Create identities automatically with auto-federation
In many instances there isn’t an identity to link with on the SP. For example, if it is the first time a user is attempting to access the service, and they do not have an account in the SP identity store, then there is no way to link from the IDP to the SP.
You can configure PingOne Advanced Identity Cloud to to create an account dynamically for the user in the SP identity store, using the values in the assertion as profile properties, as defined in the attribute mappings.
Create and link identities based on attribute values
Before you configure auto-federation to create identities based on attribute values:
-
Configure PingOne Advanced Identity Cloud for SAML 2.0.
-
Create the IDP.
-
If PingOne Advanced Identity Cloud is the IDP, use the Advanced Identity Cloud admin UI with application management.
-
-
Create SPs.
-
Configure a circle of trust (CoT).
-
Configure PingOne Advanced Identity Cloud to support SSO.
To create missing identities on the SP dynamically:
-
Under Native Consoles > Access Management, go to Realms > Realm Name > Applications > Federation > Entity Providers, and click on the name of the hosted provider.
PingOne Advanced Identity Cloud only displays the configuration of a single role.
To switch between an IDP and SP configuration for a given provider, select the role to view:

-
On the hosted IDP:
-
Go to the Assertion Processing tab.
-
Review the Attribute Map configuration. If the attributes you want to populate when creating the new user are not in the map, add them.
The IDP will send these attributes in the assertion, and the SP will then map them using its own attribute map.
The default IDP mapping implementation allows you to add static values in addition to values taken from the user profile. You add a static value by enclosing the profile attribute name in double quotes (
"), as in the following example: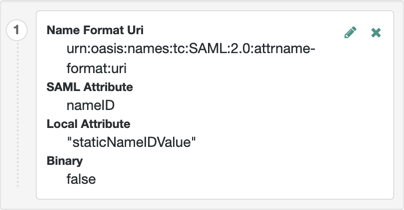
-
Save your work.
-
-
On the hosted SP:
-
Go to the Assertion Processing tab.
-
Review the Attribute Map configuration. The attribute mappings on the IDP are represented in the map.
Tips to configure the attribute map on the SP
The value of Key is a SAML attribute sent in an assertion. The value of Value is a property in the user’s session or an attribute of the user’s profile.
By default, the SP maps the SAML attributes it receives to equivalent-named session properties. However, when the SP is configured to create identities during auto-federation and the identity doesn’t exist yet, the SP maps the SAML attributes to their equivalents in the newly-created user profile.
The special mapping
Key: *, Value: *means that the SP maps each attribute it receives in the assertion to equivalent-named properties or attributes. For example, if the SP receivesmailandfirstnamein the assertion, it maps them tomailandfirstnamerespectively.Remove the special mapping and add key pairs to the map if:
-
During auto-federation the attributes in the IDP and SP’s identity stores do not match.
-
You need control over the names of the session properties.
-
You need control over which attributes the SP should map, because the IDP adds too many to the assertion.
For example, if the SAML attribute is
firstnameand you want the SP to map it to a session property/user profile attribute calledcn, create a mapping similar toKey: firstname, Value: cn. -
-
Enable auto-federation. In the Attribute property, enter the SAML attribute name the SP will use to link accounts, as configured in the Attribute Map.
The value of the named attribute is used as the username of the created user when auto-federation is enabled.
-
Save your work.
-
Navigate to Realms > Realm Name > Authentication > Settings.
-
On the User Profile tab in the User Profile field, select Dynamic or Dynamic with User Alias.
For more information the user profile property, refer to User profile.
-
Save your work.
-
-
To test your work:
-
Create a new user on the IDP, including values for any attributes you mapped in the providers.
-
Log out of the UI and initiate SSO; for example, as described in IDP-Initiated SSO JSP.
-
Authenticate as the new user you created in the IDP.
-
On success, check
https://<tenant-env-sp-fqdn>/enduser/?realm=realm_name/profileand click Edit Personal Info to see the new user account created on the SP, and the attributes that were copied from the assertion.
-