Secure sensitive values
There are two ways to encode attribute values for managed objects—reversible encryption and salted hashing algorithms. Examples of encoded attribute values include passwords, authentication questions, credit card numbers, and social security numbers. If passwords are already encoded on the external resource, they are generally excluded from the synchronization process. For more information, refer to Manage password policies.
You configure attribute value encoding, per schema property, in the managed object configuration. The following sections show how to use reversible encryption and salted hash algorithms to encode attribute values.
Reversible encryption
Reversible encryption secures your data by encrypting it with a key. You should use encryption in cases where you need to decrypt the sensitive data to synchronize it or provide it to another system.
Encryption keys are mapped to purposes in your project’s conf/secrets.json file. For more information, refer to Secret stores.
|
The following managed object configuration encrypts and decrypts the password attribute using the default idm.password.encryption purpose:
{
"objects" : [
{
"name" : "user",
...
"schema" : {
...
"properties" : {
...
"password" : {
"title" : "Password",
...
"encryption" : {
"purpose" : "idm.password.encryption"
},
"scope" : "private",
}
...
}
]
}You specify the encryption cipher or keysize by specifying a cipher property of the related encryption object in your configuration.
The cipher property must be a valid transformation string as described in the javax.crypto.Cipher reference. The following example demonstrates using the transformation AES/GCM/NoPadding:
...
"encryption" : {
"purpose": "idm.password.encryption",
"cipher": "AES/GCM/NoPadding"
},By default, IDM uses AES/CBC/PKCS5Padding—the Advanced Encryption Standard (AES) algorithm with cipher block chaining, PKCS#5 padding, and a key size of 128.
|
If you change the default cipher, you must specify the algorithm, mode, and padding. If the algorithm does not require a mode, use |
To encrypt attribute values from the command-line, refer to encrypt.
Salted hash algorithms
To encode attribute values with salted hash algorithms, add the secureHash property to the attribute definition and define the hashing configuration. The configuration depends on the algorithm that you choose.
If you do not specify an algorithm, SHA-256 is used by default. MD5 and SHA-1 are supported for legacy reasons, but should not be used in production environments.
| Algorithm | Config Property and Description | ||
|---|---|---|---|
|
|
||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
The following list displays supported hash algorithms and example configurations:
SHA-256-
"secureHash" : { "algorithm" : "SHA-256", "saltLength" : 16 } SHA-384-
"secureHash" : { "algorithm" : "SHA-384", "saltLength" : 16 } SHA-512-
"secureHash" : { "algorithm" : "SHA-512", "saltLength" : 16 } Bcrypt-
"secureHash" : { "algorithm" : "BCRYPT", "cost" : 16 } Scrypt-
"secureHash" : { "algorithm" : "SCRYPT", "hashLength" : 16, "saltLength" : 16, "n" : 32768, "r" : 8, "p" : 1 } - Password-Based Key Derivation Function 2 (
PBKDF2) -
"secureHash" : { "algorithm" : "PBKDF2", "hashLength" : 16, "saltLength" : 16, "iterations" : 10, "hmac" : "SHA-256" }
|
Some one-way hash functions are designed to be computationally expensive. Functions such as PBKDF2, Bcrypt, and Scrypt are designed to be relatively slow even on modern hardware. This makes them generally less susceptible to brute force attacks. However, computationally expensive functions can dramatically increase response times. If you use these functions, be aware of the performance impact and perform extensive testing before deploying your service in production. Do not use functions like PBKDF2 and Bcrypt for any accounts that are used for frequent, short-lived connections. Hashing is a one-way operation, such that the original value cannot be recovered. Therefore, if you hash the value of any property, you cannot synchronize that property value to an external resource. For managed object properties with hashed values, you must either exclude those properties from the mapping or set a random default value if the external resource requires the property. |
The following excerpt of a managed object configuration shows that values of the password attribute are hashed using the SHA-256 algorithm:
{
"objects" : [
{
"name" : "user",
...
"schema" : {
...
"properties" : {
...
"password" : {
"title" : "Password",
...
"secureHash" : {
"algorithm" : "SHA-256"
},
"scope" : "private",
}
...
}
]
}To hash attribute values from the command-line, refer to secureHash.
Configure hashing using the admin UI
You can set a property hash algorithm using the admin UI. However, only some algorithms and none of the enhanced configuration options are supported.
Show Me
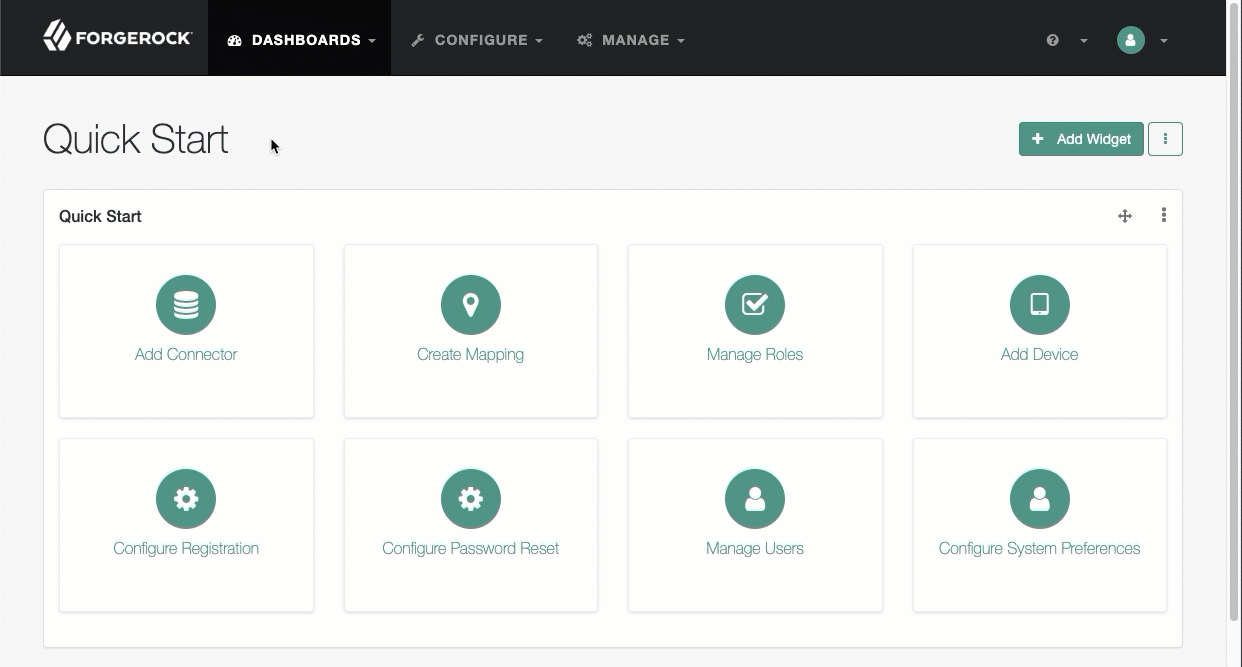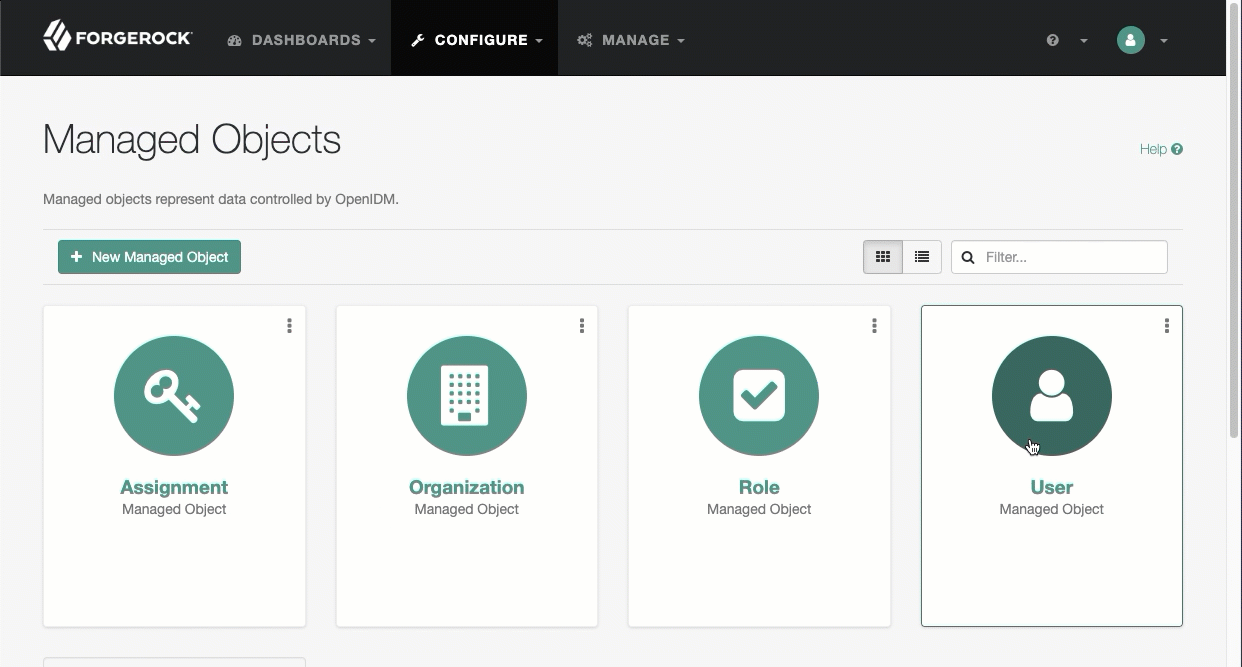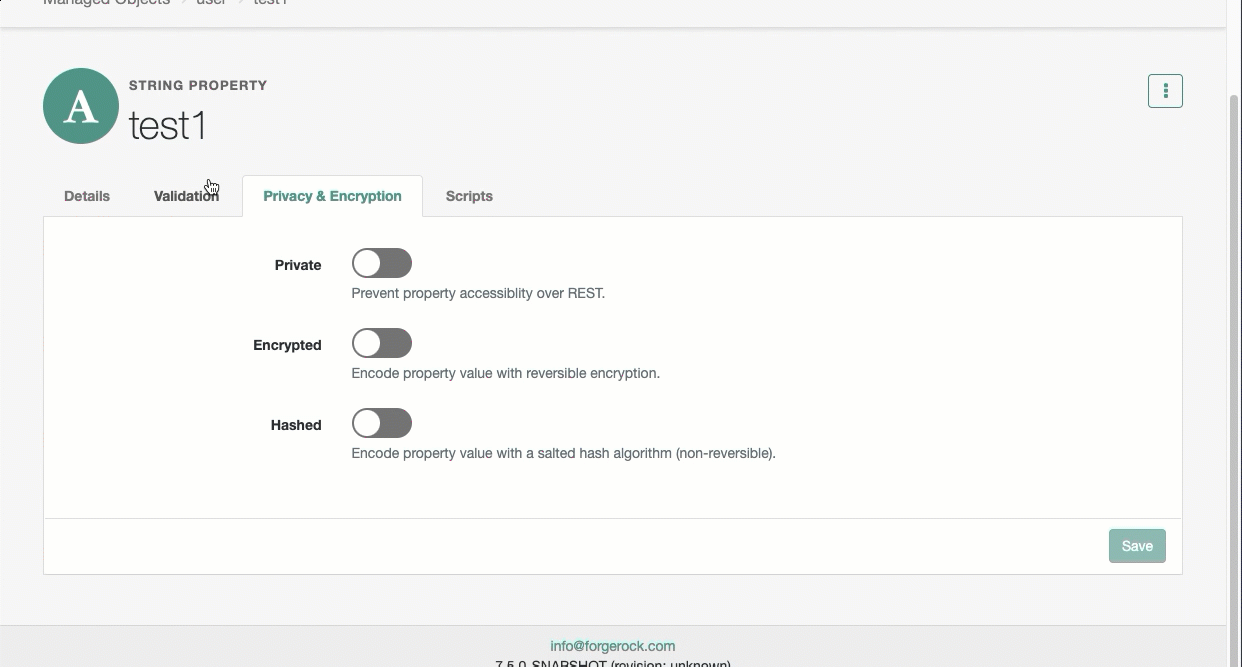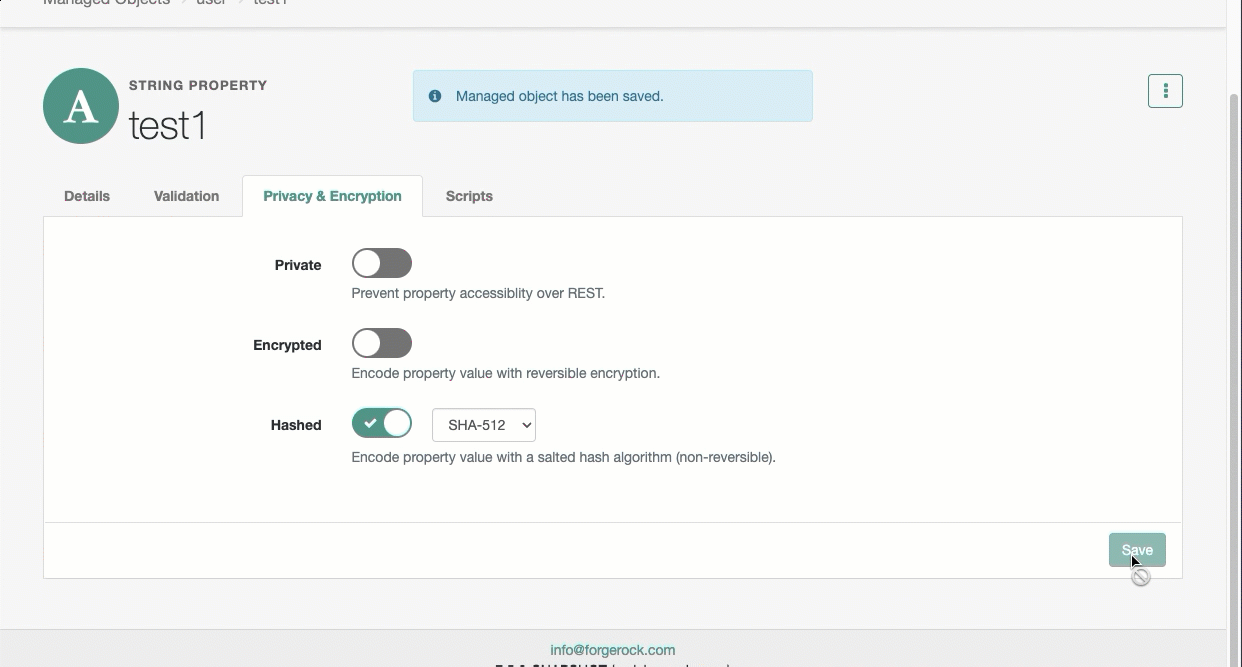
-
Select Configure > Managed Objects, and select an object type (for example, User).
-
On the Properties tab, select a property to hash.
-
On the Property Name page, click the Privacy & Encryption tab, and select Hashed.
-
From the adjacent drop-down menu, select an algorithm.
-
Click Save.