PingOne Protect
PingOne Protect is a centralized identity threat protection service, securing your digital assets against online fraud attempts, such as account takeover and fraudulent new account registration. This cloud-based system uses artificial intelligence (AI) and machine-learning (ML) algorithms to perform real-time risk analysis on online events, specifically detecting fraudulent activities during authentication, authorization, registration, and transaction processes.
For example, enterprises implementing a Zero Trust model can create a user authentication journey where:
-
Employees authenticated by using FIDO2 security keys and assessed as low risk can directly access the system.
-
Users assessed as medium risk can be required to use an alternate authentication method to verify their identity.
-
Users assessed as high risk can be denied access completely.
Businesses using Identity Cloud can maximize the benefits of the PingOne Protect service by seamlessly integrating it into their tenants.
This guide offers step-by-step instructions for this integration. For more detailed documentation on PingOne Protect, refer to Threat Protection using PingOne Protect. For those familiar to PingOne Protect, refer directly to the Integrating PingOne Protect into Identity Cloud.
How the PingOne Protect integration works
PingOne Protect is a cloud-based service running AI/ML analytics on incoming and external signals. Companies can integrate PingOne Protect into cloud-based (public, private, and hybrid), on-prem, and self-hosted networks.
|
Please note, this integration only targets Identity Cloud hosted pages. In a future release, support for native devices will be incorporated through the ForgeRock SDK. |
The following overview explains how the integration of the PingOne Protect service on the Identity Cloud works:
The user flow for PingOne Protect integration is as follows:
-
The client sends a request to the Identity Cloud journey, with the Initialize node as the first node in the journey.
-
The Initialize node sends a response to initialize the PingOne Protect Web SDK to start collecting data.
-
The PingOne Protect Evaluation node retrieves the data from the client through a callback.
The PingOne Protect Evaluation node makes an access request to the PingOne Service. The PingOne Service obtains an access token from the PingOne API token endpoint. This token is then forwarded to the PingOne Protect Evaluation node, allowing the node to transmit the required data to the PingOne server for conducting risk evaluations. Administrators need to configure the PingOne Service on Identity Cloud. -
The Evaluation node sends data to the PingOne Protect service for risk evaluation. Administrators must configure policies on PingOne Protect for the specific risk predictors, risk scores, and risk levels. The PingOne Protect service sends the risk evaluation results back to the Evaluation node.
-
The Identity Cloud journey continues as dictated by the nodes based on the risk levels: for pass-through or some type of mitigation, such as multifactor authentication or denial of access.
-
The Result node gets an access token from the PingOne Service and sends the journey result (success or failure) back to the PingOne Protect service to improve the training models.
-
PingOne Protect service displays the risk event on its dashboard.
PingOne Protect components
The following section presents a general overview of the PingOne Protect components for those new to this product. The components are:
For more detailed information, refer to the documentation Threat Protection using PingOne Protect.
Predictors
PingOne Protect uses predictors to detect threats. Some predictors are machine
learning heuristics that simplify and speed up risk analysis and threat
detection; while others are User Entity and Behavior Analytics (UEBA) properties
to detect anomalies in online user behavior and devices.
For example, one type of predictor is bot detection, which identifies
automated software scripts acting as an agent simulating human activity.
Malicious bots are known to send spam, break into user accounts, or steal
sensitive personal data. When a bot is detected, PingOne Protect marks it as a
high-risk event and recommends immediate bot mitigation.
For more details on each predictor, refer to PingOne Protect’s documentation at Predictors.
Risk evaluations
PingOne Protect uses risk evaluations to calculate the risk level and other details, for example, risk policy set ID, result, level, recommended action and others associated with the risk evaluation events. The policy then uses the aggregated risk score from the risk evaluation to calculate the levels based on the policy settings. You can use your risk evaluations to fine-tune your policies for accuracy.
The risk evaluation events are:
-
Risk evaluation created. An event where a risk threshold is set and PingOne Protect evaluates risk for an authentication event using configurable policies. The result generates a risk evaluation of
LOW,MEDIUM, orHIGH. -
Risk evaluation updated. An event where the risk model has been informed that the authentication attempt passed or not.
For more information, refer to Risk Evaluations.
Risk policies
Administrators must configure risk policies to use the predictors in the machine-learning analytics. Risk policies have many important functions, including:
-
Determining which predictor types and specific score to include in the risk calculations. Predictors can include default, custom, or composite.
-
Determining how each predictor should be taken into account when combining multiple predictors. For example, you can set the risk scores, numeric value ranges for predictor results.
-
Determining how the aggregated risk scores for the predictors should be translated into final risk levels:
LOW,MEDIUM, andHIGH. -
Defining any fallback values when a risk score could not be evaluated, such as when there is insufficient information to generate a score.
-
Defining any overrides for specific predictors, like
bot mitigation, to override any risk level with aHIGHrisk level.
PingOne Protect also provides a convenient Risk Policy assistant to help administrators create their policies as well as staging policies to test new policies before moving them to production.
For more details on properties, refer to Risk Policies.
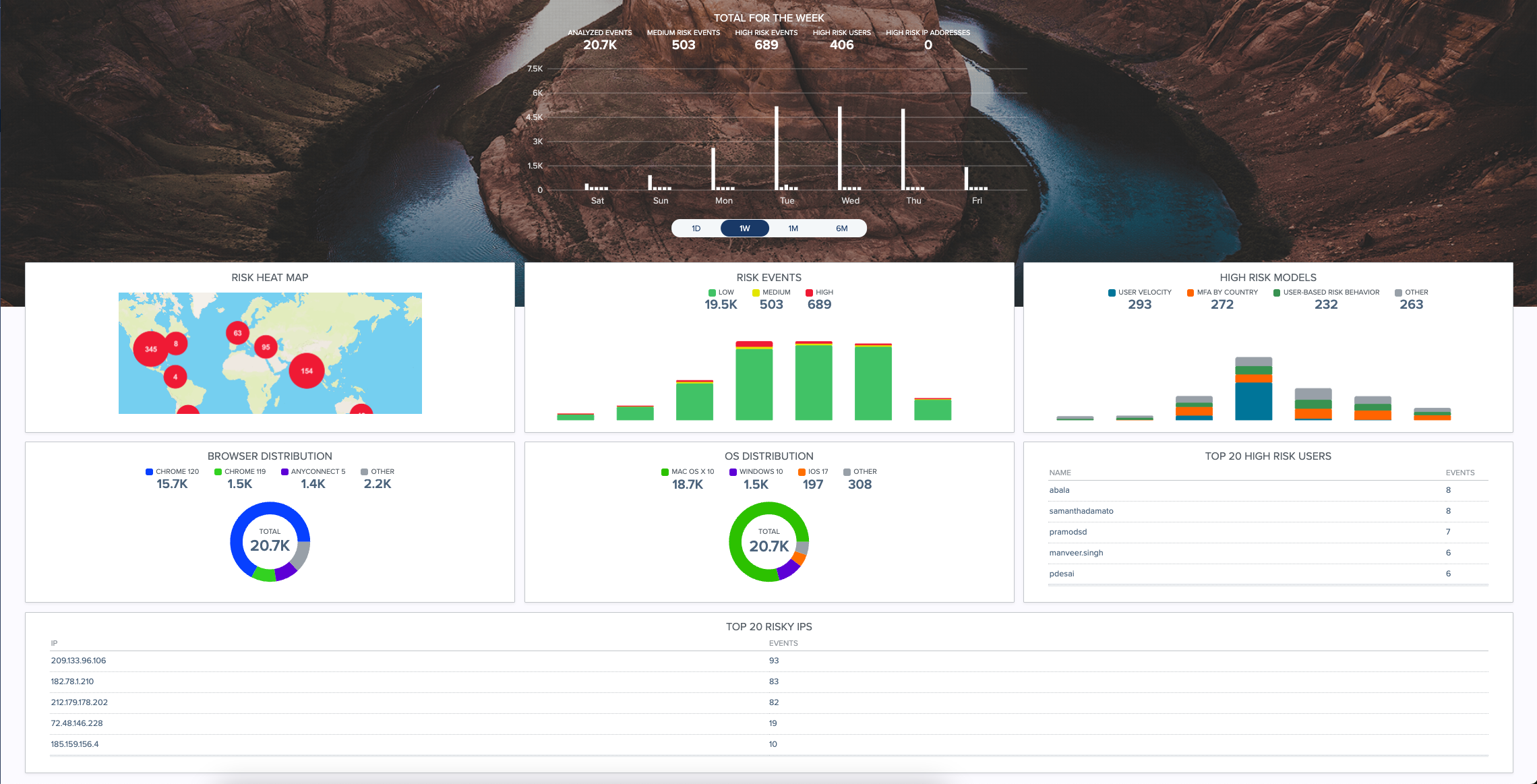
PingOne Protect Dashboard
PingOne Protect provides a graphical UI dashboard that displays the key metrics across your worldwide organization. Administrators can gain valuable insights into the types of risky events are occurring company-wide. The main dashboard has multiple panels, allowing you to view a summary for that particular metric. If you click the panel, you can view further details related to the metric.
You can view summary screens for the following:
-
Total for the week. Displays the total analyzed events for the past week.
-
Risk Heat Map. Displays a worldwide heat map where risky events occur.
-
Risk Events. Displays a bar chart of low, medium, and high-risk events for the week.
-
High-Risk Models. Displays a bar chart of high-risk models.
-
Browser Distribution. Displays a pie chart showing the browser type distribution of analyzed events.
-
OS Distribution. Displays a pie chart showing the operating system distribution of analyzed events.
-
Top 20 High-Risk Users. Displays the top 20 high-risk users by username and the number of events.
-
Top 20 Risk IPs. Displays the top 20 risky IPs by IP address and number of events.