Certify access using templates and campaigns
In Identity Governance, certifying access means reviewing the data and access a user has, such as access to applications, the accounts in those applications, and more.
Steps to certify access
To certify access for users, you must:
-
Create templates — Allows you to configure the data you want to certify.
-
Run campaigns — After you create a template and are ready to kick off the review process, create a campaign.
-
Certify data and access by end users — After you start a campaign, the template-defined end users (certifiers) receive notifications to review the data. The certifiers' review of the data is referred to as an access review.
Certifications tab
Certifications and related features can be found by selecting Certification from the left navigation bar in the Advanced Identity Cloud admin UI.
Three tabs display under Certification:
Overview tab
To access the Overview tab, from the Advanced Identity Cloud admin UI, go to Certification > Overview.
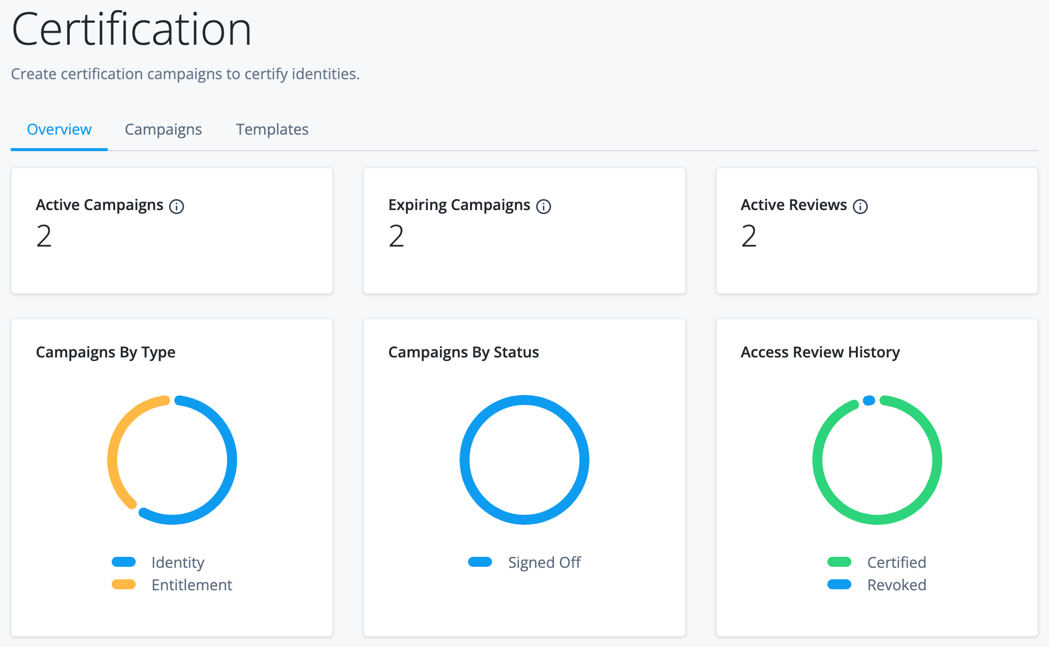
The Overview landing page displays various metrics that allow you to view items such as campaign status, active reviews, and campaigns by type.
You can hover your cursor over the charts to view the data details.
| Data Element | Description |
|---|---|
Active Campaigns |
The number of campaigns currently in progress. |
Expiring Campaigns |
The number of campaigns that expire in the next two weeks. |
Active Reviews |
The total amount of line items in access reviews that are in progress. A line item is a record for a certifier to review. For example, the user Barbara Jensen’s record that details their access to a particular application is a line item. |
Campaigns By Type |
A breakdown of the varying types of certifications. |
Campaigns By Status |
A breakdown of certifications by status. |
access review History |
The number of line items certified versus revoked from campaigns. |
Example of certifying access
As an example of certifying access, let’s say you want to know what applications a specific user, Barbara Jenson, has access to. You may want to do this for a couple of reasons; increasing your company’s security landscape by ensuring users have accurate, appropriate access, or to comply with organizational, industry, or governmental policies. Barbara Jensen has an account and access to an application, called App A.
With Identity Governance, perform the following actions to achieve this:
-
Configure and assign end users (certifiers) in your company to review Barbara’s access to App A using templates.
-
Kick off the data review using campaigns. Campaigns are the active processes, where certifiers review the data. In this case, it is Barbara’s data. Certifiers are assigned to review the data in a campaign.
-
Certifiers review Barbara’s data and either certify (allow) or revoke (remove) the access to App A.