Integrate with PingOne Protect for risk evaluations
The ForgeRock SDKs can integrate with PingOne Protect to evaluate the risk involved in a transaction.
|
Integration with PingOne Protect in journeys is only available in self-managed ForgeRock Access Management 7.5 and later. |
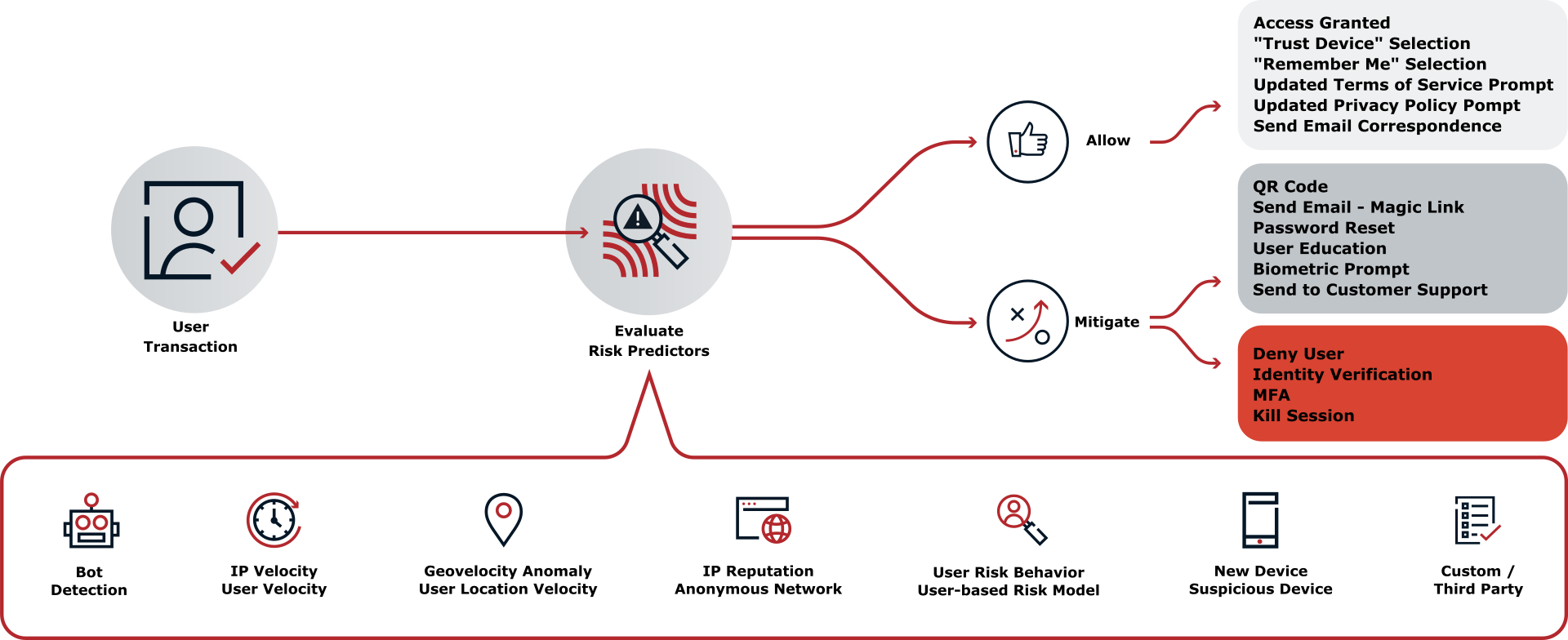
You can instruct the ForgeRock SDKs to use the embedded PingOne Signals SDK to gather information during a transaction. Your authentication journeys can then gather this information together and request a risk evaluation from PingOne.
Based on the response, you can choose whether to allow or deny the transaction or perform additional mitigation, such as bot detection measures.
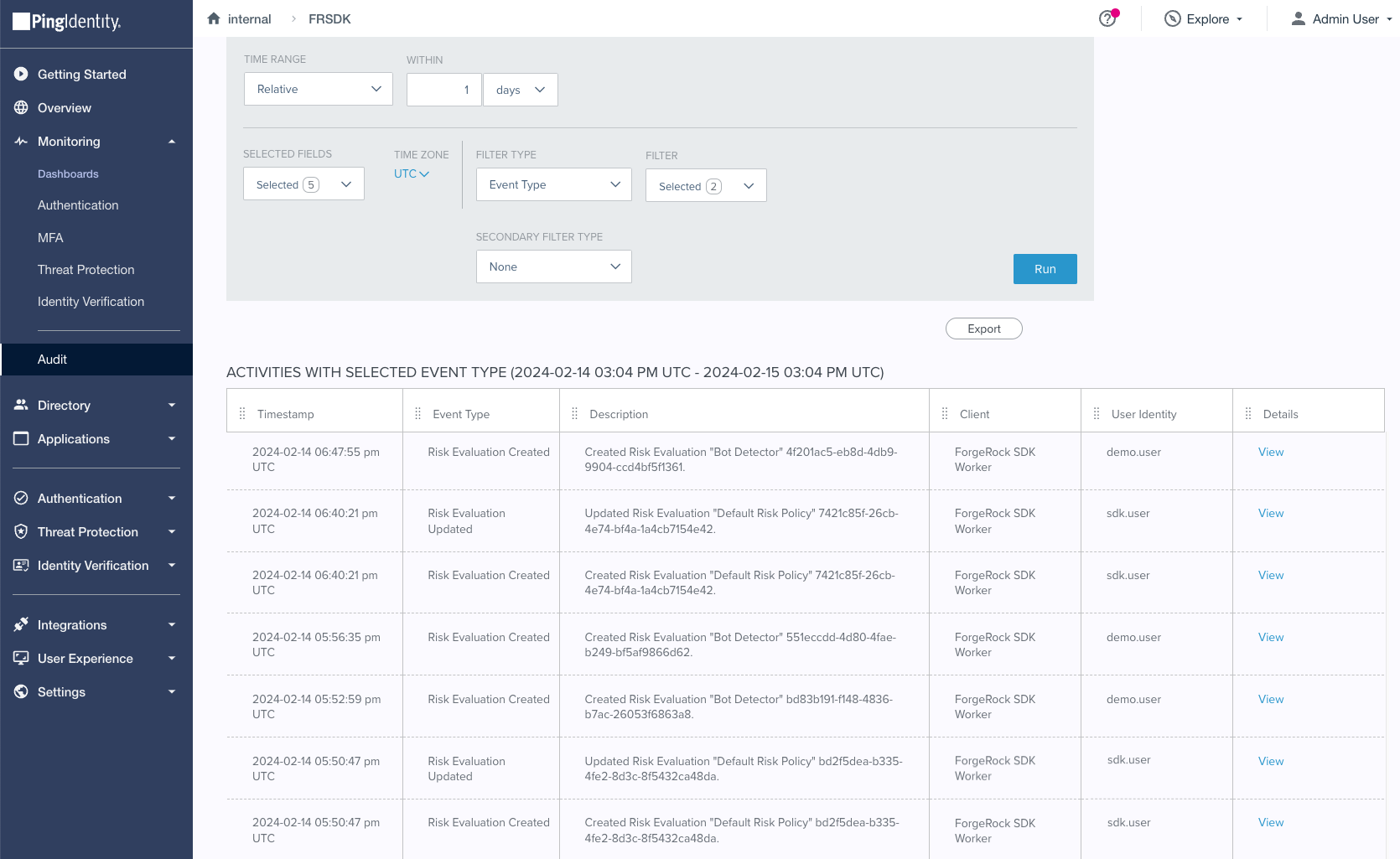
You can use the audit functionality in PingOne to view the risk evaluations:
Steps
- Step 1. Set up the servers
-
In this step, you set up your ForgeRock and PingOne servers to perform risk evaluations.
For example, you create a worker application in PingOne and configure your ForgeRock server to access it. You also create an authentication journey that uses the relevant nodes.
- Step 2. Install dependencies
-
In this step, you add the required PingOne Protect module and dependencies to your project.
We provide instructions for Android, iOS, and JavaScript projects.
- Step 3. Develop the client app
-
With everything prepared, you can now add ForgeRock SDK code to your client application to evaluate risk by using PingOne Protect.
You’ll learn how to initialize the collection of contextual data, gather and send it to the server for a risk evaluation, and how to pause and resume behavioral data collection.