Social Google node
Duplicates OAuth 2.0 node, but is preconfigured to work with Google.
You specify only the Client ID and Client Secret.
|
This node and its related services, are deprecated. For information about the legacy/deprecated social authentication node and module implementations, refer to Social authentication in the ForgeRock Access Management 7 Authentication and Single Sign-On Guide. |
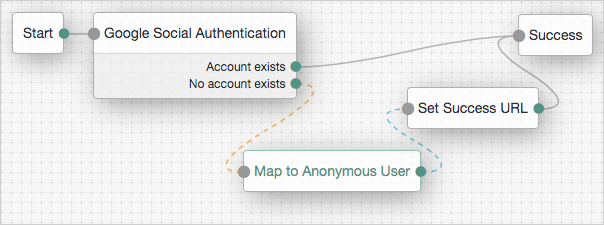
Outcomes
-
Account exists -
No account exists
Evaluation continues along the Account Exists path
if an account matching the attributes retrieved from Google are found in the user data store;
otherwise, evaluation continues along the No account exists path.
Properties
| Property | Usage | ||
|---|---|---|---|
Client ID (required) |
Specifies the |
||
Client Secret (required) |
Specifies the |
||
Authentication Endpoint URL |
Specifies the URL to the social provider’s endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework (RFC 6749). Default: |
||
Access Token Endpoint URL |
Specifies the URL to the endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework (RFC 6749). Default: |
||
User Profile Service URL |
Specifies the user profile URL that returns profile information. Default: |
||
OAuth Scope |
Specifies a space-separated list of user profile attributes the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions the resource owner, such as the end user, grants to the client application. Default: |
||
Redirect URL |
Specifies the URL the user is redirected to by Google after authenticating to continue the flow. Set this property to the URL of the AM UI.
For example,
|
||
Social Provider |
Specifies the name of the social provider for which this node is being set up. Default: |
||
Auth ID Key |
Specifies the attribute the social identity provider uses to identify an authenticated individual. Default: |
||
Use Basic Auth |
Specifies that the client uses HTTP Basic authentication when authenticating to Google. Default: |
||
Account Provider |
Specifies the name of the class that implements the account provider. Default: |
||
Account Mapper |
Specifies the name of the class that implements the method of locating local accounts based on the attributes returned from Google. Default: |
||
Attribute Mapper |
Specifies the list of fully qualified class names for implementations that map attributes from Google to AM profile attributes. Default:
|
||
Account Mapper Configuration |
Specifies the attribute configuration used to map the account of the user
authenticated in the Social Google provider to the local data store in AM.
Valid values are in the form Default:
|
||
Attribute Mapper Configuration |
Map of Google user account attributes to local user profile attributes,
with values in the form Default:
|
||
Save attributes in the session |
When enabled, saves the attributes in the Attribute Mapper Configuration field to the AM session. Default: |
||
OAuth 2.0 Mix-Up Mitigation Enabled |
Controls whether the authentication node carries out additional verification steps when it receives the authorization code from the authorization server. Specifies that the client must compare the issuer identifier of the authorization server
upon registration with the issuer value returned as the The Token Issuer property must be entered when the OAuth 2.0 Mix-Up Mitigation feature is enabled,
so that the validation can succeed.
The authorization code response contains an issuer value ( For more information, refer to section 4 of OAuth 2.0 Mix-Up Mitigation Draft. |
||
Token Issuer |
Corresponds to the expected issuer identifier value in the Example: |