ThreatMetrix Authentication nodes
Integrates Lexis-Nexis ThreatMetrix decision tools and enable device intelligence and risk assessment in Advanced Identity Cloud.
You can implement ThreatMetrix authentication using these nodes:
The following screenshot shows a typical authentication journey using ThreatMetrix nodes:
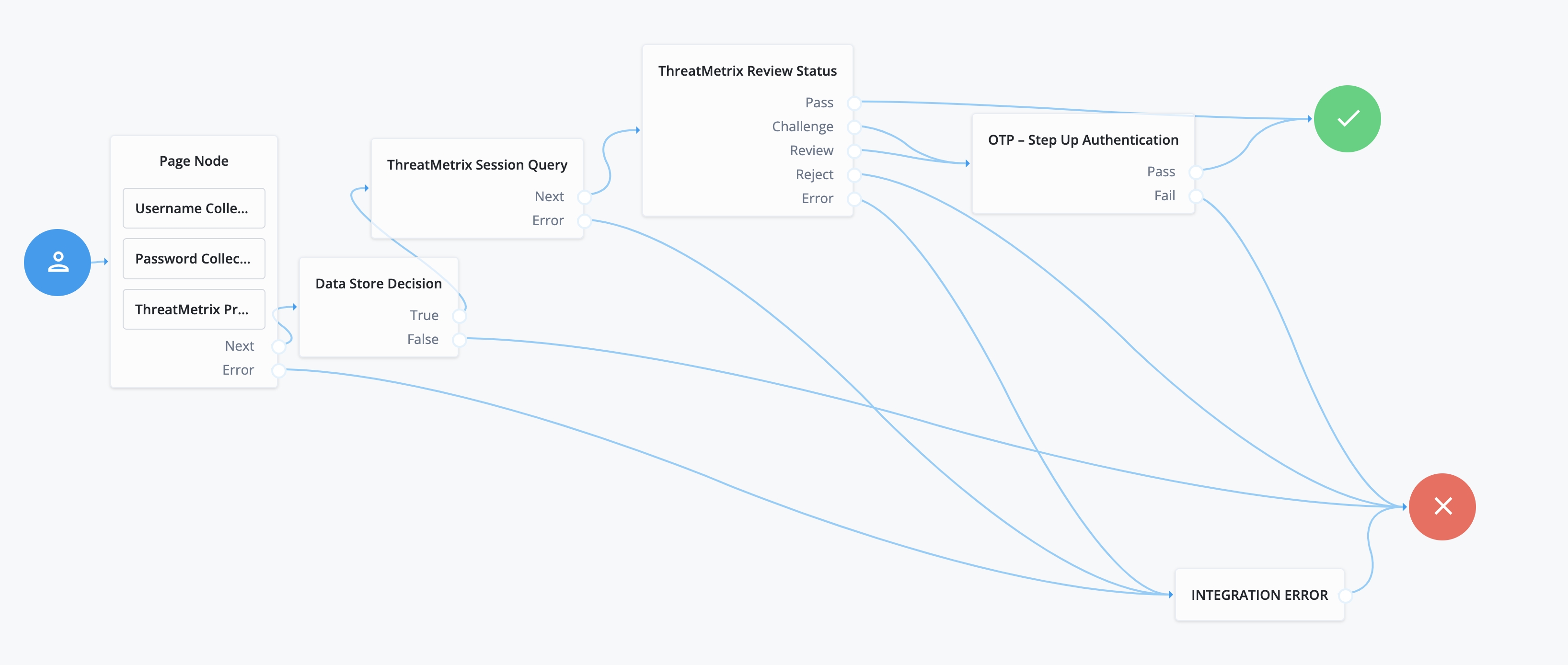
-
The journey starts with a Page node to capture username and password. Simultaneously, the ThreatMetrix Profiler node captures device intelligence information associated to a unique session ID.
-
The ThreatMetrix Session Query node uses the Session ID, along with user personal identifiable information (PII) to make an API call to the LexisNexis Dynamic Decision Platform (DDP) for risk assessment.
-
Risk assessment is performed at the DDP to capture suspicious activity.
-
The result of the risk assessment is captured as an API response in the ThreatMetrix Session Query node.
-
The ThreatMetrix Review Status node interprets the API risk assessment response.
-
The possible outcomes to continue the journey are
Pass,Challenge,Review, orReject. -
The
ChallengeandReviewoutcomes start a step-up second factor authentication. -
Regardless of the step-up authentication, the ThreatMetrix Update Review node adds truth data to the login event which enriches the information in the network and enhance fraud detection.
The example described above shows initialization of step-up MFA along with outcome of either pass or fail.
If a step-up authentication is initialized but is not completed, then it is a sign of potential fraud in a login event.