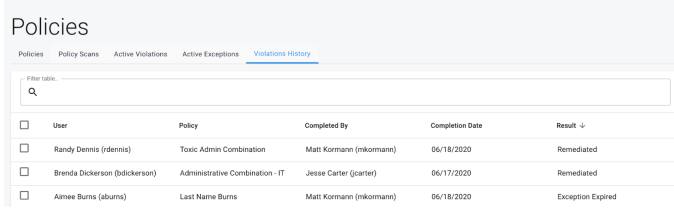
-
Action Buttons:
-
None
-
-
Display Columns
-
User
-
Description: User who violated the policy
-
Searchable: Yes, by username
-
Sortable: no
-
-
Policy
-
Description: Name of the policy that was violated
-
Searchable: Yes
-
Sortable: Yes
-
-
Completed By
-
Description: User who completed the violation
-
Searchable: No
-
Sortable: Yes
-
-
Completion Date
-
Description: Date the violation was completed (date remediated, cancelled, or exception expired)
-
Searchable: No
-
Sortable: Yes
-
-
Result
-
Description: Final result of the violation
-
Searchable: No
-
Sortable: Yes
-
-
Creating a New Policy
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
From the Policies tab, select ‘New Policy’.
-
On the Create Policy page, fill in each of the required fields. Additional details on the available fields are given below:
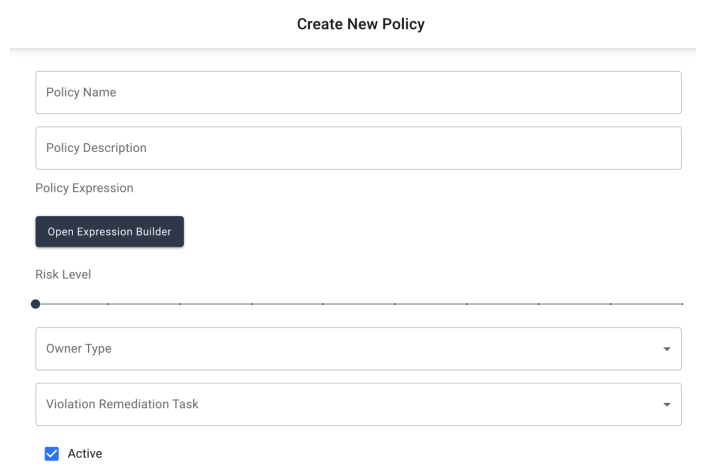
-
Policy Name: (Required) Reference name of the policy
-
Policy Description: Additional details describing the purpose of the policy. It is recommended to make this field as descriptive as possible to give the policy owner as much information as they need to make a remediation or exception decision.
-
Policy Expression: (Required) Rule for triggering a violation from the policy. If an event causing the rule to evaluate is true, a violation is created. The expression is defined using the Identity Governance expression builder.
-
-
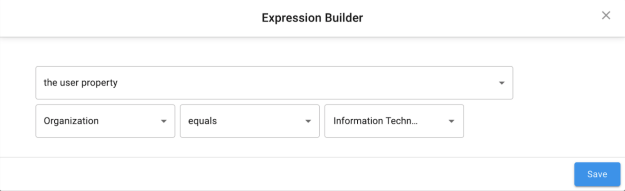
Upon selecting Open Expression Builder, the advanced expression builder is displayed. The following options for creating a custom expression are available within the policy scan target filter. For a more detailed description of what the individual options determine, refer to section Expression Builder.
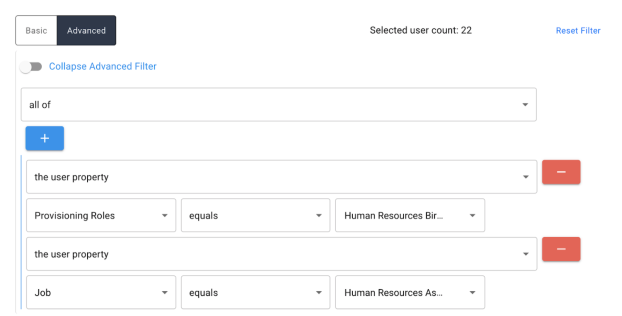
-
The user/object property: Choose from any user attribute
-
The user application: (User Certifications Only) Allows choice of any connected application to be selected from the dropdown menu
-
All of: Match all of the nested rows
-
Any of: Match at least one of the nested rows
-
None of: Negate the expression in the nested row
-
All users
For more information on building expressions, refer to section Expression Builder. -
Risk Level: (Required) Risk level for the policy on a 1 - 10 scale. A risk score of 1 indicates a policy that is tracking a low risk violation or combination of access, while a score of 10 is given for a policy that is tracking an access violation that is of the utmost importance. These scores can be used during a remediation workflow to determine what steps should be taken to revoke the violating access.
-
Owner Type: (Required) Type of owner to assign to this policy. The options are between a single user or a group.
-
Policy Owner: (Required) Specific owner being assigned to this policy. Choose the single user or role that will be the owner and responsible for decisions on all violations created by this policy.
-
Violation Remediation Task: An automated remediation task for handling revocations from violation acceptance .
For more information on remediation tasks, refer to section Remediation Tasks -
Active: Identifies whether the policy is active or inactive. If unchecked, the policy will not be evaluated on updates.
-
Modifying Policies
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Ensure the Policies tab is selected.
-
The table will be populated with all existing policy definitions that exist within the system.
-
To modify a policy, click on the row that contains the desired policy definition to open up the edit page. This page will be the same as the one used for creating policies, with the policy data already populated. See section Policy Tables for descriptions of the fields found within this form.
-
Once you have finished making your adjustments to the policy, click Save at the bottom of the form to complete the update. Note: For additional information on the fields to update on this form, refer to section Policy Tables.
Creating a New Policy Scan
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
From the Policies page, navigate to the Policy Scans tab and select ‘New Scan’.
-
On the Create Scan page, fill in each of the required fields.
Additional details on available fields are given below:
-
Name: (Required) Name of the policy scan
-
Trigger: (Required) When the policy scan will run. Options are described below:
-
Ad-hoc: Triggers a policy scan immediately after submitting the current form and can only be triggered once
-
Scheduled: Triggers a policy scan when a specified time duration has passed. Additional fields become available when selecting the ‘Scheduled’ option to allow specific durations. Note: For more information on scheduling events, refer to section Scheduling Events
-
-
User Target Filter: The subset of users the created scan will search for violations
-
Upon selecting Open Expression Builder, the advanced expression builder is displayed. The following options for creating a custom expression are available within the policy scan target filter. For a more detailed description of what the individual options determine, refer to section Expression Builder.
-
The user/object property: Choose from any user attribute
-
The user application: (User Certifications Only) Allows choice of any connected application to be selected from the dropdown menu
-
All of: Match all of the nested rows
-
Any of: Match at least one of the nested rows
-
None of: Negate the expression in the nested row
-
All users
-
-
-
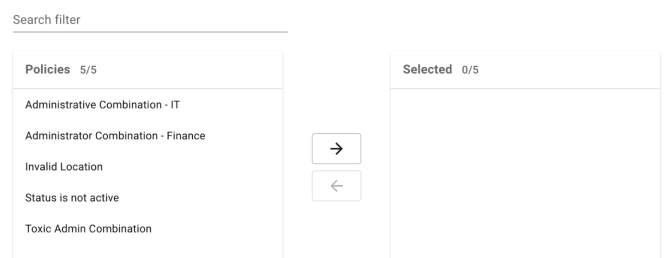
Select Policies: (Required) Policies that will be triggered by the scan. The field consists of side-by-side lists, with the left side containing available policies and the right side containing policies to be triggered in the scan. Selecting a policy in either list will move the policy to the opposite list.
-
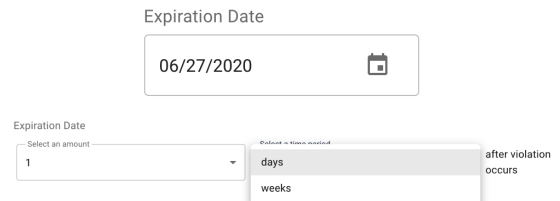
Expiration Date: (Required) Specifies how long a violation should remain active. After the specified date or duration, the violation expires and becomes unavailable for modification. For Ad-hoc policy scans, the expiration date is a static date in the future. For scheduled policy scans, the expiration date is a period of time after the violation has been found and the task created.
-
Escalation Schedule: Administrators are now able to define a configured schedule of escalation notifications that are delivered to a specific party at a specific time period before the violation expires.

-
Add an escalation date. To add an escalation notification to the schedule, simply click the ‘Add Escalation Date’ button located on the stage form beneath the deadline field. This will populate a single instance of the escalation form which consists of the following fields:
-
Amount: The numeric value that combines with the chosen time period to determine the time before the certification expires that the notification will be sent
-
Time period: Days or weeks before certification expires.
-
Escalation owner type: Who will be notified of the escalation. Choice of either user, group, or manager. Manager in this case refers to the manager of the owner for the given policy.
-
Choose escalation owner: If owner type is user or group, select the user or role that will receive the notification.
In order to add an additional escalation date the preceding form must be completed before the add button is enabled again. Escalation dates must be added in order of furthest from the deadline to closest.
-
-
-
-
Remove escalation date. To remove the most recent escalation date, click on the ‘Remove Escalation Date’ found next to the add button.
Modifying Scheduled Policy Scans
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Policy Scans tab to navigate to the scans section.
-
The top table will be populated with all existing policy scan definitions that exist within the system.
-
To modify a policy scan, click on the row that contains the desired scan definition to open up the edit page. This page will be the same as the one used for creating policy scans, with the scheduled scan data already populated. See section Creating a New Policy Scan for descriptions of the fields found within this form.
Reviewing Active Policy Scans
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Policy Scans tab to navigate to the scans section.
-
If any scans are currently in progress, the bottom table will be populated with all existing active scans that exist.
-
The information within this table will constantly update as a scan is running, and once a scan is completed it will be removed from the table completely.
Configure Reactive Policy Scans
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Policy Scans tab to navigate to the scans section.
-
On the top right of the policy scans table, there will be an action button for ‘Configure Reactive Scans.’ Clicking this button will display the reactive scans page.
-
The following fields are configurable for reactive scans.
-
Expiration Date: (Required) Specifies how long a violation should remain active. After the specified duration, a violation expires and becomes unavailable for modification. The expiration date is calculated from the day that the violation is found.
-
Escalation Schedule: Specifies where escalation notifications should be sent, at what day, and how many should go out overall. For more information on escalation schedules in policy scans, see section Creating a New Policy Scan.
-
Viewing Active Violations
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Active Violations tab to navigate to the active violations section. The table will be populated with any active violations that are currently assigned out to users for completion. Note that this does not include violations that are currently being granted an exception, only those that are not yet acted on.
-
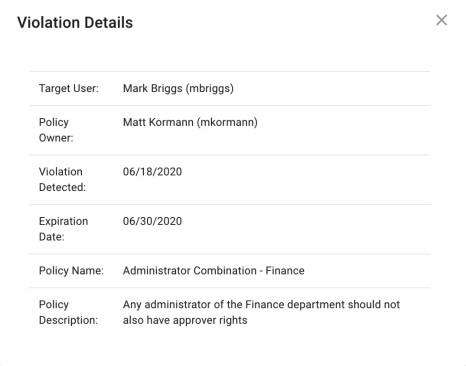
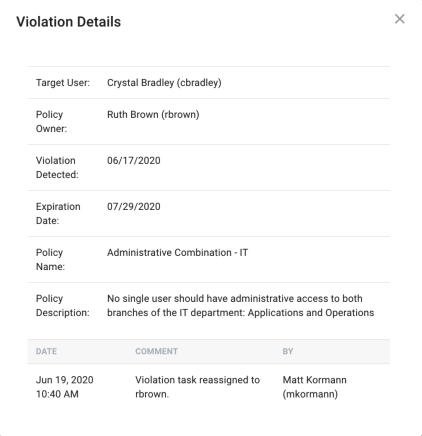
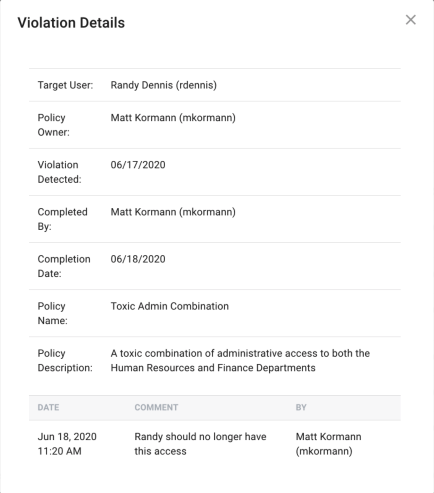
To view a given violation, click on its row within the table to expand the violation page. This page will show the following information:
-
Target User: The user who violated the policy
-
Policy Owner: The user or role who is assigned the violation task
-
Violation Detected: Date that the violation was found
-
Expiration Date: Date that the task will expire
-
Policy Name: Policy that was violated
-
Policy Description: Description of the policy that was violated
-
Comments: Any comments on the violation will appear at the bottom of the violation view screen
-
Date: Date comment was made
-
Comment: The message that was added
-
By: The person who made the comment
-
-
Cancelling Active Violations
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Active Violations tab to navigate to the active violations section.
-
Select the checkboxes next to the row or rows of the violations that you wish to cancel.
-
Click Cancel Violations.
-
The administrator will see a confirmation dialog to confirm that they wish to cancel the selected violations. Clicking ok will complete the cancellation action.

Reassigning Active Violations
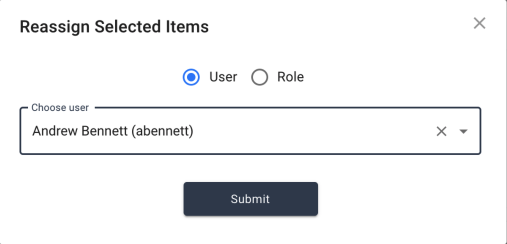
Administrators have the ability to reassign active violation tasks from the active violations tab. The button to reassign a violation is found in the action buttons section of the violation table.
Once the administrator has selected one or more violation rows to reassign, a small dialog box will appear with a few options for selecting the new owner. The administrator can choose to reassign to an individual user or a role (group.) When searching for a user, the administrator can use any of the properties made available and searchable via the User Name Display Format setting, while roles are searchable by name.

Viewing Active Exceptions
-
To navigate to the Policies page, click Administration > Policies.
-
Click the Active Exceptions tab to navigate to the active exceptions section. The table will be populated with any active exceptions that have currently been granted by the owner of the policy violated. A violation exception is considered
activeif it has been granted by the owner and has not yet reached its exception expiration date.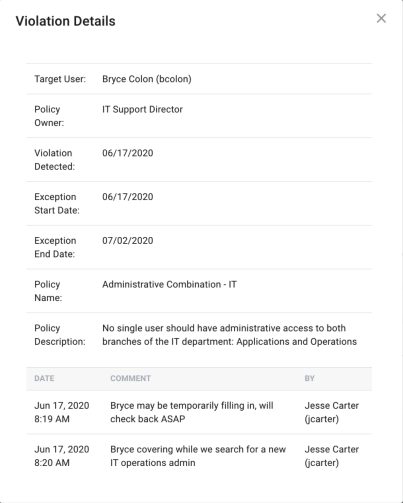
-
To view a given exception, click on its row within the table to expand the exception page. This page will show the following information:
-
Target User: The user who violated the policy
-
Policy Owner: The user or role who is assigned the violation task
-
Violation Detected: Date that the violation was found
-
Exception Start Date: Date that the exception was granted
-
Exception End Date: Date that the exception will expire
-
Policy Name: Policy that was violated
-
Policy Description: Description of the policy that was violated
-
Comments: Any comments on the violation will appear at the bottom of the violation view screen
-
Date: Date comment was made
-
Comment: The message that was added
-
By: The person who made the comment
-
-
Cancelling Active Exceptions
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Active Exceptions tab to navigate to the active exceptions section.
-
Select the checkboxes next to the row(s) of exceptions that you wish to cancel.
-
Click Cancel Exception.
-
The administrator will see a confirmation dialog to confirm that they wish to cancel the selected exceptions. Clicking ok will complete the cancellation action.
Reviewing Violation History
-
Navigate to the Policies page by clicking the Policies link under the Administration section of the side navigation bar.
-
Click the Violations History tab to navigate to the history section. The table will be populated with any past violations that have been completed. A violation is considered complete if it has any of the following statuses:
-
Remediated
-
Exception Expired
-
Cancelled
-
-
Target User: The user who violated the policy
-
Policy Owner: The user or role who is assigned the violation task
-
Violation Detected: Date that the violation was found
-
Exception Start Date: (if exception granted) Date that the exception was granted
-
Exception End Date: (if exception granted) Date that the exception expired
-
Completed By: User that completed the task
-
Completion Date: Date task was completed
-
Policy Name: Policy that was violated
-
Policy Description: Description of the policy that was violated
-
Comments: Any comments on the violation will appear at the bottom of the violation view screen
-
Date: Date comment was made
-
Comment: The message that was added
-
By: The person who made the comment
-
User Summary
The Access Review User Summary page allows governance administrators to access and view any given user’s entitlement certification history in one single screen. Administrators can see the user’s entire certifiable profile, the date and result of each certification of each entitlement, who made the certification decision, and view previous certifications for each entitlement as well. The user summary also allows the administrator to access any tasks that are currently assigned to that user, organized by task type (user certification, object certification, or violation). These task tables can be leveraged to easily reassign any or all tasks that belong to a given user in the event that they are no longer able to complete them as assigned.
|
If you are using IDM 7.2 with Identity Governance, you must enable the To enable the json |
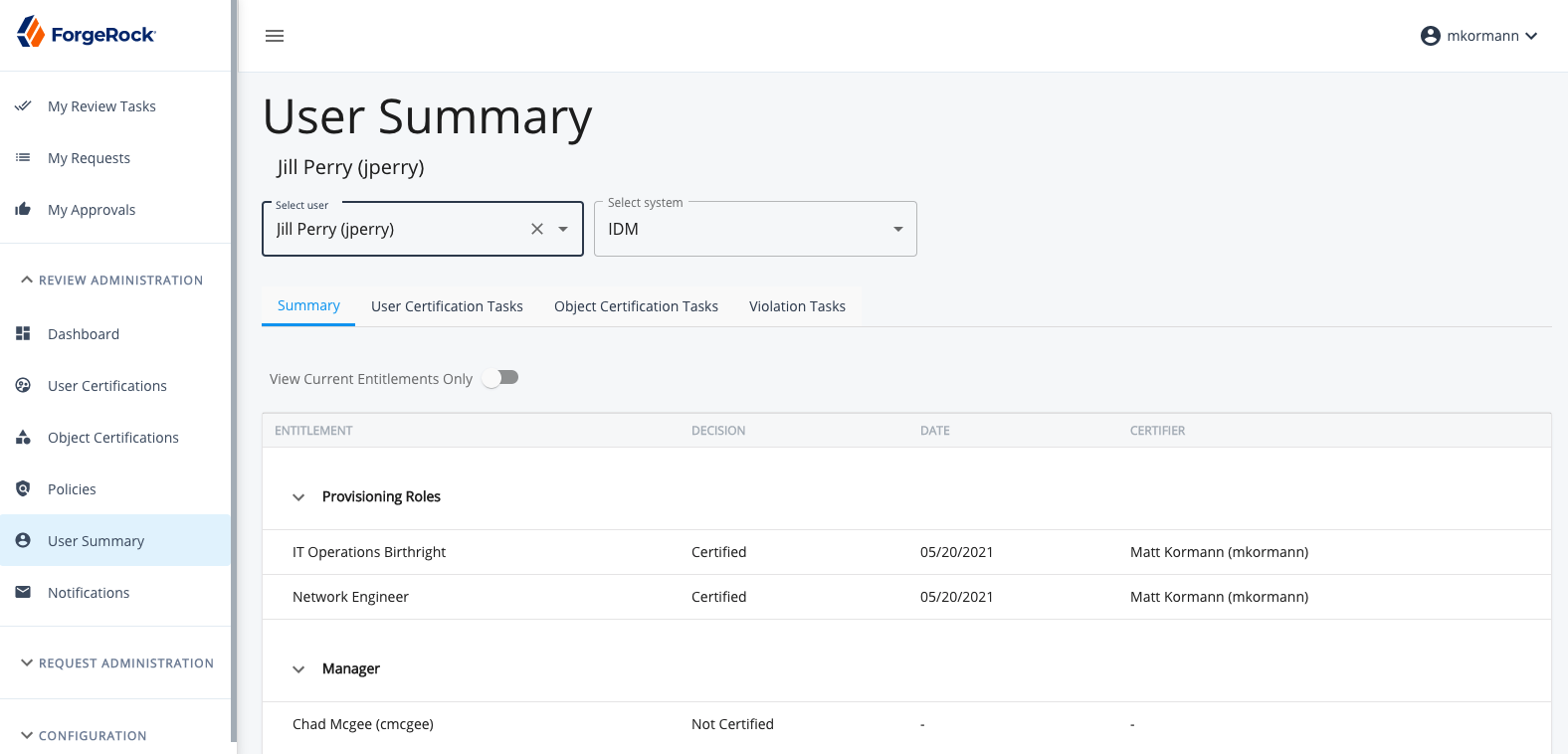
User Selection
When first navigating to the User Summary section, administrators will notice a blank auto select input field labelled ‘Select User.’ This field can be used to search for any user within the IDM system using the fields found in the display name format set in the system settings. Once a user is selected, the information for the given tab selected will populate below.
Summary
Select System
When the summary tab is selected, administrators will notice a second select input appears directly next to the user select input box at the top of the page, labelled ‘Select System.’ The “system” in this context refers to either the ForgeRock IDM environment or any of the linked systems that the given user has a connection to via a mapping in IDM. As ForgeRock Access Review allows attributes in both the IDM schema as well as connected systems to be certifiable, this selection will allow administrators to view certification history for the entitlements derived from any of those given sources. The default view and selection will always be ‘IDM,’ and will show the certifiable entitlements that exist on the user profile.
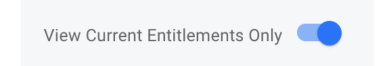
Viewing Current Entitlements Only
When viewing the Summary tab, administrators have the option to toggle on or off a view of the user’s currently assigned entitlements only. If toggled on, the only items displayed in the certification history summary table will be those that exist on the current user object. This view is useful when the administrator wants to view the current certification state of the user, to gain insight into whether or not there are entitlements on the user that have not yet been certified and possibly rectify that situation. If toggled off, the administrator will see not only the user’s current entitlements, but also any other entitlement that has ever been certified for that user. This allows administrators to get an entire lifetime view of a single user, even as their access has changed, been revoked, or otherwise altered.
Entitlements Table
The entitlements table is where the individual user entitlements are displayed, displaying data in four separate columns and separated into groups by attribute name. The entry shown for any given entitlement is the most recently completed and signed-off certification of that item, or in the event that a certification is in progress for that given entry, it will show that the entitlement is currently in-progress. The four columns displayed are:
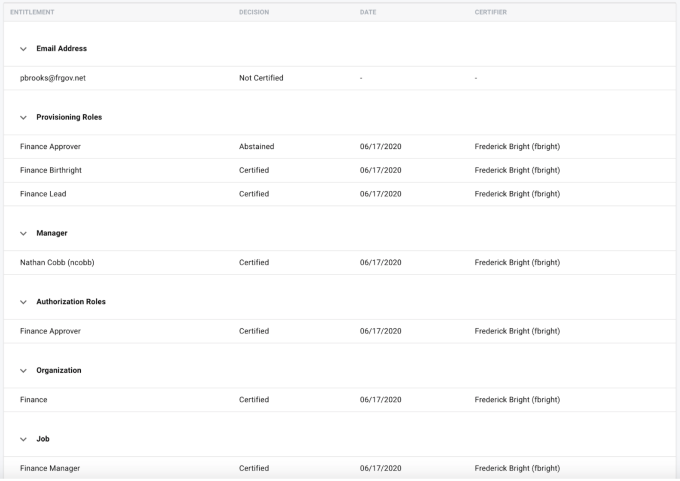
-
Entitlement - Name of the given entitlement
-
Decision - Most recent decision made on that entitlement. Possible values are listed below:
-
Certified
-
Revoked
-
Abstained
-
Not Certified
-
In-Progress
-
-
Date - Most recent date of certification
-
Certifier - Person who made the most recent certification decision
Each grouping of entitlements by attribute name can be collapsed or expanded by clicking on the arrow icon located to the left of the attribute name itself.
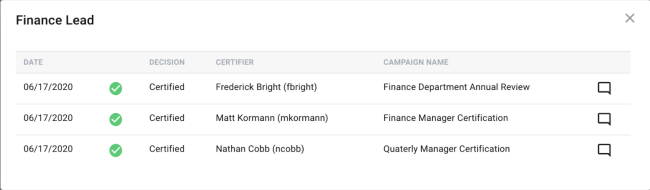
Single Entitlement History View
For any entitlement that is not listed as ‘Not Certified,’ the administrator can click on that entitlement row and expand the historical certification view for that item. The page that appears will show every time that the given entitlement has been certified for the target user in a table, organized by most recent data first, with the following columns:
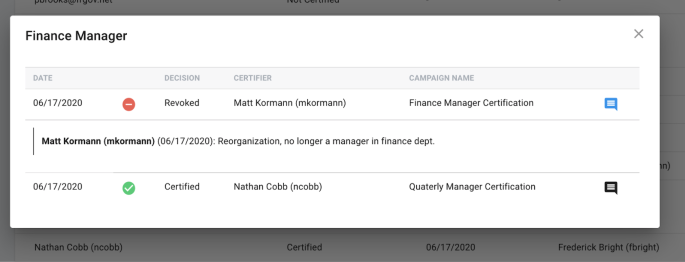
-
Date - Date the certification was signed off
-
Decision - Decision made for that certification
-
Certifier - User who completed and signed-off the listed event
-
Campaign Name - The campaign which the listed event was a part of
-
Comments - If comments were made on the specific object during the certification, the comment icon will be clickable, and will display the comments made in chronological order.
User Certification Tasks
The User Certification Tasks tab will display any certification campaign that currently has the selected user as a certifier for any of its events. This table will not display any certification tasks that the user is eligible to certify due to their membership of a role. This table, when populated, will mirror the table found on the end-user My Tasks dashboard page. For a further description on all of the columns and information found within the table, please refer to the Identity Governance 3.0 User Guide.
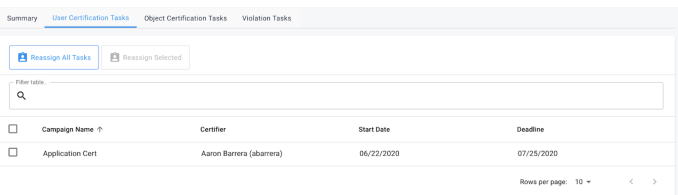
Viewing a User Certification
To get more details on any given campaign that’s assigned to the current user, the administrator can simply click on the certification row to navigate directly to the certification list. This is the same landing page that an admin ends up on when clicking a campaign from the User Certifications page.
Reassigning User Certification Tasks
Administrators have two options for reassignment of tasks from the User Certification Tasks table: reassign selected campaigns or reassign all tasks.
Reassigning Selected Campaigns
To reassign only those tasks that belong to select campaigns, the administrator can select the checkbox(es) next to any campaign that they wish to reassign. Once selected, clicking on Reassign Selected Tasks will display the reassign page where the admin can choose the user or role to reassign to. After the process has been completed any event that belonged directly to the chosen user will be assigned to the new certifier.
Reassigning All Tasks
Alternatively, admins can choose to reassign all User Certification Tasks that belong to a given user. This functionality can be used when a certifier is on an extended leave or no longer an active user within the system to transfer all of open the reassign page where the admin will choose the new certifier.
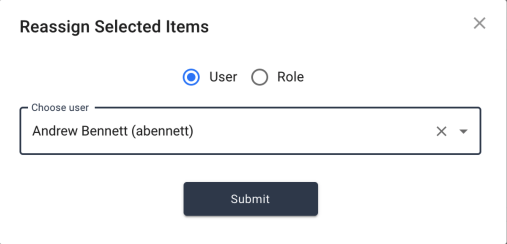
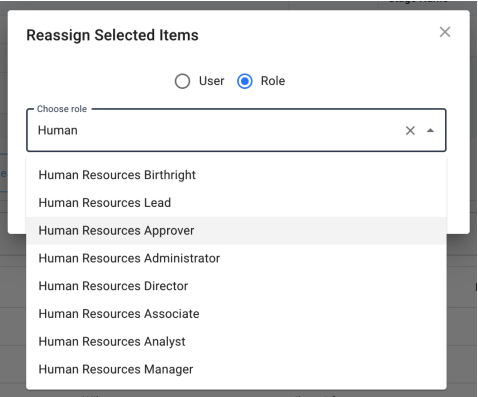
Reassigning Modal
Once the administrator has selected one of the reassign actions, a small dialog box appears with a few options for selecting the new owner. The administrator can choose to reassign to an individual user or a group (role.) When searching for a user, the administrator can use any of the properties made available and searchable using the User Name Display Format setting, while roles are searchable by name.
Object Certification Tasks
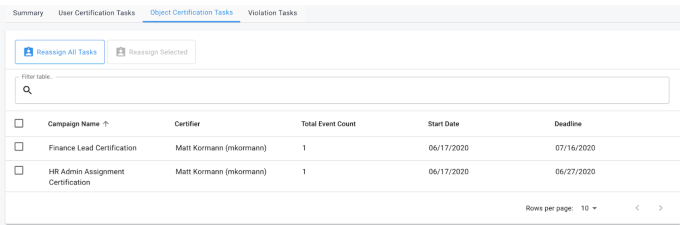
The object certification tasks table will mirror the exact functionality of the user certification tasks table but for object certification tasks. Administrators will be able to view all of the selected users’ object tasks, navigate directly to the tasks’ campaigns, or reassign any or all tasks from this table. For further information on the table’s functionality, refer to Section Selecting a Glossary Object Class.
Violation Tasks
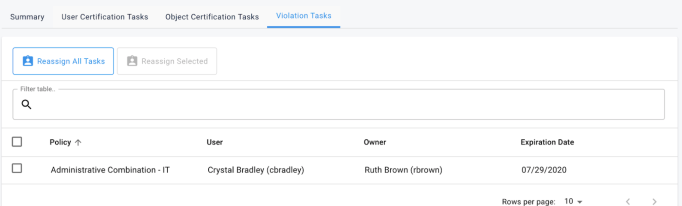
Like the certification tables described above, the violation tasks table will show all of the violation tasks directly assigned to the selected user. Administrators have the ability to reassign selected violation tasks or all violations tasks to another user or role. In addition, admins can view the current status of the violation by clicking on the violation row in the displayed table.
Review Notifications
Notification templates are used to define the messages sent to administrators and end-users when a certain event occurs.
Modifying a Notification Template
-
Navigate to the Manage Notifications page, located in the Administrative section of the Navigation Bar.
-
View contents under Notification List.
-
To display additional information about the notification, select a notification from the Notification List.
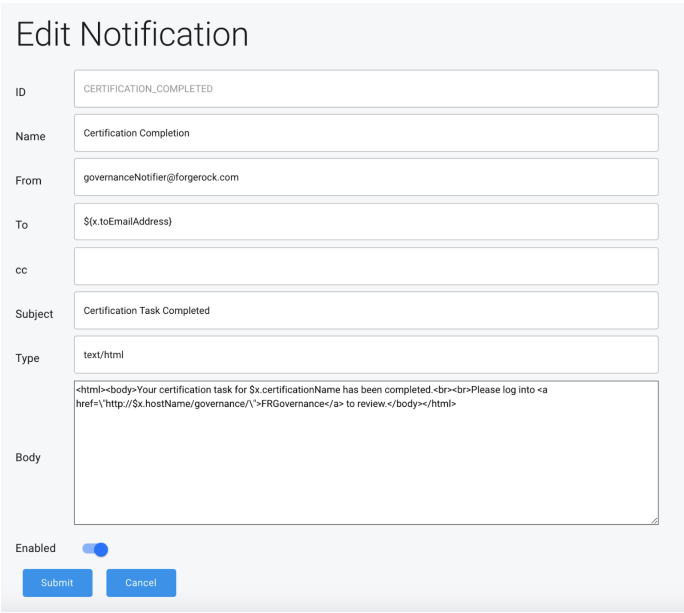
The following details are displayed:
-
ID: Represents unique identifier for the notification template. This field is not editable.
-
Name: (Required) Name of the notification template
-
From: (Required) Information that appears in the From field of the notification
-
To: (Required) Address of those who will receive the notification. It contains a default variable that evaluates information from the certification. Note: For more information on supported variables, see section Predefined Notification Variables.
-
CC: Addresses of users who may receive a copy of the notification
-
Subject: (Required) Information that appears in the Subject field of the notification
-
Type: (Required) Form of the notification to be sent. The value is defaulted to ‘text/html’.
-
Body: (Required) Contents of the notification. The default format is html, according to the value in the Type field, and may contain variables.
-
Enabled: (Required) Identifies whether the notification is enabled or disabled. If unchecked, the notification will not be sent on a triggering event. Note: For more information on supported variables, see section Predefined Notification Variables.
-
Predefined Notification Templates
The following list describes the predefined notification templates:
| Name | Description |
|---|---|
Certification Cancellation Failure |
Sent when a certification cancel fails during the cancellation process. |
Certification Cancelled |
Triggered when an administrator cancels a certification to inform the certifier that the certification is no longer available. |
Certification Completion |
Triggered when a user certification is completed to inform the certifier that the certification is complete. |
Certification Creation Adhoc |
Triggered when a user certification is created from an administrator to inform the certifier that the certification is pending. |
Certification Creation Adhoc Default Certifier |
Triggered when an ad-hoc user certification event is assigned to the default certifier |
Certification Creation Scheduled |
Triggered when a user certification is created as a scheduled event to inform the certifier that the certification is pending. |
Certification Creation Scheduled Default Certifier |
Triggered when a scheduled user certification event is assigned to the default certifier |
Certification Creation Triggered |
Triggered when a user certification is created after an update to a user to inform the certifier that the certification is pending. |
Certification Creation Triggered Default Certifier |
Triggered when an event-based user certification event is assigned to the default certifier |
Certification Escalated |
Triggered when a user certification is active past the escalation date set in the certification definition to inform the escalation owner that the certification is still pending. |
Certification Expired |
Triggered when a user certification was active past the expiration date set in the certification definition to inform the certifier that the certification is now inactive. |
Object Certification Completion |
Triggered when an object certification is completed to inform the certifier that the certification is complete. |
Object Certification Creation Adhoc |
Triggered when an object certification is created from an administrator to inform the certifier that the certification is pending. |
Object Certification Creation Scheduled |
Triggered when an object certification is created as a scheduled event to inform the certifier that the certification is pending. |
Object Certification Creation Triggered |
Triggered when an object certification is created after an update to an object to inform the certifier that the certification is pending. |
Object Certification Escalated |
Triggered when an object certification is active past the escalation date set in the certification definition to inform the escalation owner that the certification is still pending. |
Object Certification Expired |
Triggered when an object certification was active past the expiration date set in the certification definition to inform the certifier that the certification is now inactive. |
Policy Exception |
Triggered when an exception is created for a violation to confirm the exception with the violation owner. |
Policy Exception Expired |
Triggered when an exception for a violation has expired to inform the violation owner of the change. |
Policy Remediated |
Triggered when a violation is remediated by either an administrator or task to inform the violation owner. |
Policy Violation Detected |
Triggered when a violation is raised from a policy scan to inform the violation owner. |
Policy Violation Escalated |
Triggered when an escalation duration has been exceeded for a violation to inform the escalation owner of the violation. |
Policy Violation Expired |
Triggered when an expiration duration has been exceeded for a violation to inform the violation owner of the change. |
Predefined Notification Variables
The following describes the predefined variables that are used within notifications:
| Variable | Description |
|---|---|
${x.email} |
|
${x.certifierEmail} |
|
${x.escalatorEmail} |
|
$x.user |
|
$x.certifier |
|
$x.owner |
|
$x.certificationName |
Access Review Integration with the Glossary
There are a few major areas of functionality within Access Review that are handled by Glossary entries for certain identity objects. The following is the full list of keys, and what they control within the application:
| Class | Key | Type | Function |
|---|---|---|---|
Identity |
certifiable |
boolean |
Allows the attribute to appear within the user certification creation screen as an option for ‘Access to Certify’. If not present or set to false the attribute will not appear. |
Identity |
displayInUserInfo |
boolean |
Displays this attribute in the user certification list and event details tables. If not present or set to false the attribute will not appear. Note as of v3.0 this setting does not properly display relationship attributes within the above tables, with the exception of ‘manager’, which displays correctly. |
Identity-Value |
displayName |
String |
Displays the value defined here in lieu of the actual value on the user event details page, if the displayed attribute matches this entry. |
Object |
riskLevel |
Integer |
When risk level is enabled in system settings, certifications for user, object, and assignment will use this value to match against the provided certification filter for each object. |
Object |
entitlementOwner |
managed object |
The entitlement owner key is used to determine the user or role that should be assigned a certification task for the given object. This is used in user certifications when the certifier is set to “Entitlement Owner’, as well as when the glossary key certifier is chosen for object certifications. The value here should reference only a managed/user or a managed/role. |
Object |
displayName |
String |
Displays the value defined here in lieu of the actual value on the user event details page, if the object is included within a certification. |
System |
certifiable |
boolean |
Allows the system to appear within the user certification creation screen as an option for ‘Access to Certify’. If not present or set to false the system will not appear. |
System |
riskLevel |
Integer |
When risk level is enabled in system settings, certifications for users will use this value to match against the provided certification filter for each system. Note risk level for connected systems is global to that entire system and all its attributes. |
System |
entitlementOwner |
managed object |
The entitlement owner is used to determine the user or role that should be assigned a certification task for the given system. It’s used in user certifications when the certifier is set to 'Entitlement Owner’. The value here should reference only a managed/user or a managed/role, and is global to the system and all its attributes. |
System-Attribute |
certifiable |
boolean |
Allows the system attribute to appear within the user certification creation screen as an option for ‘Access to Certify’. If not present or set to false the attribute will not appear. |
System-Attribute |
displayable |
boolean |
Allows the system attribute to appear within the user event details page as a non-certifiable attribute. It can be used to provide the certifier more insight to the user’s account, for entitlements that may be helpful to see not certify (e.g. cn, uid, etc.) |
Viewing Glossary Metadata within a Certification
When viewing the event details display of a single event within a certification, users will notice that the entitlements, and in user certifications the attribute names, of each certifiable row are clickable links. If clicked, a glossary page will appear that corresponds to the identity attribute or value chosen. If that entry exists, the metadata for that item will be displayed in a key-value table. If that entry does not exist, the user will be informed that there is no current glossary entry for that item. This view allows the certifier or admin to gain more information and perspective on the things included in that particular certification.
There is often metadata in glossary entries that administrators would either not want the end user to see, whether that be for privacy reasons or simply because the information would be more confusing than helpful. Access Review leverages a configuration file within the openidm/conf directory called displayableMetadata.json to restrict the keys that will display in these pages for each of the different glossary object classes. Only keys that appear for each class type will be shown to end users, and they are global for each class type.
