About Autonomous Access
|
End of life for Autonomous Access After much consideration and extensive evaluation of our product portfolio, Ping Identity is discontinuing support for the Advanced Identity Cloud Autonomous Access product, effective October 31, 2024. To support our Autonomous Access customers, we’re offering migration assistance to PingOne Protect, an advanced threat detection solution that leverages machine learning to analyze authentication signals and detect abnormal online behavior. PingOne Protect is a well-established product, trusted by hundreds of customers worldwide. The end of life for Autonomous Access indicates the following:
For any questions, please contact Ping Identity Support for assistance. |
Autonomous Access leverages artificial intelligence (AI) and machine learning (ML) techniques to analyze incoming authentication events and identify abnormal online behavioral patterns. It provides an advanced threat detection solution powered by AI, protecting against account takeover and fraudulent activities at the identity perimeter.
By accelerating and simplifying access decisions, Autonomous Access empowers your organization to efficiently thwart threats while delivering personalized user experiences that enhance online interactions for legitimate users.
Ultimately, Autonomous Access seeks to provide insights based on the following questions:
-
Is the user’s online behavior unusual compared to their typical behavior?
-
If the user typically exhibits similar behavior to a specific group (for example, a department), is their current behavior deviating from the norm in this context?
-
Does the user’s behavior differ from any other patterns observed on the platform?
Ping Identity implements Autonomous Access within your new or existing tenants (development, staging, and production), ensuring that your users' data and personally identifiable information (PII) remain exclusively within the tenant’s boundaries.
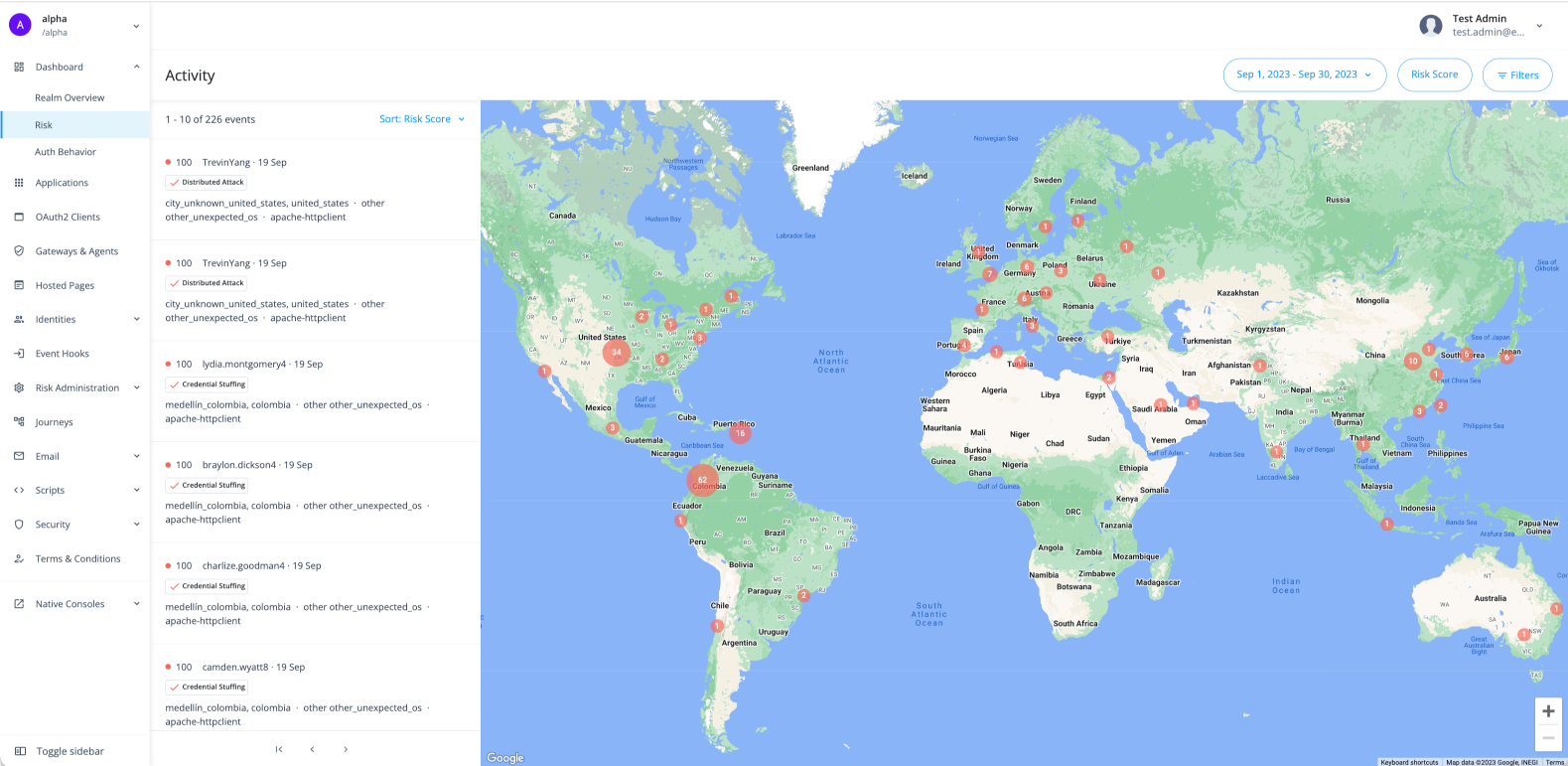
Activity dashboard
The Activity dashboard shows risky access activity and lets users drill in and investigate across time, risk reason, and risk score in the realm that you are currently in (for example, Alpha or Bravo).
Autonomous Access nodes
Autonomous Access provides three prebuilt nodes and a journey template, eliminating the need for custom coding or connectors to implement these journeys. By adding these three nodes, you can fully leverage over 100 nodes to trigger actionable outcomes when high risk scores are discovered.
Risk scores reflect a combination of anomalous behavior and identified threats. You have the flexibility to determine the appropriate actions for different ranges of risk scores. For example, when Autonomous Access returns lower risk scores (e.g., numbers between 0 and 30), you can configure Autonomous Access to allow users to proceed without additional authentication steps. Conversely, for high-risk scores (e.g., numbers between 71 and 100), you can configure Autonomous Access to flag these events for escalation, such as requiring multifactor or step-up authentication, blocking, reviewing, informing the user, or other actions.
The following nodes are available:
-
Autonomous Access signal node: Assesses risk based on anomalous user behavior, credential stuffing, suspicious IPs, automated user agents (bots), impossible travelers, and brute force attacks using AI/ML analytics. The result is a risk score from 0 (no risk) to 100 (high risk).
-
Autonomous Access decision node: Maps the risk score to a high, medium, low, or unknown branch of a journey to direct the user experience.
-
Autonomous Access results node: Sends data back to Autonomous Access for the dashboards and model learning.
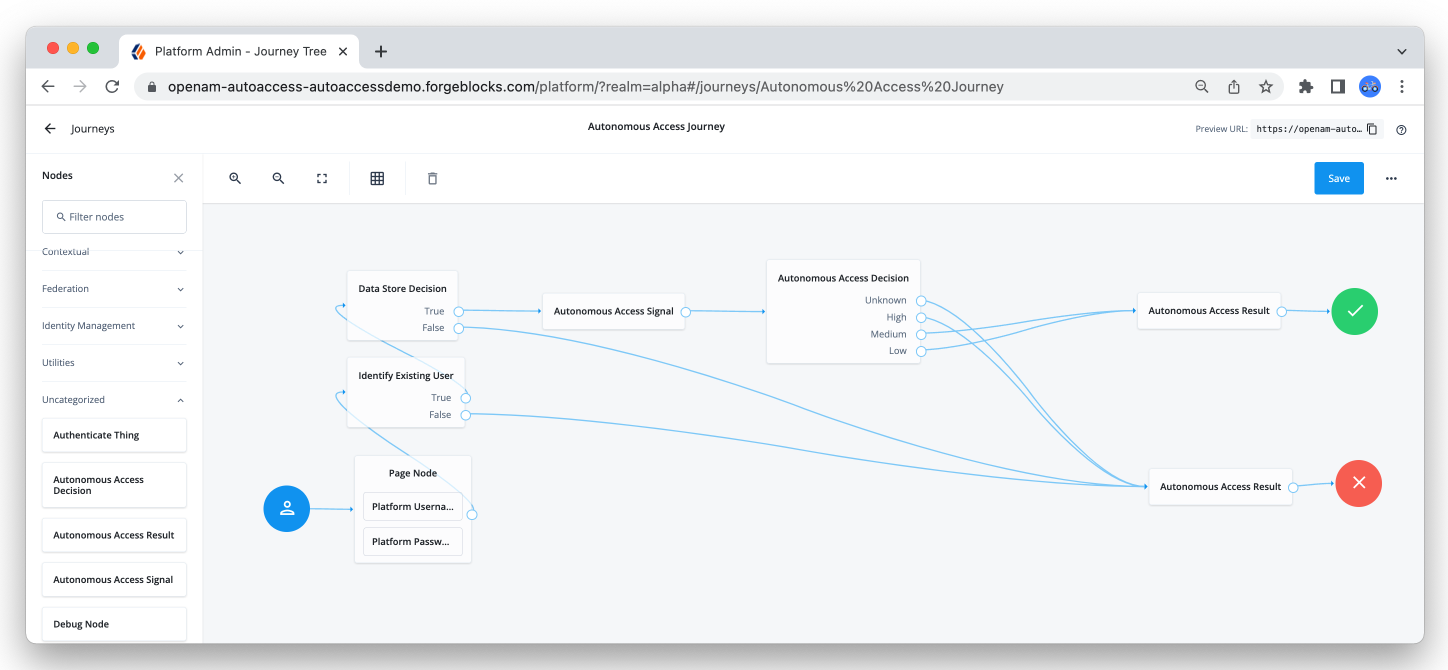 Figure 2. Autonomous Access nodes
Figure 2. Autonomous Access nodes