Pass-through auth (PTA) with Microsoft Entra ID (Azure AD)
Description
Estimated time to complete: 30 minutes
In this use case, you enable pass-through authentication (PTA) to Microsoft Entra ID (formerly Azure AD) and let Advanced Identity Cloud capture the Microsoft Entra ID password for future logins.
Goals
In completing this use case, you will learn how to do the following:
-
Use the Advanced Identity Cloud admin UI
-
Create an authentication journey enabling pass-through authentication for Microsoft Entra ID users provisioned to Advanced Identity Cloud
-
Capture passwords on successful pass-through authentication
Prerequisites
Before you start work on this use case, make sure you have:
-
A basic understanding of:
-
The Advanced Identity Cloud admin UI
-
Journeys
-
Nodes
-
Pass-through authentication
-
-
Completed the use case to Provision users from Microsoft Entra
-
A test user in Microsoft Entra ID and provisioned in Advanced Identity Cloud with the password to sign in as the test user
-
Access to your Advanced Identity Cloud development environment as an administrator
-
Access to your Microsoft Entra ID tenant environment as an administrator
Tasks
Task 1: Sign on to Microsoft Entra ID as the test user
This confirms you have the test user credentials and the test user is active in Microsoft Entra ID:
-
Browse to the sign-on page for Microsoft Azure.
-
Sign on as the test user.
-
If this is the first time the test user signed on, update the password and record the new password for pass-through authentication.
|
Do not enable multi-factor authentication for the test user. For this use case, the test user must be able to authenticate with only a username and password. |
Task 2: Confirm the test user account in Advanced Identity Cloud
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Application > Identities > Manage.
-
Find the Advanced Identity Cloud test user in the list.
If the test user doesn’t have a Advanced Identity Cloud account yet, provision the account from Microsoft Entra ID.
Task 3: Create a pass-through authentication journey
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Journeys > + New Journey and set at least the following before clicking Save:
Field Value NAME
PTA with password captureIdentity Object
managed/alpha_user -
Drag the following nodes onto the journey editor canvas:
-
Page node containing:
-
Platform Username node
-
Platform Password node
-
-
Data Store Decision node
-
Passthrough Authentication node
-
Identify Existing User node
-
Required Attributes Present node
-
Patch Object node
-
Increment Login Count node
-
Inner Tree Evaluator node
-
-
Connect the nodes, clicking Save from time to time to keep your work:
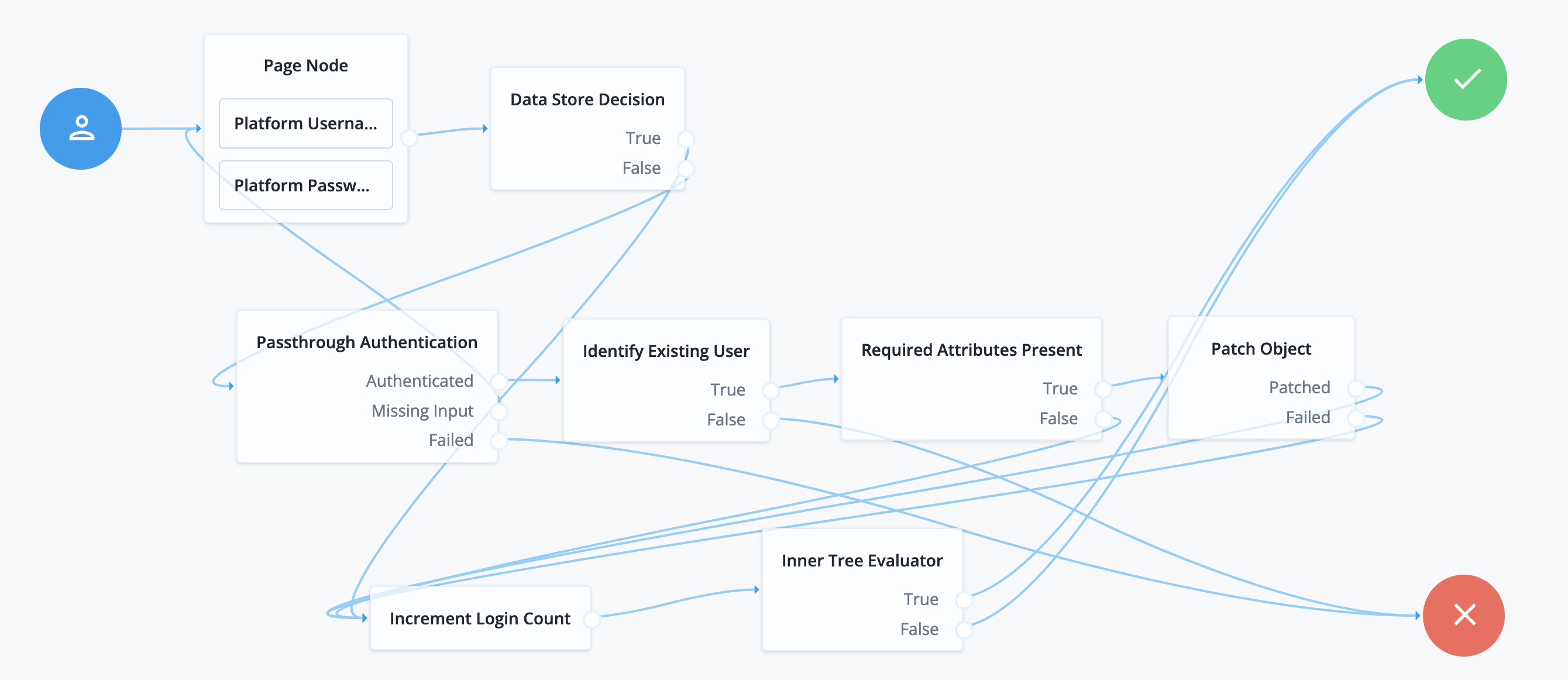
Source node Outcome path Target node Start (person icon)
→
Page node
Page node containing:
-
Platform Username node
-
Platform Password node
→
Data Store Decision node
Data Store Decision node
TrueIncrement Login Count node
FalsePassthrough Authentication node
Passthrough Authentication node
AuthenticatedIdentify Existing User node
Missing InputPage node
FailedFailure node
Identify Existing User node
TrueRequired Attributes Present node
FalseFailure node
Required Attributes Present node
TruePatch Object node
FalseIncrement Login Count node
Patch Object node
PatchedIncrement Login Count node
FailedIncrement Login Count node
Increment Login Count node
→
Inner Tree Evaluator node
Inner Tree Evaluator node
TrueSuccess node
FalseSuccess node
-
Task 4: Adjust node settings for the journey
Adjust the settings for the specified nodes as follows:
-
Configure these Page node settings and click Save:
Field Value Page Header
Key:
en, Value:Sign onPage Description
Key:
en, Value:This page uses pass-through authentication.All other fields
Accept the default settings, leaving the fields blank.
-
Configure these Passthrough Authentication node settings and click Save:
Field Value System Endpoint
The name of the connector for the provisioning application.
To find the name of the connector:
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Native Consoles > Identity Management.
-
On the Identity Management page, select Configure > Connectors.
-
Find the MSGraphAPI Connector.
It is named like the application, but the connector name does not include spaces; for example, an application named Microsoft Entra ID has a connector named
MicrosoftEntraID.
Object Type
Enter
User.To find the name of the object type:
-
On the Identity Management page, select Configure > Connector Name > Object Types.
-
Find the available types in the list.
Identity Attribute
Keep
userName.Password Attribute
Keep
password. -
-
Configure these Identify Existing User node settings and click Save:
Field Value Identifier
Keep
userName.Identity Attribute
Enter
userName. -
Configure these Required Attributes Present node settings and click Save:
Field Value Identity Resource
managed/alpha_user -
Configure these Patch Object node settings and click Save:
Field Value Patch As Object
Enable.
Identity Resource
managed/alpha_userIdentity Attribute
Keep
userName. -
Configure these Inner Tree Evaluator node settings and click Save:
Field Value Tree Name
Select
ProgressiveProfile.
Task 5: Adjust password policy settings
When Advanced Identity Cloud updates a password, it checks the password policy to prevent weak passwords. Pass-through authentication has no way of ensuring a remote password is valid according to the Advanced Identity Cloud policy.
Default Microsoft Entra ID password policies don’t necessarily match the default Advanced Identity Cloud password policy. Adjust the Advanced Identity Cloud password policy appropriately to avoid rejecting valid Microsoft Entra ID passwords:
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Security > Password Policy.
-
Adjust the settings to avoid rejecting valid Microsoft Entra ID passwords.
-
Click Save.
| This changes the password policy for all identities in the realm. |
Task 6: Allow public client flows in Microsoft Entra ID
Update the Microsoft Entra ID application Advanced Identity Cloud uses for provisioning. This change allows the Advanced Identity Cloud connector to authenticate to Microsoft Entra ID with the username and password:
-
Sign in to the Microsoft Entra ID tenant as administrator.
-
Select Home > App registrations > Microsoft Entra ID application.
-
In the App registrations page, change Authentication > Advanced settings > Allow public client flows to Yes.
-
Click Save.
Validation
You are ready to validate the pass-through authentication journey.
Steps
Validate authentication in each of the following ways.
Default login before
Check the user cannot log in to Advanced Identity Cloud. Advanced Identity Cloud doesn’t have the user’s password:
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Journeys > Login and copy the Preview URL.
-
Paste the URL into an incognito window.
Use incognito mode for testing to avoid caching issues. No current sessions interfere with your test.
The login page for the tenant displays.
-
Log in as the test user.
Log in fails.
Pass-through authentication
Log in with the user’s Microsoft Entra ID credentials, providing the username and password. After Advanced Identity Cloud verifies the credentials in Microsoft Entra ID, it stores the captured password in the user’s profile:
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Journeys > Pass-through authentication with password capture and copy the Preview URL.
-
Paste the URL into an incognito window.
The login page for the pass-through authentication journey displays.
-
Log in as the test user.
Behind the scenes, the journey proceeds as follows:
-
The Data Store Decision node fails to authenticate the user.
-
The Passthrough Authentication node tests the username and password through the connector to Microsoft Entra ID.
You provided the correct credentials, so the test succeeds. The node has confirmed the password is valid.
-
The Identify Existing User node finds the provisioned test user in Advanced Identity Cloud.
-
The Required Attributes Present node checks the shared node state has the
managed/alpha_userattributes needed for a minimally complete user profile. -
The Patch Object node updates the test user profile with the required attributes, capturing the valid password.
-
The Increment Login Count node updates the login count.
-
The Inner Tree Evaluator node invokes the
ProgressiveProfilejourney. -
The journey succeeds and the test user profile displays.
-
Default login after
Advanced Identity Cloud captured the user password during the pass-through authentication journey. The user can now log in to Advanced Identity Cloud directly:
-
Log in to the Advanced Identity Cloud admin UI as an administrator.
-
Select Journeys > Login and copy the Preview URL.
-
Paste the URL into an incognito window.
The login page for the tenant displays.
-
Log in as the test user.
Log in succeeds.
Explore further
Reference material
| Reference | Description |
|---|---|
Get to know the Advanced Identity Cloud admin UI. |
|
Learn about connecting Advanced Identity Cloud to Microsoft Entra ID. |
|
Read about alternative pass-through authentication methods. |
|
Refer to this Microsoft Entra ID documentation for details. |