PingOne connector
| This is a SaaS common connector. |
The PingOne connector lets you manage and synchronize data between PingOne and IDM or Advanced Identity Cloud. A PingOne administrator account is required for this connector to work.
PingOne requirements
Before you can configure the connector, you must register an application in PingOne. You need a PingOne environment to complete this procedure:
-
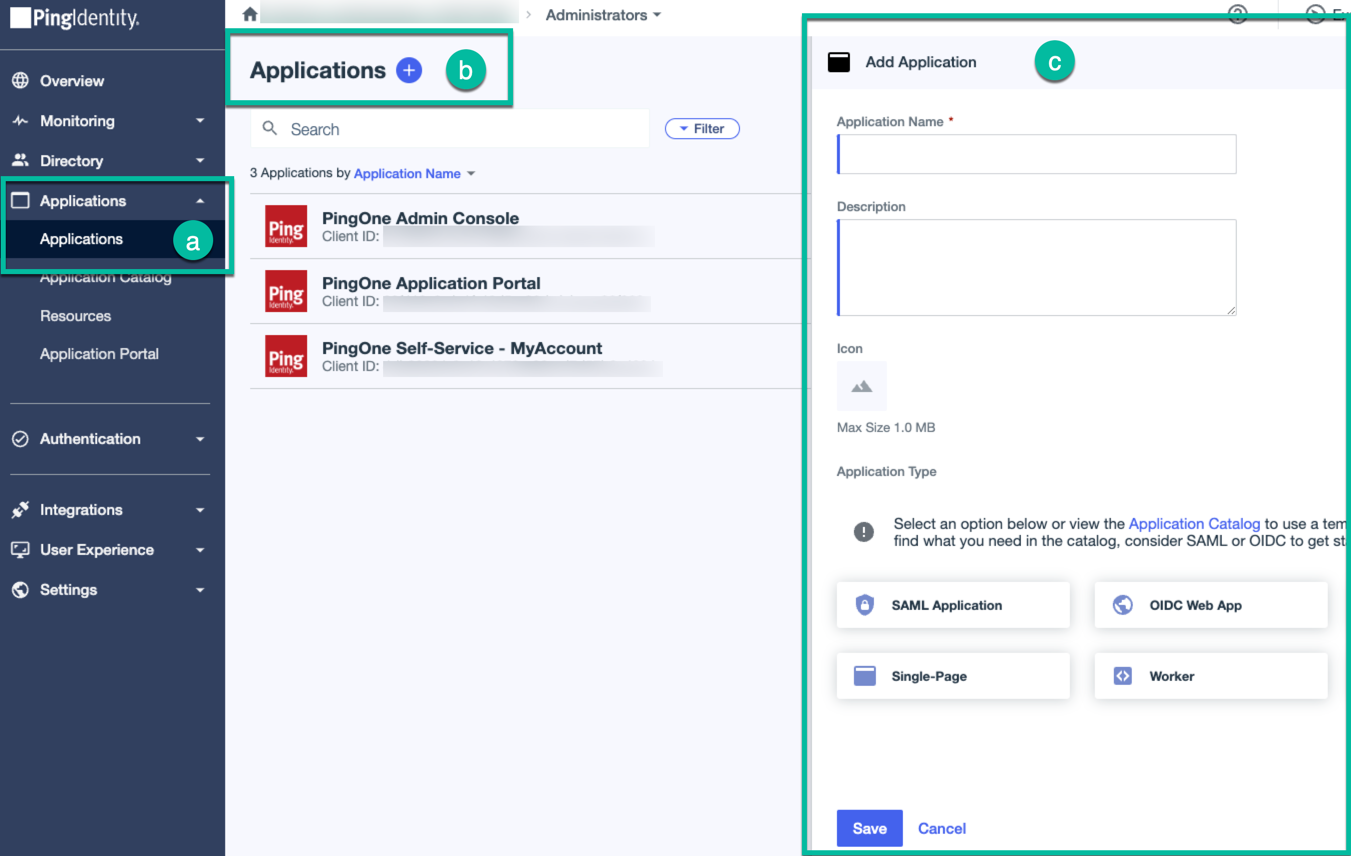
In your PingOne environment, create a new application:
-
From the menu, expand the Applications node, and click Applications.
-
On the Applications page, click the add button.
-
In the Add Application window, enter the necessary details, select the Worker application type, and click Save.
Show Me
-
-
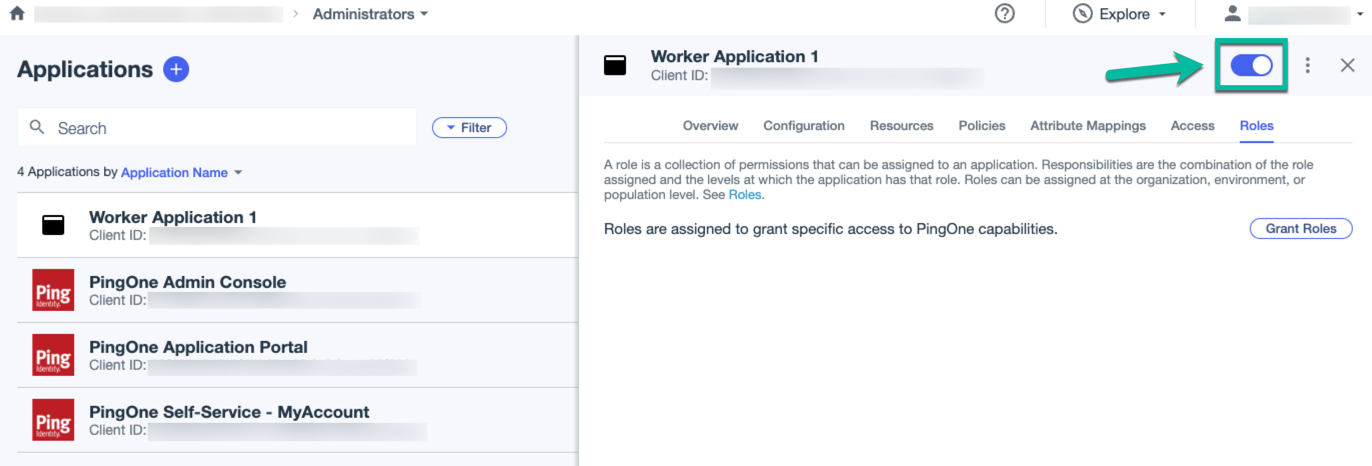
In the Application Name window, enable the application.
Show Me
-
On the Roles tab, click Grant Roles.
-
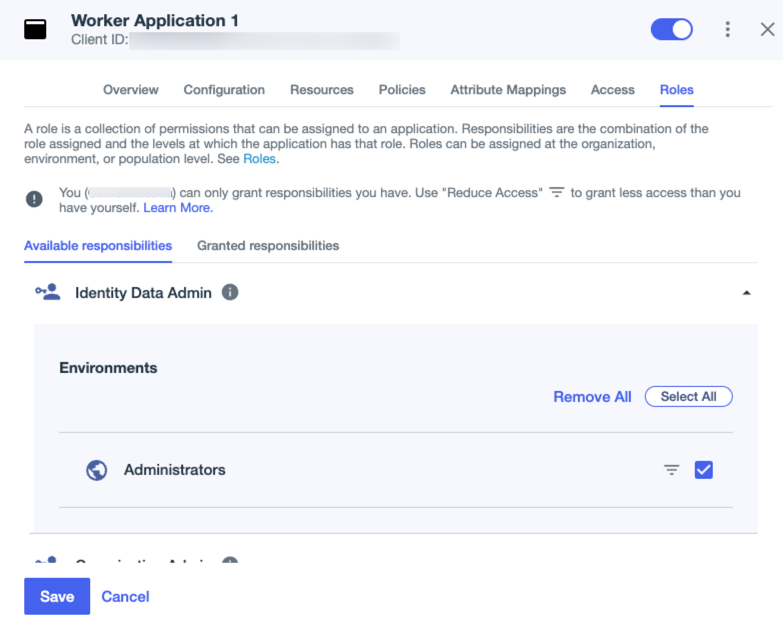
On the Available Responsibilities tab, expand the Identity Data Admin node, select the applicable environment, and click Save.
Show Me
-
Click the Configuration tab, and make note of the following:
-
URLs > Token Endpoint
-
General > Client ID
-
General > Client Secret
-
General > Environment ID
Use these values when you Configure the PingOne connector.
-
Install the PingOne connector
|
If you are looking for the Advanced Identity Cloud application for this connector, refer to: |
You can download any connector from Backstage, but some are included in the default deployment for Advanced Identity Cloud, IDM, or RCS. When using an included connector, you can skip installing it and move directly to configuration.
| Connector | IDM | RCS |
|---|---|---|
No |
No |
Download the connector .jar file from Backstage.
-
If you are running the connector locally, place it in the
/path/to/openidm/connectorsdirectory, for example:mv ~/Downloads/pingone-connector-1.5.20.23.jar /path/to/openidm/connectors/
-
If you are using a remote connector server (RCS), place it in the
/path/to/openicf/connectorsdirectory on the RCS.
Configure the PingOne connector
Create a connector configuration using the IDM admin UI:
-
From the navigation bar, click Configure > Connectors.
-
On the Connectors page, click New Connector.
-
On the New Connector page, type a Connector Name.
-
From the Connector Type drop-down list, select PingOne Connector - 1.5.20.23.
-
Complete the Base Connector Details.
For a list of all configuration properties, refer to PingOne Connector Configuration -
Click Save.
When your connector is configured correctly, the connector displays as Active in the admin UI.
Refer to this procedure to create a connector configuration over REST.
Example PingOne configuration
This excerpt shows a sample PingOne connector configuration:
{
"connectorRef" : {
"displayName" : "org.forgerock.openicf.connectors.pingone.PingOneConnector",
"bundleVersion" : "[1.5.0.0,1.6.0.0)",
"systemType" : "provisioner.openicf",
"bundleName" : "org.forgerock.openicf.connectors.pingone-connector",
"connectorName" : "org.forgerock.openicf.connectors.pingone.PingOneConnector",
"connectorHostRef" : ""
},
"poolConfigOption" : {
"maxObjects" : 10,
"maxIdle" : 10,
"maxWait" : 150000,
"minEvictableIdleTimeMillis" : 120000,
"minIdle" : 1
},
"resultsHandlerConfig" : {
"enableNormalizingResultsHandler" : false,
"enableFilteredResultsHandler" : false,
"enableCaseInsensitiveFilter" : false,
"enableAttributesToGetSearchResultsHandler" : true
},
"operationTimeout" : {
"CREATE" : -1,
"UPDATE" : -1,
"DELETE" : -1,
"TEST" : -1,
"SCRIPT_ON_CONNECTOR" : -1,
"SCRIPT_ON_RESOURCE" : -1,
"GET" : -1,
"RESOLVEUSERNAME" : -1,
"AUTHENTICATE" : -1,
"SEARCH" : -1,
"VALIDATE" : -1,
"SYNC" : -1,
"SCHEMA" : -1
},
"configurationProperties" : {
"environmentId" : null,
"serviceUri" : null,
"login" : null,
"password" : null,
"authenticationMethod" : "OAUTH",
"tokenEndpoint" : null,
"clientId" : null,
"clientSecret" : null,
"authToken" : null,
"acceptSelfSignedCertificates" : false,
"disableHostNameVerifier" : false,
"disableHttpCompression" : false,
"clientCertAlias" : null,
"clientCertPassword" : null,
"maximumConnections" : 10,
"httpProxyHost" : null,
"httpProxyPort" : null,
"httpProxyUsername" : null,
"httpProxyPassword" : null,
"connectionTimeout" : 30,
"refreshToken" : null,
"grantType" : null,
"scope" : null,
"authorizationTokenPrefix" : "Bearer",
"useBasicAuthForOauthTokenNeg" : true
},
"enabled" : true,
"objectTypes" : {
"__GROUP__" : {
"$schema" : "http://json-schema.org/draft-03/schema",
"id" : "__GROUP__",
"type" : "object",
"nativeType" : "__GROUP__",
...
}
},
"__POPULATION__" : {
"$schema" : "http://json-schema.org/draft-03/schema",
"id" : "__POPULATION__",
"type" : "object",
"nativeType" : "__POPULATION__",
...
}
},
"__ACCOUNT__" : {
"$schema" : "http://json-schema.org/draft-03/schema",
"id" : "__ACCOUNT__",
"type" : "object",
"nativeType" : "__ACCOUNT__",
...
}
},
"__AVAILABLE_ROLE__" : {
"$schema" : "http://json-schema.org/draft-03/schema",
"id" : "__AVAILABLE_ROLE__",
"type" : "object",
"nativeType" : "__AVAILABLE_ROLE__",
...
}
},
"__ROLE__" : {
"$schema" : "http://json-schema.org/draft-03/schema",
"id" : "__ROLE__",
"type" : "object",
"nativeType" : "__ROLE__",
...
}
}
}
}Test the PingOne connector
Test that the configuration is correct by running the following command:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request POST \
"http://localhost:8080/openidm/system/pingone?_action=test"
{
"name": "pingone",
"enabled": true,
"config": "config/provisioner.openicf/pingone",
"connectorRef": {
"bundleVersion": "[1.5.0.0,1.6.0.0)",
"bundleName": "org.forgerock.openicf.connectors.pingone-connector",
"connectorName": "org.forgerock.openicf.connectors.pingone.PingOneConnector"
},
"displayName": "PingOne Connector",
"objectTypes": [
"__GROUP__",
"__POPULATION__",
"__ACCOUNT__",
"__ALL__",
"__AVAILABLE_ROLE__",
"__ROLE__"
],
"ok": true
}
If the command returns "ok": true, your connector has been configured correctly and can authenticate to the PingOne environment.
PingOne remote connector
If you want to run this connector outside of PingOne Advanced Identity Cloud or IDM, you can configure the PingOne connector as a remote connector. Java Connectors installed remotely on a Java Connector Server function identically to those bundled locally within PingOne Advanced Identity Cloud or installed locally on IDM.
You can download the PingOne connector from here.
Refer to Remote connectors for configuring the PingOne remote connector.
Implementation specifics
Any sync mapping that uses PingOne as the source or target must include the following in the mapping configuration:
-
Source
-
Target
{
"reconSourceQueryPaging" : true
}{
"reconTargetQueryPaging" : true
}The default recon query page size for IDM and Advanced Identity Cloud is too large for PingOne resources. You must set the source and target to 1000 or less. For example:
{
"reconSourceQueryPageSize" : 1000,
"reconTargetQueryPageSize" : 1000,
...
}For more information about sync mappings, refer to:
Use the PingOne connector
You can use the PingOne connector to perform various actions on the following PingOne resources:
| Connector resource | PingOne resource type |
|---|---|
|
|
|
|
|
|
|
|
|
Users
Create a PingOne user
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request POST \
--data '{
"username": "A_20240223183659857",
"nickname": "A_2024022",
"email": "A_20240223183659857@example.com",
"primaryPhone": "123 123 123"
}' \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__?_action=create"
{
"_id": "dc3c02ab-5a22-4537-b5cb-7f3a0c164ab1",
"createdAt": "2024-02-24T02:37:01.889Z",
"email": "A_20240223183659857@example.com",
"__NAME__": "A_20240223183659857",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "A_20240223183659857",
"updatedAt": "2024-02-24T02:37:01.889Z",
"mfaEnabled": true,
"nickname": "A_2024022",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
}
}
|
When you create a new user, you must specify at least the |
Create a PingOne user with group memberships and role assignments
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request POST \
--data '{
"username": "20240223183659857_gm",
"nickname": "2024022318",
"email": "20240223183659857_gm@example.com",
"primaryPhone": "123 123 123",
"__groupMemberships__": [
"336c9e3e-5480-4f32-8706-ccd944531286",
"aa4c33a9-6726-4526-b70f-7cd63fce5c28"
],
"__roleAssignments__": [
"9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:0bd9c966-7664-4ac1-b059-0ff9293908e2",
"9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:ce00e15f-f845-4df1-abf3-fdc4ff4e176c"
]
}' \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__?_action=create"
{
"_id": "e9c4a878-d26d-4a2e-9da7-3d83b5d6a8b9",
"__groupMemberships__": [
"336c9e3e-5480-4f32-8706-ccd944531286",
"aa4c33a9-6726-4526-b70f-7cd63fce5c28"
],
"__roleAssignments__": [
"9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:0bd9c966-7664-4ac1-b059-0ff9293908e2",
"9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:ce00e15f-f845-4df1-abf3-fdc4ff4e176c"
],
"createdAt": "2024-02-24T02:37:09.365Z",
"email": "20240223183659857_gm@example.com",
"__NAME__": "20240223183659857_gm",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "20240223183659857_gm",
"updatedAt": "2024-02-24T02:37:09.967Z",
"mfaEnabled": true,
"nickname": "2024022318",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
},
"groupMemberships": [
{
"name": "20240223183659857_A",
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"id": "336c9e3e-5480-4f32-8706-ccd944531286",
"isExternal": false,
"type": "DIRECT"
},
{
"name": "20240223183659857_B",
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"id": "aa4c33a9-6726-4526-b70f-7cd63fce5c28",
"isExternal": false,
"type": "DIRECT"
}
],
"roleAssignments": [
{
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"role": {
"id": "0bd9c966-7664-4ac1-b059-0ff9293908e2"
},
"scope": {
"id": "9da69b4c-8101-4db8-8cef-66a9a167b02e",
"type": "ENVIRONMENT"
},
"readOnly": false,
"id": "2c48fdd6-fec3-47f6-80d7-c993bafc8802",
"type": "DIRECT",
"user": {
"id": "fd5e0c14-ba9b-479b-85f8-80ac9222cc97"
}
},
{
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"role": {
"id": "ce00e15f-f845-4df1-abf3-fdc4ff4e176c"
},
"scope": {
"id": "9da69b4c-8101-4db8-8cef-66a9a167b02e",
"type": "ENVIRONMENT"
},
"readOnly": false,
"id": "c5eda229-fdc7-4e4a-b887-833b53b3ec87",
"type": "DIRECT",
"user": {
"id": "fd5e0c14-ba9b-479b-85f8-80ac9222cc97"
}
}
]
}
Update a PingOne user
To modify an existing user, include all user attributes in the PUT request. The following user attributes can’t be modified:
-
population -
mfaEnabled -
verifyStatus -
identityProvider -
linkedAccounts
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--header "If-Match:*" \
--request PUT \
--data '{
"username": "A_20240223183659857",
"nickname": "A_2024022",
"email": "update@email.com",
"primaryPhone": "123 123 123"
}' \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__/4da38ae8-50dc-4555-9c76-6d2f9a984007"
{
"_id": "4da38ae8-50dc-4555-9c76-6d2f9a984007",
"createdAt": "2024-02-24T02:37:04.668Z",
"email": "update@email.com",
"__NAME__": "A_20240223183659857",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "C_20240223183659857",
"updatedAt": "2024-02-24T02:37:05.866Z",
"mfaEnabled": true,
"nickname": "A_2024022",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
}
}
Query all PingOne user IDs
The following example queries all PingOne users:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__?_queryId=query-all-ids"
{
"result": [
{
"_id": "ffc979b8-6279-4cb9-b327-98db745ff60b"
},
{
"_id": "e0e0258a-87de-43c5-8e25-91915959317d"
},
...
],
"resultCount": 5,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}
Read all PingOne users
The following example reads all PingOne users:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__?_queryFilter=true"
{
"result": [
{
"_id": "ffc979b8-6279-4cb9-b327-98db745ff60b",
"createdAt": "2024-02-24T02:35:33.304Z",
"email": "OCPSGYHOARDL@example.com",
"__NAME__": "OCPSGYHOARDL",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "OCPSGYHOARDL",
"updatedAt": "2024-02-24T02:35:33.304Z",
"mfaEnabled": true,
"nickname": "OCPSGY",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
}
},
{
"_id": "e0e0258a-87de-43c5-8e25-91915959317d",
"createdAt": "2024-02-24T02:35:34.219Z",
"email": "FQHCIODRAYIK@example.com",
"__NAME__": "FQHCIODRAYIK",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "FQHCIODRAYIK",
"updatedAt": "2024-02-24T02:35:34.219Z",
"mfaEnabled": true,
"nickname": "FQHCIO",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
}
},
...
],
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}
Read a single PingOne user
The following example reads PingOne user dfdb1068-174c-4c05-8a73-8c91e3f20f83:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__/dfdb1068-174c-4c05-8a73-8c91e3f20f83"
{
"_id": "dfdb1068-174c-4c05-8a73-8c91e3f20f83",
"createdAt": "2024-02-24T02:37:06.471Z",
"email": "D_20240223183659857@example.com",
"__NAME__": "D_20240223183659857",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "D_20240223183659857",
"updatedAt": "2024-02-24T02:37:06.471Z",
"mfaEnabled": true,
"nickname": "D_2024022",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
}
}
Delete a PingOne user
The following example deletes a PingOne account:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--header "If-Match: *" \
--request DELETE \
"http://localhost:8080/openidm/system/pingone/__ACCOUNT__/dfdb1068-174c-4c05-8a73-8c91e3f20f83"
{
"_id": "dfdb1068-174c-4c05-8a73-8c91e3f20f83",
"createdAt": "2024-02-24T02:37:06.471Z",
"email": "D_20240223183659857@example.com",
"__NAME__": "D_20240223183659857",
"identityProvider": {
"type": "PING_ONE"
},
"primaryPhone": "123 123 123",
"enabled": true,
"lifecycle": {
"status": "ACCOUNT_OK"
},
"verifyStatus": "NOT_INITIATED",
"username": "D_20240223183659857",
"updatedAt": "2024-02-24T02:37:06.471Z",
"mfaEnabled": true,
"nickname": "D_2024022",
"account": {
"canAuthenticate": true,
"status": "OK"
},
"population": {
"id": "1a0348b5-c6f5-41b0-a71a-194ed76f703f"
}
}
Groups
Create a group
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header 'Content-Type: application/json' \
--request POST \
--data '{
"name": "A_20240223183647490",
"description": "standard description"
}' \
'http://localhost:8080/openidm/system/pingone/__GROUP__?_action=create'
{
"_id": "bb6534d0-39a0-4e8e-b4b1-efe595063540",
"directMemberCounts": {
"users": 0,
"groups": 0
},
"__NAME__": "A_20240223183647490",
"name": "A_20240223183647490",
"description": "standard description"
}
|
When you create a new group, you must specify at least the |
Query all group IDs
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__GROUP__?_queryId=query-all-ids"
{
"result": [
{
"_id": "c42b514f-56c9-4c63-a91c-679d006ac248"
},
{
"_id": "bb6534d0-39a0-4e8e-b4b1-efe595063540"
},
{
"_id": "1ce940ce-dde6-4066-8869-9435072c4089"
},
...
],
"resultCount": 14,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}
Query a specific group
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__GROUP__/c42b514f-56c9-4c63-a91c-679d006ac248"
{
"_id": "c42b514f-56c9-4c63-a91c-679d006ac248",
"directMemberCounts": {
"users": 0,
"groups": 0
},
"__NAME__": "PY_GROUP_20240223183647490",
"name": "PY_GROUP_20240223183647490",
"description": "standard description"
}
Update a group
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header 'If-Match: *' \
--header 'Content-Type: application/json' \
--request PUT \
--data '{
"name": "C_20240223183647490",
"description": "updated description"
}' \
'http://localhost:8080/openidm/system/pingone/__GROUP__/bb6534d0-39a0-4e8e-b4b1-efe595063540'
{
"_id": "bb6534d0-39a0-4e8e-b4b1-efe595063540",
"directMemberCounts": {
"users": 0,
"groups": 0
},
"__NAME__": "A_20240223183647490",
"name": "A_20240223183647490",
"description": "updated description"
}
Delete a group
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "If-Match: *" \
--header 'Accept-API-Version: resource=1.0' \
--request DELETE \
'http://localhost:8080/openidm/system/pingone/__GROUP__/1ce940ce-dde6-4066-8869-9435072c4089'
{
"_id": "1ce940ce-dde6-4066-8869-9435072c4089",
"directMemberCounts": {
"users": 0,
"groups": 0
},
"__NAME__": "D_20240223183647490",
"name": "D_20240223183647490",
"description": "standard description"
}
Populations
A PingOne population defines a particular set of users.
Create a population
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header 'Content-Type: application/json' \
--request POST \
--data '{
"name": "C_20240223183654888",
"description": "standard description"
}' \
'http://localhost:8080/openidm/system/pingone/__POPULATION__?_action=create'
{
"_id": "e40936b4-36ec-4250-96dd-1c37ee8773e5",
"createdAt": "2024-02-24T02:36:56.710Z",
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"description": "standard description",
"default": "false",
"updatedAt": "2024-02-24T02:36:56.710Z",
"name": "C_20240223183654888",
"userCount": 0,
"__NAME__": "C_20240223183654888"
}
|
When you create a new population, you must specify at least the |
Read a single population
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__POPULATION__/e40936b4-36ec-4250-96dd-1c37ee8773e5"
{
"_id": "e40936b4-36ec-4250-96dd-1c37ee8773e5",
"createdAt": "2024-02-24T02:36:56.710Z",
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"description": "standard description",
"default": "false",
"updatedAt": "2024-02-24T02:36:56.710Z",
"name": "C_20240223183654888",
"userCount": 0,
"__NAME__": "C_20240223183654888"
}
Update a population
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header 'If-Match: *' \
--header 'Content-Type: application/json' \
--request PUT \
--data '{
"name": "C_20240223183654888",
"description": "updated description"
}' \
'http://localhost:8080/openidm/system/pingone/__POPULATION__/e40936b4-36ec-4250-96dd-1c37ee8773e5'
{
"_id": "e40936b4-36ec-4250-96dd-1c37ee8773e5",
"createdAt": "2024-02-24T02:36:56.710Z",
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"description": "updated description",
"default": "false",
"updatedAt": "2024-02-24T02:36:57.125Z",
"name": "C_20240223183654888",
"userCount": 0,
"__NAME__": "C_20240223183654888"
}
Delete a population
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header 'If-Match: *' \
--header 'Content-Type: application/json' \
--request DELETE \
'http://localhost:8080/openidm/system/pingone/__POPULATION__/93c83bc9-a546-4728-bd1f-f75a6436616c'
{
"_id": "93c83bc9-a546-4728-bd1f-f75a6436616c",
"createdAt": "2024-02-24T02:36:57.463Z",
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"description": "standard description",
"default": "false",
"updatedAt": "2024-02-24T02:36:57.463Z",
"name": "D_20240223183654888",
"userCount": 0,
"__NAME__": "D_20240223183654888"
}
Roles
Read all roles
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__ROLE__?_queryFilter=true"
{
"result": [
{
"_id": "1813bc13-8d13-4e88-a825-d40bfe82777b",
"applicableTo": [
"ORGANIZATION"
],
"name": "Organization Admin",
"description": "Organization Admin",
"permissions": [
{
"id": "advancedservices:read:config",
"classifier": "config",
"description": "Retrieve PingOne Advanced Services customer configuration"
},
{
"id": "authz:update:entity",
"classifier": "entity",
"description": "Update PingOne Authorize Entity"
},
{
"id": "pingintelligence:create:orchestration",
"classifier": "orchestration",
"description": "Creates a Orchestration flow for Ping Intelligence deployment"
},
{
"id": "authz:read:entity",
"classifier": "entity",
"description": "Read PingOne Authorize Entity"
},
{
"id": "authz:create:condition",
"classifier": "condition",
"description": "Create a PingOne Authorize Condition"
},
{
"id": "authz:test:condition",
"classifier": "condition",
"description": "Test a PingOne Authorize Condition"
},
{
"id": "authz:create:service",
"classifier": "service",
"description": "Create a PingOne Authorize Service"
},
{
"id": "authz:read:recentdecisions",
"classifier": "recentdecisions",
"description": "Read Recent Decisions of a PingOne Authorize Decision Endpoint"
},
{
"id": "orgmgt:read:organization",
"classifier": "organization",
"description": "Read organizations"
},
{
"id": "pingenterprise:update:orchestration",
"classifier": "orchestration",
"description": "Updates Orchestration flow for Ping Enterprise deployment"
},
...
],
"__NAME__": "Organization Admin"
},
...
],
"resultCount": 13,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}
Read a single role
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Content-Type: application/json" \
--request GET \
"http://localhost:8080/openidm/system/pingone/__ROLE__/1813bc13-8d13-4e88-a825-d40bfe82777b"
{
"_id": "1813bc13-8d13-4e88-a825-d40bfe82777b",
"applicableTo": [
"ORGANIZATION"
],
"name": "Organization Admin",
"description": "Organization Admin",
"permissions": [
{
"id": "advancedservices:read:config",
"classifier": "config",
"description": "Retrieve PingOne Advanced Services customer configuration"
},
{
"id": "authz:update:entity",
"classifier": "entity",
"description": "Update PingOne Authorize Entity"
},
{
"id": "pingintelligence:create:orchestration",
"classifier": "orchestration",
"description": "Creates a Orchestration flow for Ping Intelligence deployment"
},
{
"id": "authz:read:entity",
"classifier": "entity",
"description": "Read PingOne Authorize Entity"
},
{
"id": "authz:create:condition",
"classifier": "condition",
"description": "Create a PingOne Authorize Condition"
},
{
"id": "authz:test:condition",
"classifier": "condition",
"description": "Test a PingOne Authorize Condition"
},
{
"id": "authz:create:service",
"classifier": "service",
"description": "Create a PingOne Authorize Service"
},
{
"id": "authz:read:recentdecisions",
"classifier": "recentdecisions",
"description": "Read Recent Decisions of a PingOne Authorize Decision Endpoint"
},
{
"id": "orgmgt:read:organization",
"classifier": "organization",
"description": "Read organizations"
},
{
"id": "pingenterprise:update:orchestration",
"classifier": "orchestration",
"description": "Updates Orchestration flow for Ping Enterprise deployment"
},
{
"id": "authz:read:condition",
"classifier": "condition",
"description": "Read a PingOne Authorize Condition"
},
{
"id": "authz:test:service",
"classifier": "service",
"description": "Test a PingOne Authorize Service"
},
{
"id": "pingenterprise:create:orchestration",
"classifier": "orchestration",
"description": "Creates a Orchestration flow for Ping Enterprise deployment"
},
{
"id": "orgmgt:read:environment",
"classifier": "environment",
"description": "Read environments"
},
{
"id": "authz:update:service",
"classifier": "service",
"description": "Update a PingOne Authorize Service"
},
{
"id": "pingintelligence:update:orchestration",
"classifier": "orchestration",
"description": "Updates Orchestration flow for Ping Intelligence deployment"
},
{
"id": "orgmgt:read:deployment",
"classifier": "deployment",
"description": "Read deployment resource"
},
{
"id": "authz:update:tag",
"classifier": "tag",
"description": "Create and Update PingOne Authorize Policy Version Tag"
},
{
"id": "authz:create:decisionendpoint",
"classifier": "decisionendpoint",
"description": "Create PingOne Authorize Decision Endpoint"
},
{
"id": "advancedservices:delete:environment",
"classifier": "environment",
"description": "Delete PingOne Advanced Services environment"
},
{
"id": "authz:create:entity",
"classifier": "entity",
"description": "Create PingOne Authorize Entity"
},
{
"id": "authz:test:entity",
"classifier": "entity",
"description": "Test PingOne Authorize Entity"
},
{
"id": "authz:delete:condition",
"classifier": "condition",
"description": "Delete a PingOne Authorize Condition"
},
{
"id": "authz:update:decisionendpoint",
"classifier": "decisionendpoint",
"description": "Update PingOne Authorize Decision Endpoint"
},
{
"id": "authz:delete:entity",
"classifier": "entity",
"description": "Delete PingOne Authorize Entity"
},
{
"id": "orgmgt:update:environment",
"classifier": "environment",
"description": "Update environment"
},
{
"id": "integrations:read:integration",
"classifier": "integration",
"description": "Read an integration in integration catalog"
},
{
"id": "authz:read:service",
"classifier": "service",
"description": "Read a PingOne Authorize Service"
},
{
"id": "authz:authorize:decisionendpoint",
"classifier": "decisionendpoint",
"description": "Request Decision from a PingOne Authorize Decision Endpoint"
},
{
"id": "visualization:create:exploration",
"classifier": "exploration",
"description": "Create data exploration"
},
{
"id": "bootstrap:read:bootstrap",
"classifier": "bootstrap",
"description": "Read bootstrap"
},
{
"id": "authz:delete:service",
"classifier": "service",
"description": "Delete a PingOne Authorize Service"
},
{
"id": "visualization:read:template",
"classifier": "template",
"description": "Read data exploration template"
},
{
"id": "pingenterprise:read:orchestration",
"classifier": "orchestration",
"description": "Retrieve Orchestration flow for Ping Enterprise deployment"
},
{
"id": "ratelimiting:read:rateLimits",
"classifier": "rateLimits",
"description": "Read rate limits"
},
{
"id": "authz:delete:attribute",
"classifier": "attribute",
"description": "Delete a PingOne Authorize Attribute"
},
{
"id": "authz:delete:adaptiveTrustPolicy",
"classifier": "adaptiveTrustPolicy",
"description": "Delete a PingOne Adaptive Trust Policy"
},
{
"id": "pingenterprise:delete:orchestration",
"classifier": "orchestration",
"description": "Deletes Orchestration flow for Ping Enterprise deployment"
},
{
"id": "visualization:read:exploration",
"classifier": "exploration",
"description": "Read data exploration"
},
{
"id": "authz:delete:processor",
"classifier": "processor",
"description": "Delete a PingOne Authorize Processor"
},
{
"id": "orgmgt:delete:environment",
"classifier": "environment",
"description": "Delete environment"
},
{
"id": "orgmgt:promote:environment",
"classifier": "environment",
"description": "Promote environment"
},
...
],
"__NAME__": "Organization Admin"
}
Available roles
Available roles is a virtual object class, not a native PingOne resource. The _id is a concatenation of two other GUIDs and the level of access the role grants in the following format:
scopeId:scopeType:roleId
|
The id for the associated scope type |
|
|
|
The role id |
Example available role:
{
"_id": "9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:0bd9c966-7664-4ac1-b059-0ff9293908e2",
"role": {
"id": "0bd9c966-7664-4ac1-b059-0ff9293908e2" (1)
},
"name": "ENVIRONMENT - Administrators: Identity Data Admin",
"scope": {
"id": "9da69b4c-8101-4db8-8cef-66a9a167b02e", (2)
"type": "ENVIRONMENT" (3)
},
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"__NAME__": "ENVIRONMENT - Administrators: Identity Data Admin"
}| 1 | roleId |
| 2 | scopeId |
| 3 | scopeType |
Read all available roles
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
'http://localhost:8080/openidm/system/pingone/__AVAILABLE_ROLE__?_queryFilter=true'
{
"result": [
{
"_id": "9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:0bd9c966-7664-4ac1-b059-0ff9293908e2",
"role": {
"id": "0bd9c966-7664-4ac1-b059-0ff9293908e2"
},
"name": "ENVIRONMENT - Administrators: Identity Data Admin",
"scope": {
"id": "9da69b4c-8101-4db8-8cef-66a9a167b02e",
"type": "ENVIRONMENT"
},
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"__NAME__": "ENVIRONMENT - Administrators: Identity Data Admin"
},
{
"_id": "9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:ce00e15f-f845-4df1-abf3-fdc4ff4e176c",
"role": {
"id": "ce00e15f-f845-4df1-abf3-fdc4ff4e176c"
},
"name": "ENVIRONMENT - Administrators: Identity Data Read Only",
"scope": {
"id": "9da69b4c-8101-4db8-8cef-66a9a167b02e",
"type": "ENVIRONMENT"
},
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"__NAME__": "ENVIRONMENT - Administrators: Identity Data Read Only"
},
...
],
"resultCount": 10,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}
Read a single available role
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
'http://localhost:8080/openidm/system/pingone/__AVAILABLE_ROLE__/9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:0bd9c966-7664-4ac1-b059-0ff9293908e2'
{
"_id": "9da69b4c-8101-4db8-8cef-66a9a167b02e:ENVIRONMENT:0bd9c966-7664-4ac1-b059-0ff9293908e2",
"role": {
"id": "0bd9c966-7664-4ac1-b059-0ff9293908e2"
},
"name": "ENVIRONMENT - Administrators: Identity Data Admin",
"scope": {
"id": "9da69b4c-8101-4db8-8cef-66a9a167b02e",
"type": "ENVIRONMENT"
},
"environment": {
"id": "d182d341-2739-4082-975f-bc94396a9651"
},
"__NAME__": "ENVIRONMENT - Administrators: Identity Data Admin"
}
Supported search filters
The PingOne connector supports filtered searches against PingOne resources. However, certain limitations imposed by the PingOne APIs prevent the filtering of resource types based on arbitrary attributes and values. For a complete list, refer to Limiting and Filtering data in the PingOne documentation.
OpenICF Interfaces Implemented by the PingOne Connector
The PingOne Connector implements the following OpenICF interfaces. For additional details, see ICF interfaces:
- Create
-
Creates an object and its
uid. - Delete
-
Deletes an object, referenced by its
uid. - Schema
-
Describes the object types, operations, and options that the connector supports.
- Script on Connector
-
Enables an application to run a script in the context of the connector.
Any script that runs on the connector has the following characteristics:
-
The script runs in the same execution environment as the connector and has access to all the classes to which the connector has access.
-
The script has access to a
connectorvariable that is equivalent to an initialized instance of the connector. At a minimum, the script can access the connector configuration. -
The script has access to any script arguments passed in by the application.
-
- Search
-
Searches the target resource for all objects that match the specified object class and filter.
- Test
-
Tests the connector configuration.
Testing a configuration checks all elements of the environment that are referred to by the configuration are available. For example, the connector might make a physical connection to a host that is specified in the configuration to verify that it exists and that the credentials that are specified in the configuration are valid.
This operation might need to connect to a resource, and, as such, might take some time. Do not invoke this operation too often, such as before every provisioning operation. The test operation is not intended to check that the connector is alive (that is, that its physical connection to the resource has not timed out).
You can invoke the test operation before a connector configuration has been validated.
- Update
-
Updates (modifies or replaces) objects on a target resource.
PingOne Connector Configuration
The PingOne Connector has the following configurable properties:
Configuration properties
| Property | Type | Default | Encrypted(1) | Required(2) |
|---|---|---|---|---|
|
|
|
|
Yes |
The environment identifier. |
||||
(1) Whether the property value is considered confidential, and is therefore encrypted in IDM.
(2) A list of operations in this column indicates that the property is required for those operations.
Basic Configuration Properties
| Property | Type | Default | Encrypted(1) | Required(2) |
|---|---|---|---|---|
|
|
|
|
Yes |
The service endpoint URI. |
||||
|
|
|
|
Yes |
The service login name. |
||||
|
|
|
Yes |
No |
The service user password. |
||||
|
|
|
|
Yes |
Defines which method is to be used to authenticate on the remote server. Options are BASIC (username/password), OAUTH (Client id/secret) or TOKEN (static token). |
||||
|
|
|
|
No |
When using OAUTH as authentication method, this property defines the endpoint where a new access token should be queried for (https://myserver.com/oauth2/token). |
||||
|
|
|
|
Yes |
The client identifier for OAuth2. |
||||
|
|
|
Yes |
No |
Secure client secret for OAuth2. |
||||
|
|
|
Yes |
No |
Static authentication token. |
||||
|
|
|
|
Yes |
To be used for debug/test purposes. To be avoided in production. |
||||
|
|
|
|
Yes |
To be used for debug/test purposes. To be avoided in production. |
||||
|
|
|
|
Yes |
Content compression is enabled by default. Set this property to true to disable it. |
||||
|
|
|
|
Yes |
If TLS Mutual Auth is needed, set this to the certificate alias from the keystore. |
||||
|
|
|
Yes |
Yes |
If TLS Mutual Auth is needed and the client certificate (private key) password is different from the keystore password, set this to the client private key password. |
||||
|
|
|
|
Yes |
Defines the max size of the HTTP connection pool used. |
||||
|
|
|
|
Yes |
Defines the Hostname if an HTTP proxy is used between the connector and the service. |
||||
|
|
|
|
Yes |
Defines the Port if an HTTP proxy is used between the connector and the service. |
||||
|
|
|
|
Yes |
Defines Proxy Username if an HTTP proxy is used between the connector and the service. |
||||
|
|
|
Yes |
Yes |
Defines Proxy Password if an HTTP proxy is used between the connector and the service. |
||||
|
|
|
|
No |
Defines a timeout for the underlying HTTP connection in seconds. |
||||
|
|
|
|
No |
Used by the refresh_token grant type. |
||||
|
|
|
|
No |
The OAuth2 grant type to use (client_credentials or refresh_token). |
||||
|
|
|
|
No |
The OAuth2 scope to use. |
||||
|
|
|
|
No |
The prefix to be used in the Authorization HTTP header for Token authentication. |
||||
|
|
|
|
Yes |
The Authentication method for refresh token (Basic Authentication or Sending the ClientId and Client Secret in the Header). |
||||
(1) Whether the property value is considered confidential, and is therefore encrypted in IDM.
(2) A list of operations in this column indicates that the property is required for those operations.