Configure Linux SSH to use Windows RADIUS proxy for MFA
With the Windows RADIUS proxy installed and configured on a Windows machine, you are ready to add MFA to an SSH login on Linux.
This use case is explored in this section.
|
The subsequent sections and examples utilize the Red Hat Enterprise Linux (RHEL) distribution. The commands can vary slightly. For example, RHEL uses The following subsections assume you are logged into the Linux terminal as the root user or equivalent. |
Prerequisites
Before setting up the SSH login on a Linux machine to use MFA via the Windows RADIUS proxy, you must:
-
Install the Windows RADIUS proxy.
-
Validate and test the Windows RADIUS proxy.
-
Establish network connectivity between the Linux machine(s) and the Windows machine(s).
-
Confirm all usernames (profiles/accounts) match from the Linux machine(s)> ForgeRock and vice versa.
-
Set up a connector from ForgeRock to the datastore and sync the data.
-
The ForgeRock journey validates the credentials when you configure MFA on an SSH login for Linux.
-
-
Confirm users pre-register in the appropriate journey if required. For example, for the push MFA method, users download the ForgeRock Authenticator application. For more information, refer to Windows RADIUS proxy prerequisites.
|
Ensure you properly patch, lock down, and harden the Linux machine(s) you expose to the Windows RADIUS proxy. |
Install required packages
Packages are required to install relevant RADIUS configurations.
-
Install the EPEL release by running the following command:
sudo yum install epel-release -
Install the PAM RADIUS client by running the following command:
sudo yum install pam_radius.x86_64 -
Using an RPM command, verify that the installations were successful.
|
If any of the install commands return as not found by the package manager, locate the appropriate package name via an internet search as these are subject to change slightly depending on your Linux distribution. |
Configure PAM RADIUS
After you install the required packages (which installs the PAM RADIUS), you must configure the PAM RADIUS module.
-
Edit the
/etc/pam_radius.conffile (using vim or an equivalent text editor). -
In the file, remove all entries below the
127.0.0.1entry, under the table# server[:port] shared_secret timeout (s). -
Add an entry using the syntax
<WindowsRADIUSProxyIPAddress>:<portOfProxy> <Windows RADIUS Secret> <timeoutInSeconds>.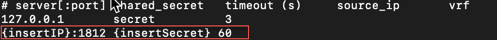 Figure 1. Linux PAM RADIUS configuration
Figure 1. Linux PAM RADIUS configuration
Configure SSH Daemon
After the PAM RADIUS configurations are complete, the sshd configuration must be updated to utilize the RADIUS settings on SSH login.
-
Edit the
/etc/pam.d/sshdfile (using vim or an equivalent text editor). -
Add the following line to the top of the file:
auth required /usr/lib64/security/pam_radius_auth.soThis line instructs Linux that for authentication, use the PAM RADIUS configurations. It requires the authentication service to enforce users to log in via the Windows RADIUS proxy. For more information on this, refer to RHEL’s documentation.
-
Save changes and exit the file.
-
Restart the
sshdservice:sudo systemctl restart sshd.service
|
Verify these changes with a test user and machine before applying them to your environments. Ensure the selected MFA method (defined in Install Windows RADIUS proxy) works with the test user. Failure to confirm this successfully may result in users being locked out of the Linux machine(s). |
Verify and test functionality
With the Windows RADIUS proxy installed and tested, the required packages installed on the Linux machine(s), and relevant configuration changes to PAM RADIUS and the SSH Daemon, you are ready to verify and test SSH login with a user.
|
Ensure the user you test in your Linux environment matches what is in your ForgeRock environment. |
Add a Linux user
To add a user on a Linux machine:
-
Create the user:
adduser <username> -
Modify the password of the newly created user:
passwd <username>You will be prompted to enter and re-enter the password of the user.
|
Create the user in your ForgeRock environment with the same username and password for testing. In a production scenario, syncing should be set up. |
Perform SSH login
After you create a test user in the Linux environment with an equivalent account in the ForgeRock environment, you are ready to perform an SSH login test. The below steps assume the push MFA method was configured in the Windows RADIUS proxy setup.
-
Initiate an SSH connection to the target Linux machine.
-
Enter the username and password as prompted. A push notification should appear on your phone.
-
Tap Approve on the ForgeRock Authenticator application.
-
Verify that you have successfully logged into the Linux terminal with a valid session.