Create authentication journey(s)
To enable workstation authentication integration, you need to create relevant journeys to support the MFA authentication method(s) you want. These journeys allow workstation authentication to work directly with the ForgeRock environment.
Since Enterprise Connect integrates with Identity Cloud or self-managed Access Management, the examples that follow depict the various UI changes between the two.
|
Do not deviate from the following journeys when you configure Enterprise Connect or use the journeys you create for any other purpose (including repurposing the journeys). You must strictly follow the placement of the nodes to ensure the product works correctly. Failure to do so or the addition of other nodes could result in unexpected behavior. |
Example of push journey
The push journeys for Enterprise Connect allow users to approve a push notification from the ForgeRock Authenticator application. End users must download the ForgeRock Authenticator application and pre-register (from another journey you define) to be able to use the push journeys.

If you configure Use credentials in the MSI Updater client, then you must include the Platform Password and Data Store Decision nodes. Otherwise, you must omit these nodes in your journey configuration.
| When configuring the push journey in Identity Cloud, you must enable services in the AM admin UI (native console). For more information, refer to Create a push authentication journey. |
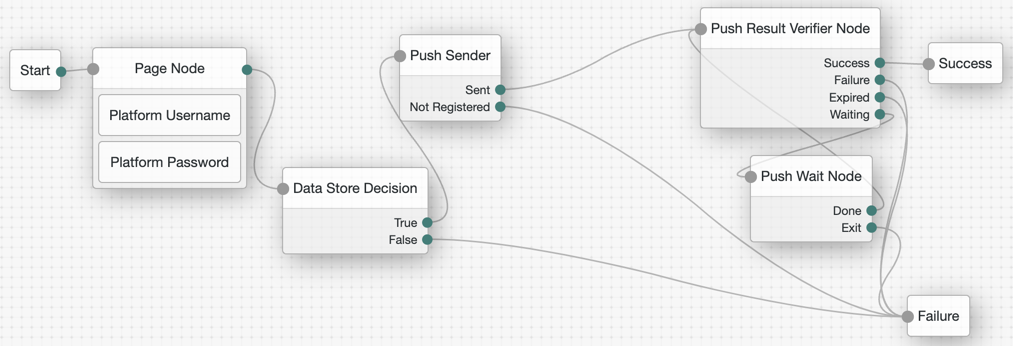
If you configure Use credentials in the MSI Updater client, then you must include the Platform Password and Data Store Decision nodes. Otherwise, you must omit these nodes in your journey configuration.
| When configuring the push journey in Access Management, you must enable services in the AM admin UI (self managed). For more information, refer to Create a push authentication journey. |
Example of OTP from authenticator app journey
The following journeys show the OTP that is presented from the ForgeRock Authenticator application. End users must download the ForgeRock Authenticator application and pre-register (from another journey you define) to be able to use the OTP journeys.

If you configure Use credentials in the MSI Updater client, then you must include the Platform Password and Data Store Decision nodes. Otherwise, you must omit these nodes in your journey configuration.
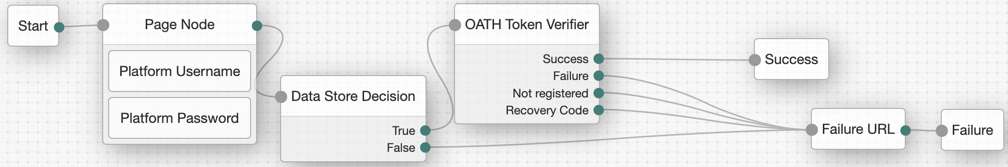
If you configure Use credentials in the MSI Updater client, then you must include the Platform Password and Data Store Decision nodes. Otherwise, you must omit these nodes in your journey configuration.
Example of OTP SMS/email/voice call journey
The following journeys show the OATH OTP (HOTP) that can be presented to an end user via SMS/email/voice. Ensure end users have the appropriate data in their user profile to facilitate the MFA method(s) you allow an end user to select.
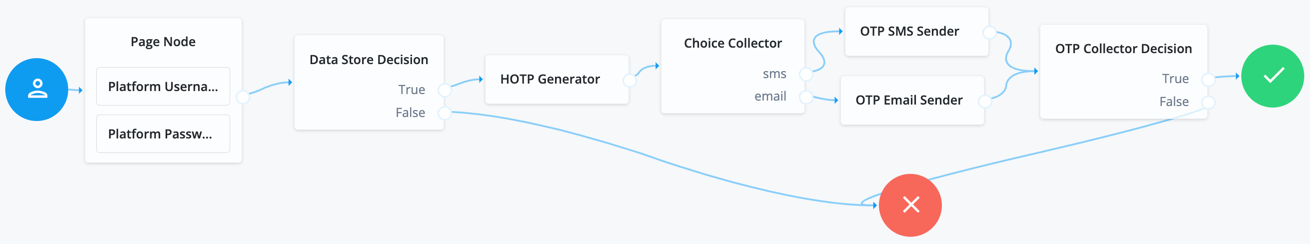
If you configure Use credentials in the MSI Updater client, then you must include the Platform Password and Data Store Decision nodes. Otherwise, you must omit these nodes in your journey configuration.
|
In the Choice Collector node, the options correlate to the following MFA methods within Windows Workstation Authentication:
Therefore, ensure SMS is the first choice in the node, followed by email. If voice call is a method you configure, it must be the third option. Do not deviate from this order. |
If you choose to use the voice option, you could use the Twilio nodes (you must have a valid subscription with Twilio).
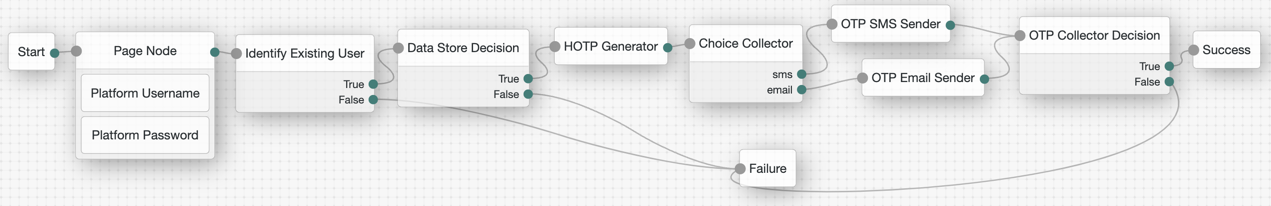
If you configure Use credentials in the MSI Updater client, then you must include the Platform Password and Data Store Decision nodes. Otherwise, you must omit these nodes in your journey configuration.
|
In the Choice Collector node, the options correlate to the following MFA methods within Windows Workstation Authentication:
Therefore, ensure SMS is the first choice in the node, followed by email. If voice call is a method you configure, it must be the third option. Do not deviate from this order. |
If you choose to use the voice option, you could use the Twilio nodes (you must have a valid subscription with Twilio).
Example of SSO journey
The following journeys depict the flow that Enterprise Connect uses after a user authenticates to their workstation. The end user ForgeRock environment opens in a default browser.
If you configure the Enable SSO setting in the MSI Updater client, then this journey applies to you. In this setting, you must supply the journey URL.
An example SSO URL to enter in this field is http://<tenant-env-fqdn>/am/XUI/?realm=alpha&authIndexType=service&authIndexValue=sso-journey&ForceAuth=true.
The authIndexValue references the journey to use for SSO. Ensure to add ForceAuth=true to the end of your SSO URL.
|
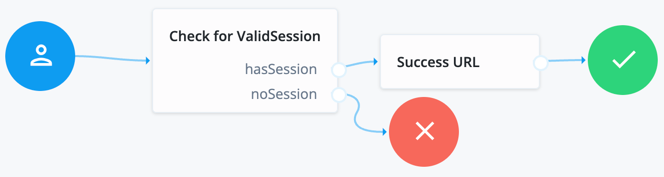
The Check for ValidSession node (shown in the image above) is the Scripted Decision node. In this example, it references a simple authentication JavaScript script:
if (typeof existingSession !== 'undefined')
{
outcome = "hasSession";
}
else
{
outcome = "noSession";
}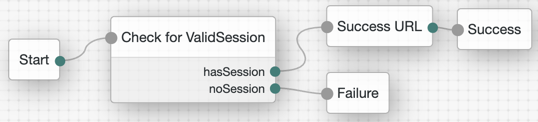
The Check for ValidSession node (shown in the image above) is the Scripted Decision node. In this example, it references a simple authentication JavaScript script:
if (typeof existingSession !== 'undefined')
{
outcome = "hasSession";
}
else
{
outcome = "noSession";
}-
Download and install the binaries from Backstage (you must be logged in). This includes the base MSI file as well as the MSI Updater client.
-
Pre-configure the relevant journey(s).
-
Install the MSI Updater client on an administrative Windows machine.
-
Configure the MSI Updater client specific to your organization’s needs.
-
(Optional) Consider additional configurations.
-
Deploy the generated MSI file through your desired mechanism.
-
Verify and test your deployment.