SSO in integrated mode
Journeys support SSO in integrated mode only via the SAML2 Authentication node. It handles the SAML 2.0 authentication flow but relies on other nodes.
Integrated mode flow (journeys)
-
An unauthenticated user initiates authentication to an Advanced Identity Cloud SAML 2.0 SP. The login URL references an authentication journey that includes a SAML2 Authentication node. For example,
https://<tenant-env-fqdn>/am/XUI/?service=mySAM2LTree. -
Advanced Identity Cloud runs any authentication nodes that precede the SAML2 Authentication node in the journey.
-
The SAML2 authentication node processing begins.
-
The authentication node requests an assertion from the IdP. The configuration of the SAML2 Authentication node determines the details of the request.
-
The IdP requests the user to authenticate if they’ve not already done so.
-
The user provides their credentials.
-
The IdP authenticates the user successfully.
-
The IdP responds to the SP with a SAML assertion.
-
If the SAML assertion contains a non-transient name ID, Advanced Identity Cloud searches the identity store and attempts to locate a user with the same name ID.
If the name ID for the account exists, the journey continues.
If the name ID doesn’t exist...
-
... and the journey has a Create Object node, the node creates a new account in the SP using auto-federation that includes the name ID in the user profile.
-
... and a method of authenticating the user is available in the journey, Advanced Identity Cloud authenticates the user.
-
The Write Federation Information node writes the persistent name ID in the user profile.
For more information about linking when autofederation is not configured, refer to Link identities for authentication.
-
The journey continues…
-
… and authentication is successful.
Implement SAML 2.0 single sign-on in integrated mode
The following list is an overview of the activities you perform when implementing SAML 2.0 single sign-on in integrated mode:
-
Preparing entity providers and a circle of trust and changing several endpoints in the SP configuration.
For more information, refer to Configure Advanced Identity Cloud for integrated mode.
-
Configuring a journey that contains, at least, the SAML2 Authentication node.
For more information, refer to Create accounts dynamically during federation.
Configure Advanced Identity Cloud for integrated mode
-
If you haven’t already done so, configure SAML 2.0 by performing the tasks listed in Deployment considerations.
-
Under Native Consoles > Access Management, create a hosted SP by following the steps in Create a hosted entity provider.
You must configure the attribute map (Assertion Processing > Attribute Mapper) first. This determines how PingOne Advanced Identity Cloud maps assertion attributes from the IdP to the user’s profile on the SP.
During the authentication process, the mapping is used to find existing users on the SP and to create or update user accounts on the SP.
-
Configure a remote IdP by following the steps in Import and configure a remote entity provider.
When you specify the circle of trust for the IdP, use the Add to Existing option and specify the circle of trust you created when you created the hosted SP.
-
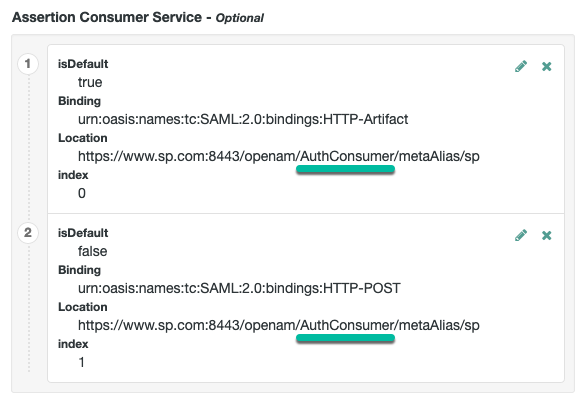
Change the Assertion Consumer Service locations in the hosted SP configuration.
The default locations support standalone mode; therefore, you must change the locations when implementing integrated mode.
Change the locations as follows:
-
Under Native Consoles > Access Management, go to Realms > Realm Name > Applications > Federation > Entity Providers > SP Name > Services > Assertion Consumer Service.
-
Change the location of the HTTP-Artifact consumer service to use
AuthConsumer, rather thanConsumer. For example, if the location ishttps://<tenant-env-sp-fqdn>/am/Consumer/metaAlias/sp, change it tohttps://<tenant-env-sp-fqdn>/am/AuthConsumer/metaAlias/sp. -
Similarly, change the location for the HTTP-POST consumer service to use
AuthConsumerrather thanConsumer.You do not need to change the location for the PAOS service because integrated mode does not support the PAOS binding.
-
The results will resemble the following:
Save your changes. Now you are ready to configure your journey(s).
-
Create accounts dynamically during federation
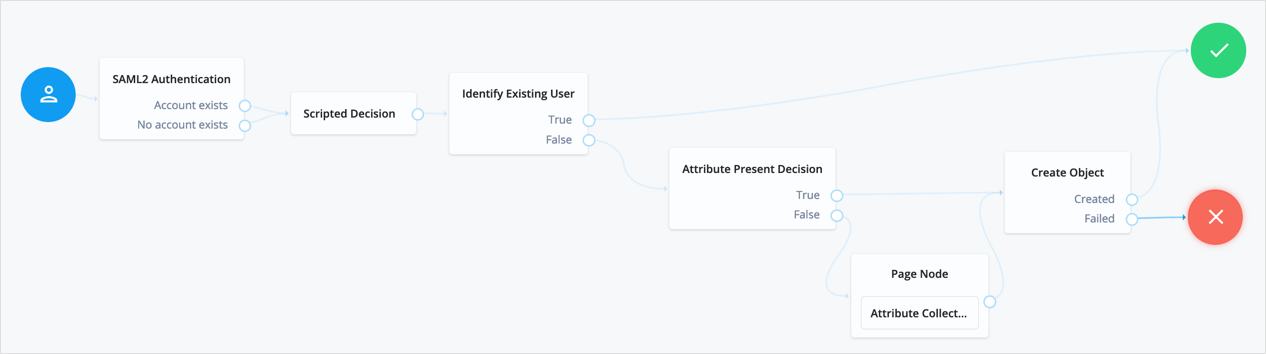
In integrated mode, the SP can use journeys to tailor the authentication experience to the users. You can create multiple complex journeys to satisfy the requirements of your organization.
The example shown in this procedure uses the SAML 2.0 node to request an assertion from the IdP, and then creates an account for the user in the SP if one does not exist.
If you are not using auto-federation, you can also use journeys to create persistent links between user accounts.
Perform the steps in this procedure to configure a journey similar to the following:
-
Add a SAML2 Authentication node.
Integrated mode is SP SSO-initiated only, and SLO is not supported.
The node processes the assertion, makes its contents available to the journey’s state in the
userInfoobject, and tries to map the assertion’s nameID using theuidmapping in the SP’s assertion map.If the node finds a match, the journey continues through the
Account Existsoutput. Otherwise, the journey continues through theNo Account Existsoutput.The attribute the node uses to map the nameID is not configurable. This example adds nodes to process the
userInfoobject and matches its contents to the managed user’s schema. -
Add a Scripted Decision node to copy the information from the assertion to the authentication journey’s shared state.
Example script
-
Next-generation
-
Legacy
if (nodeState.get("userInfo")) { if (nodeState.get("objectAttributes")) { nodeState.remove("objectAttributes"); } var userName=null,sn=null,mail=null; try { var attribs = nodeState.get("userInfo")["attributes"]; userName=attribs["uid"][0]; sn=attribs["sn"][0]; mail=attribs["mail"][0]; } catch (e) { logger.error("Error getting userInfo: " + e); } nodeState.putShared("objectAttributes", {"userName":userName,"sn":sn,"mail":mail}); } action.goTo("true");var fr = JavaImporter(org.forgerock.openam.auth.node.api.Action); if (nodeState.get("userInfo")) { if (nodeState.get("objectAttributes")) { nodeState.remove("objectAttributes"); } var userName=null,sn=null,mail=null; try { var attribs = nodeState.get("userInfo").get("attributes"); userName=attribs.get("uid").get(0).asString(); sn=attribs.get("sn").get(0).asString(); mail=attribs.get("mail").get(0).asString(); } catch (e) { logger.error("Error getting userInfo: " + e); } nodeState.putShared("objectAttributes", {"userName":userName,"sn":sn,"mail":mail}); } action = fr.Action.goTo("true").build();For more information, refer to Scripted decision node API functionality.
-
-
Add an Identify Existing User node to search the user with the appropriate attribute.
For example,
userName. -
Complete the journey by adding the required nodes to create the new account if it doesn’t exist on the SP.
The scripted decision node placed the attributes required to create the account in the journey’s shared state; however, these might not be enough to satisfy your managed user rules.
To ensure the required attributes are available, use the Required Attributes Present node to check them and the Attribute Collector node to collect the ones missing.
Finally, to create the account, use the Create Object node.
You must configure the appropriate identity resource in this node. For example,
managed/alpha_user. -
(Optional) If you haven’t configured auto-federation, you can add the Write Federation Information node to create a persistent link between the accounts.
Refer to Link identities by using journeys for an example.