About Identity Governance
|
Advanced Identity Cloud add-on capability
Contact your Ping Identity representative if you want to add PingOne® Identity Governance to your Advanced Identity Cloud subscription. |
Identity Governance lets you administer and manage end user access to applications and data across your company to support corporate and regulatory compliance. Identity Governance uses onboarded target applications when reviewing identity data.
With Identity Governance, you can:
-
Create and manage policies and policy rules, allowing end users to manage segregation of duties (SoD) violations.
-
Allow end users to gain access to the resources they need through access requests.
-
Review (certify) end users' access in onboarded target applications through access certifications, event-based certification, and access reviews.
-
Manage access requests by configuring workflows, end-to-end UI-based sequence of tasks that results in the approval or rejection of an access request.
-
Aggregate permissions into Advanced Identity Cloud to view user privileges in onboarded target applications using entitlements.
-
Attach custom attributes to applications, entitlements, and roles that you can use to extend the data you review using governance glossary attributes.
|
Ping Identity does not support Identity Governance actions for users authenticated in the Bravo realm of a tenant. Configuring Identity Governance in both Alpha and Bravo realms can cause issues since Identity Governance is not realm-aware. This may result in users gaining unauthorized access to customer data across realms and features. To avoid these issues, Ping Identity recommends setting up an Advanced Identity Cloud instance for your workforce/Identity Governance use cases using only the Alpha realm and another instance for your CIAM use cases using one or both realms depending on application. Contact your Ping Identity representative to discuss your particular deployment options. |
To access Identity Governance administration functions in Advanced Identity Cloud, you must be a tenant administrator.
When you purchase Identity Governance, the Governance-related menu items are added to the left navigation pane:
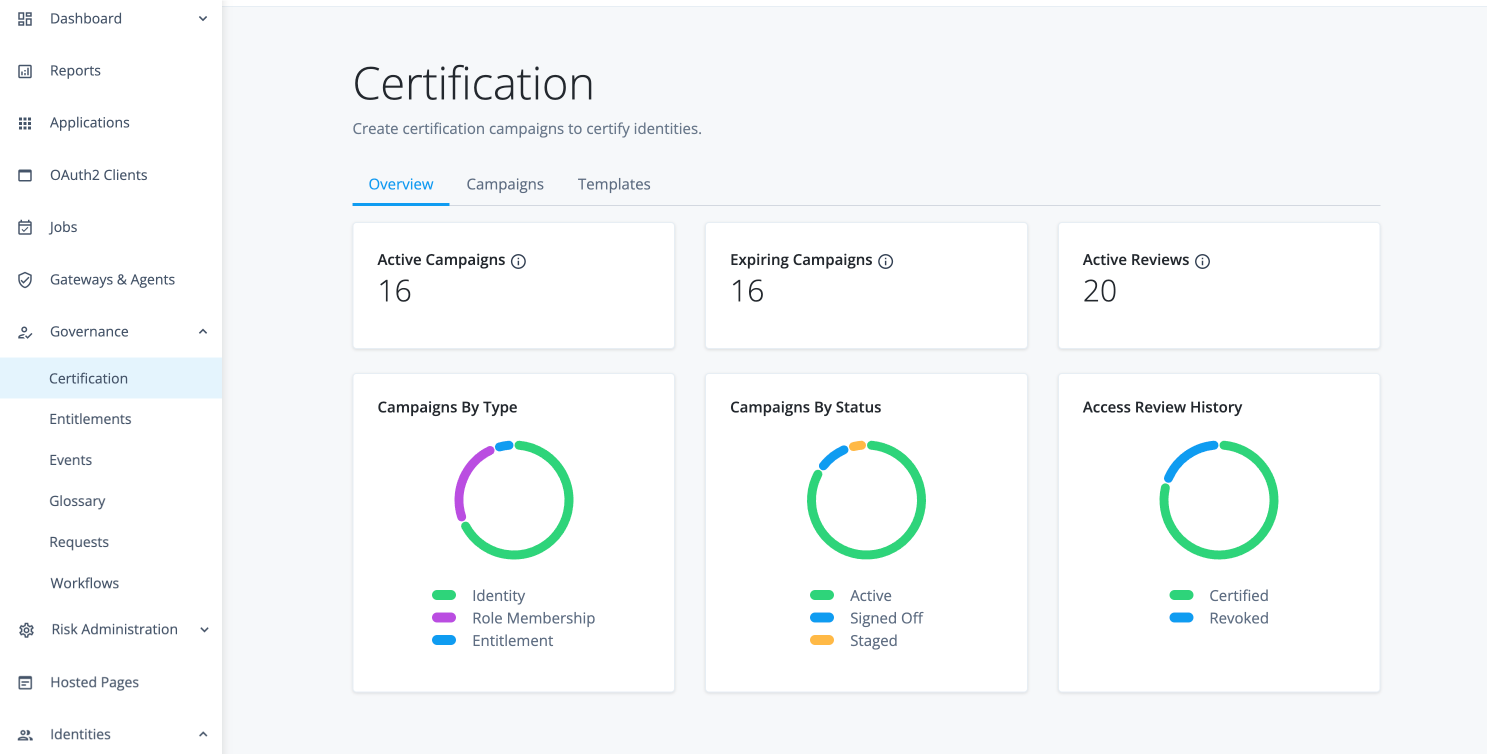
Additional menu items are also added to the End-user pages.