Reference
This reference covers the configuration settings for identity providers (IdPs), service providers (SPs), and circles of trust.
Hosted identity provider
To edit hosted IdP settings, go to Native Consoles > Access Management > Realms > Realm Name > Applications > Federation > Entity Providers > Provider Name.
Assertion Content tab
Signing and Encryption
- Request/Response Signing
-
The parts of messages the IdP requires the SP to sign digitally.
- Encryption
-
When NameID Encryption is selected, the SP must encrypt name identifier (NameID) elements.
- Secret ID and Algorithms
-
- Secret ID Identifier
-
By default, PingOne Advanced Identity Cloud uses the entity provider’s role-specific, default global secret IDs. Alternatively, set an identifier for the secret ID PingOne Advanced Identity Cloud uses for this entity provider when resolving secrets. For example, when you set this to
demo, the entity provider uses the following secret IDs:-
am.applications.federation.entity.providers.saml2.demo.signing -
am.applications.federation.entity.providers.saml2.demo.encryption
-
- Signing Algorithm
-
The algorithms the provider uses to sign the request and response attributes selected in the Request/Response Signing group.
The provider’s metadata extension lists these algorithms.
This property has no default.
- Digest Algorithm
-
The digest algorithms the provider uses to sign the requests and responses selected in the Request/Response Signing group.
The provider’s metadata extension lists these algorithms.
This property has no default.
- Encryption Algorithm
-
There are two types of encryption algorithms for the provider:
-
Symmetric algorithms; the provider uses these to encrypt the objects selected in the Encryption group. Select one or more AES algorithms from the drop-down list.
Default:
http://www.w3.org/2001/04/xmlenc#aes128-cbc -
Asymmetric algorithms; the provider advertises this as the transport key algorithm. When SAML 2.0 token encryption is enabled, hosted providers should use the algorithm the remote provider advertises to encrypt symmetric encryption keys.
Select one or more algorithms from the drop-down list:
-
http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p(default) -
http://www.w3.org/2009/xmlenc11#rsa-oaepFor this algorithm, PingOne Advanced Identity Cloud uses
http://www.w3.org/2009/xmlenc11#mgf1sha256to create the transport key. -
http://www.w3.org/2001/04/xmlenc#rsa-1_5For security reasons, do not use this option.
-
-
NameID Format
- NameID Format List
-
Supported NameIDs for users shared between providers for single sign-on (SSO).
The following diagram shows how the hosted IdP determines which NameID format to use:
- NameID Value Map
-
Map of NameID formats to user profile attributes. You do not need to map the
persistentandtransientNameIDs.NameID mapping supports Base64-encoded binary values. When Binary is enabled, PingOne Advanced Identity Cloud Base64-encodes the profile attribute it adds to the assertion.
Authentication Context
- Mapper
-
A class implementing the
IDPAuthnContextMapperinterface to set up the authentication context.Do not edit this field.
Default:
com.sun.identity.saml2.plugins.DefaultIDPAuthnContextMapper - Authentication Context
-
The supported authentication context classes and any authentication mechanisms PingOne Advanced Identity Cloud uses when an SP specifies the class in a SAML 2.0 authentication request. For details, refer to Authentication Context for the OASIS Security Assertion Markup Language (SAML) v2.0.
Default:
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport-
The Predefined Reference specifies the list of context references.
-
The Key specifies the authentication mechanism PingOne Advanced Identity Cloud uses when an SP specifies the class in a SAML 2.0 authentication request:
- Service
-
Set the Value to the authentication journey to use.
- Module
-
Not supported.
- User
-
Not supported.
- Role
-
Not supported.
- Authentication Level
-
PingOne Advanced Identity Cloud uses a method where the authentication level is greater than or equal to the Value. Match the Value field with the Level field to avoid requiring users to re-authenticate unnecessarily.
If more than one suitable method exists, PingOne Advanced Identity Cloud presents the available options with a
ChoiceCallback.
-
The Value depends on the Key.
-
The Level specifies precedence for supported context reference classes.
Higher numbers are stronger than lower numbers.
-
Assertion Time
- Not-Before Time Skew
-
Grace period in seconds for the
NotBeforetime in assertions. - Effective Time
-
Assertion validity in seconds.
Assertion Processing tab
Attribute Mapper
Extension point to map the IdP attributes included in the SAML assertion.
- Attribute Mapper
-
The Java class for the default implementation, which retrieves attributes from the user profile. If the attributes are not present in the profile, retrieve attributes from the user session.
Do not edit this field. It is not used if Attribute Mapper Script is set.
Default:
com.sun.identity.saml2.plugins.DefaultIDPAttributeMapper - Attribute Mapper Script
-
A JavaScript implementation of an attribute mapper.
Select a
Saml2 IDP Attribute Mapperscript from this realm.For an example, refer to saml2-idp-attribute-mapper.js.
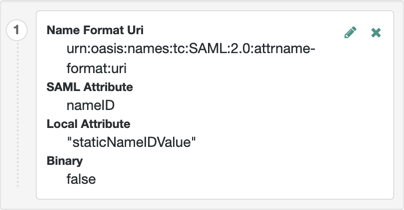
- Attribute Map
-
Maps SAML attributes to user profile attributes or session properties.
The default implementation also supports static values. Enclose the profile attribute name in double quotes (
"):
Account Mapper
- Account Mapper
-
The Java class for the default implementation to map remote users to local user profiles.
- Disable NameID Persistence
-
By default, PingOne Advanced Identity Cloud stores NameIDs the IDP issues when the NameID format is persistent (
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent). When you set this, PingOne Advanced Identity Cloud no longer stores persistent NameIDs.Only enable this setting after configuring a NameID Value Mapping for persistent NameIDs; otherwise, the
ManageNameIDand theNameIDMappingSAML profiles no longer work with persistent NameIDs.PingOne Advanced Identity Cloud does not remove existing, stored account links when you enable this setting.
Local Configuration
- Auth URL
-
If set, overrides the default UI login URL to authenticate users during federation.
Use this setting, for example, if you have created a custom UI for federation.
The application exposing the URL must authenticate federated users, establish their sessions, and return SSO tokens in the tenant session cookies.
PingOne Advanced Identity Cloud must accept the cookie for the domain of the URL. If PingOne Advanced Identity Cloud uses host cookies, the FQDN of the URL must match your tenant’s FQDN.
PingOne Advanced Identity Cloud redirects users to the URL, appending a
gotoparameter. The parameter contains the URL to redirect to after authentication. The application must not override thegotoparameter, as changing it causes federation to fail. For details, refer to Success and failure redirection URLs. - Reverse Proxy URL
-
The URL of the reverse proxy for SAML endpoints if one exists.
- External Application Logout URL
-
The URL to send an HTTP POST with all cookies when receiving a logout request. Add a user session property by including it as a query string parameter named
appsessionproperty.
Services tab
- MetaAlias
-
Read-only alias to locate the provider’s entity identifier, specified as
/realm-name/provider-name; for example:/alpha/myIDP.
IDP Service Attributes
- Artifact Resolution Service
-
The endpoint to manage artifact resolution.
- Single Logout Service
-
The endpoints to manage single logout (SLO) depending on the SAML binding.
- Manage NameID Service
-
The endpoints to manage NameIDs depending on the SAML binding.
- Single SignOn Service
-
The endpoints to manage SSO.
These endpoints are used only for SP-initiated flows but are included as a requirement of the SAML V 2.0 Metadata specification.
- NameID Mapping
-
The endpoint to manage NameID mapping.
- Assertion ID Request Service
-
The endpoints to request a specific assertion by assertion ID.
Advanced tab
SAE Configuration
- IDP URL
-
The endpoint to manage Secure Attribute Exchange (SAE) requests.
- Application Security Configuration
-
Encryption settings for SAE.
ECP Configuration
- IDP Session Mapper
-
A Java class to find a valid session in an HTTP servlet request to an IdP with a SAML Enhanced Client or Proxy (ECP) profile.
Do not edit this field.
Session Synchronization
- Enabled
-
When enabled, the IdP sends backchannel SOAP logout requests to all SPs when a session times out. A session can time out after the maximum idle time or maximum session time, for example.
IDP Finder Implementation
- IDP Finder Implementation Class
-
A Java class to find the preferred IdP for a proxied authentication request.
- IDP Finder JSP
-
A JSP to present the list of IdPs to the user.
- Enable Proxy IDP Finder For All SPs
-
When enabled, PingOne Advanced Identity Cloud applies the finder for all remote SPs.
Relay State URL List
- Relay State URL List
-
List of accepted
RelayStateURLs.PingOne Advanced Identity Cloud validates the
RelayStateredirection URLs against this list during SLO. PingOne Advanced Identity Cloud only allows redirection toRelayStateURLs in this list or matching the tenant domain; otherwise, a browser error occurs.This setting does not apply to IdP-initiated SSO as the SP validates the
RelayStateURL.Use the pattern matching rules in Success and failure redirection URLs to specify URLs.
IDP Adapter
- IDP Adapter Class
-
A Java class PingOne Advanced Identity Cloud invokes immediately before sending a SAML 2.0 response.
- IDP Adapter Script
-
A JavaScript implementation of an IdP adapter.
Select a
Saml2 IDP Adapterscript from this realm.For an example, refer to saml2-idp-adapter.js.
Remote identity provider
After you’ve set up a remote identity provider, configure it under Native Consoles > Access Management > Realms > Realm Name > Applications > Federation > Entity Providers > Provider Name.
Assertion Content
Signing and Encryption
- Request/Response Signing
-
The parts of messages the IdP requires the SP to sign digitally.
- Encryption
-
-
NameID Encryption – When selected, the SP must encrypt NameID elements.
-
- Algorithms
-
Select the signing, encryption and digest algorithms that the SP will use.
NameID Format
- NameID Format List
-
Supported NameIDs for users shared between providers for single sign-on (SSO).
Secrets
-
Secret Label Identifier – Identifier used to create a secret label for mapping to a secret in the secret store. PingOne Advanced Identity Cloud uses this label to create a specific secret label for this entity provider. The secret label takes the form
am.applications.federation.entity.providers.saml2.identifier.basicauthwhere identifier is the value of Secret Label Identifier. The label can only contain charactersa-z,A-Z,0-9, and periods (.). It can’t start or end with a period.If you change the Secret Label Identifier for a specific entity provider, any corresponding mappings are deleted, unless they’re referenced by other entity providers.
Basic Authentication
-
Enabled – Authenticate with the specified username and password when making requests to this entity provider’s SOAP endpoints.
-
User Name – The username with which to authenticate at SOAP endpoints.
-
Password – The password with which to authenticate at SOAP endpoints.
If you set a value for Secret Label Identifier, and PingOne Advanced Identity Cloud finds a mapping to this secret label in the secret store, the value of this Password field is ignored. For example, if you set the Secret Label Identifier to demo and PingOne Advanced Identity Cloud finds a secret mapping to am.applications.federation.entity.providers.saml2.demo.basicauth, PingOne Advanced Identity Cloud uses this secret and ignores the value of the Password field. For basic authentication, there is no default secret label for the realm, or globally.
Client Authentication
These settings let an SP authenticate to the IdP using mutual TLS (mTLS).
When you enable client authentication for any request type in this section, you must configure a secret mapping from one of the following secret labels to a valid secret (ESV) in the secret store:
-
am.default.applications.federation.entity.providers.saml2.sp.mtls– the global or realm-specific mapping for hosted SPs -
am.applications.federation.entity.providers.saml2.identifier.mtls– a mapping for a specific SP, where identifier is the value of the Secret Label Identifier you set in the Secrets panel in the SP configuration.
If you configure a global mapping, a realm-specific mapping, and a mapping for a specific SP, the order of precedence is as follows:
-
Hosted SP-specific mapping
-
Realm-level default
-
Global default
The certificates mapped to these labels are included in the SP metadata export with <KeyDescriptor use="signing">.
Currently, you can enable mTLS for the following request:
-
Artifact Resolve – For artifact resolution requests, the IdP instructs the SP to send a client certificate along with the request.
Services tab
IDP Service Attributes
- Artifact Resolution Service
-
The endpoint to manage artifact resolution.
- Single Logout Service
-
The endpoints to manage SLO depending on the SAML binding.
These endpoints are used only for SP-initiated flows but are included as a requirement of the SAML V 2.0 Metadata specification.
- Manage NameID Service
-
The endpoints to manage NameIDs depending on the SAML binding.
- Single SignOn Service
-
The endpoints to manage SSO.
Hosted service provider
To edit hosted SP settings, go to Native Consoles > Access Management > Realms > Realm Name > Applications > Federation > Entity Providers > Provider Name.
Assertion Content tab
Signing and Encryption
- Request/Response Signing
-
The parts of messages the SP requires the IdP to sign digitally.
- Encryption
-
When selected, the IdP must encrypt the selected elements.
- Secret ID and Algorithms
-
- Secret ID Identifier
-
By default, PingOne Advanced Identity Cloud uses the entity provider’s role-specific, default global secret IDs. Alternatively, set an identifier for the secret ID PingOne Advanced Identity Cloud uses for this entity provider when resolving secrets. For example, when you set this to
demo, the entity provider uses the following secret IDs:-
am.applications.federation.entity.providers.saml2.demo.signing -
am.applications.federation.entity.providers.saml2.demo.encryption
-
- Signing Algorithm
-
The algorithms the provider uses to sign the request and response attributes selected in the Request/Response Signing group.
The provider’s metadata extension lists these algorithms.
This property has no default.
- Digest Algorithm
-
The digest algorithms the provider uses to sign the requests and responses selected in the Request/Response Signing group.
The provider’s metadata extension lists these algorithms.
This property has no default.
- Encryption Algorithm
-
The two types of encryption algorithms for the provider:
-
Symmetric algorithms; the provider uses these to encrypt the objects selected in the Encryption group. Select one or more AES algorithms from the drop-down list.
Default:
http://www.w3.org/2001/04/xmlenc#aes128-cbc -
Asymmetric algorithms; the provider advertises this as the transport key algorithm. When SAML 2.0 token encryption is enabled, hosted providers should use the algorithm the remote provider advertises to encrypt symmetric encryption keys.
Select one or more algorithms from the drop-down list:
-
http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p(default) -
http://www.w3.org/2009/xmlenc11#rsa-oaepFor this algorithm, PingOne Advanced Identity Cloud uses
http://www.w3.org/2009/xmlenc11#mgf1sha256to create the transport key. -
http://www.w3.org/2001/04/xmlenc#rsa-1_5For security reasons, don’t use this option.
-
-
NameID Format
- NameID Format List
-
Supported NameIDs for users shared between providers for SSO.
The following diagram shows how the hosted SP determines which NameID format to use:
- Disable NameID Persistence
-
By default, PingOne Advanced Identity Cloud stores NameIDs the IdP issues when the NameID format is persistent (
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent) and the account manager matched a local user to the assertion. When you set this, PingOne Advanced Identity Cloud no longer stores persistent NameIDs.When you enable this setting, end users must authenticate locally for each SAML login.
Authentication Context
- Mapper
-
A class implementing the
SPAuthnContextMapperinterface to set up the authentication context.Don’t edit this field.
Default:
com.sun.identity.saml2.plugins.DefaultSPAuthnContextMapper - Authentication Context
-
The supported authentication context classes and any authentication mechanisms PingOne Advanced Identity Cloud uses when an IdP specifies the class in a SAML 2.0 authentication request. Learn more in Authentication Context for the OASIS Security Assertion Markup Language (SAML) V2.0.
Default:
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport-
The Predefined Reference specifies the list of context references.
-
The Key specifies the authentication mechanism PingOne Advanced Identity Cloud uses when an IdP specifies the class in a SAML 2.0 authentication request:
- Service
-
Set the Value to the authentication journey to use.
- Module
-
Not supported.
- User
-
Not supported.
- Role
-
Not supported.
- Authentication Level
-
PingOne Advanced Identity Cloud uses a method where the authentication level is greater than or equal to the Value. Match the Value field with the Level field to avoid requiring users to re-authenticate unnecessarily.
If more than one suitable method exists, PingOne Advanced Identity Cloud presents the available options with a
ChoiceCallback.
-
The Value depends on the Key.
-
The Level specifies precedence for supported context reference classes.
Higher numbers are stronger than lower numbers.
-
- Comparison Type
-
Sets the range of authentication mechanisms the IdP can choose.
For example, when this is set to
BetterandPasswordProtectedTransportis the default authentication context class, the IdP must select an authentication mechanism with a higher level assigned.Default:
Exact - Include Request Authentication Context
-
When enabled, include the authentication context class as the requested authentication context in the SAML 2.0 authentication request.
Default: Enabled
Assertion Processing tab
Attribute Mapper
Extension point to map the SP attributes included in the SAML assertion.
- Attribute Mapper
-
The Java class for the default implementation, which sets attributes in the user profile or properties in the session.
Don’t edit this field.
Default:
com.sun.identity.saml2.plugins.DefaultSPAttributeMapper - Attribute Map
-
Maps SAML attributes to user profile attributes or session properties.
The Key is a SAML attribute from the assertion. The Value is the profile attribute or session property.
By default, the SP maps SAML attributes to session properties with the same names. When the SP creates a profile during auto-federation, the SP maps SAML attributes to the new user profile.
The special mapping
Key: *, Value: *maps each attribute in the assertion to a session property or profile attribute with the same name. For example, if the SP receivesmailandgivenNamein the assertion, it maps them tomailandgivenName.Remove the special mapping and add key pairs to the map if:
-
(Auto-federation) The attributes in the IdP’s and the SP’s identity stores do not match.
-
You need control over the names of the session properties.
-
You need control over the attributes to map because the IdP adds too many to the assertion.
-
Auto Federation
- Enabled
-
When enabled, automatically federate the user’s accounts at different providers based on the specified SAML attribute.
- Attribute
-
The SAML attribute to match accounts at different providers.
Account Mapper
- Account Mapper
-
The Java class for the default implementation to map remote users to local user profiles.
- Use Name ID as User ID
-
When selected, fall back to the NameID from the assertion to find the user.
- Transient User
-
When set, map all transient users from the IdP to this profile.
URL
- Local Authentication URL
-
If set, overrides the default redirect URL to use after validating the SAML 2.0 assertion from the IdP.
Use this setting, for example, if you have created a custom UI for federation.
In integrated mode, PingOne Advanced Identity Cloud appends query string parameters to this URL. The parameters contain details to let PingOne Advanced Identity Cloud continue the authentication journey.
In standalone mode, PingOne Advanced Identity Cloud redirects users to the specified URL and appends a
gotoparameter, identifying the next redirect URL for the user. - Intermediate URL
-
A URL to redirect the user to after authentication but before the original URL requested.
- External Application Logout URL
-
The URL to send an HTTP POST with all cookies when receiving a logout request. Add a user session property by including it as a query string parameter named
appsessionproperty.
Services tab
- MetaAlias
-
Read-only alias to locate the provider’s entity identifier, specified as
/realm-name/provider-name; for example:/alpha/mySP.
SP Service Attributes
- Single Logout Service
-
The endpoints to manage SLO depending on the SAML binding.
- Manage NameID Service
-
The endpoints to manage NameIDs depending on the SAML binding.
- Assertion Consumer Service
-
The endpoints to consume assertions, where the order corresponds to the index of the URL in the standard metadata.
The scheme, FQDN, and port configured must exactly match the SPs settings in its metadata.
If the base URL service is configured, PingOne Advanced Identity Cloud uses it to determine the SP’s endpoint URL.
If the URL does not match, the SAML 2.0 flow fails and PingOne Advanced Identity Cloud logs an
Invalid Assertion Consumer Location specifiedmessage.
Advanced tab
SAE Configuration
- SP URL
-
The endpoint to manage SAE requests.
- SP Logout URL
-
The SP endpoint to process global logout requests.
- Application Security Configuration
-
Encryption settings for SAE.
ECP Configuration
- Request IDP List Finder Implementation
-
A Java class to return a list of preferred IdPs trusted for the SAML ECP profile.
Default:
com.sun.identity.saml2.plugins.ECPIDPFinder - Request IDP List Get Complete
-
A URI reference to retrieve the complete list of IdPs if the
IDPListelement is not complete. - Request IDP List
-
A list of IdPs for the ECP client or proxy to contact. The default finder implementation uses this.
IDP Proxy
- IDP Proxy
-
When enabled, PingOne Advanced Identity Cloud adds a
Scopingelement to the authentication request for proxying. - Introduction
-
When enabled, use introductions to find the proxy IDP.
- Proxy Count
-
The maximum number of proxy identity providers.
- IDP Proxy List
-
A list of URIs for preferred proxy IDPs.
Session Synchronization
- Enabled
-
When enabled, the SP sends backchannel SOAP logout requests to all IDPs when a session times out. A session can time out after the maximum idle time or maximum session time, for example.
Relay State URL List
- Relay State URL List
-
List of accepted
RelayStateURLs.PingOne Advanced Identity Cloud validates the
RelayStateredirection URLs against this list during SLO. PingOne Advanced Identity Cloud only allows redirection toRelayStateURLs in this list or matching the tenant domain; otherwise, a browser error occurs.Use the pattern matching rules in Success and failure redirection URLs to specify URLs.
Remote service provider
After you’ve set up a remote service provider, configure it under Native Consoles > Access Management > Realms > Realm Name > Applications > Federation > Entity Providers > Provider Name.
Assertion Content
The following properties appear under the Assertion Content tab:
Signing and Encryption
- Request/Response Signing
-
The requests and responses that the SP requires the IdP to sign digitally.
- Encryption
-
The elements that the SP requires the IdP to encrypt.
-
Attribute Encryption – When selected, the IDP must encrypt SAML attributes.
-
Assertion Encryption – When selected, the IDP must encrypt SAML assertions.
-
NameID Encryption – When selected, IDP must encrypt NameID elements.
-
- Algorithms
-
-
Signing Algorithm – The signing algorithm the SP will use.
-
Digest Algorithm – The digest algorithm the SP will use.
-
Encryption Algorithm – The encryption algorithm the SP will use.
-
NameID Format
-
NameID Format List – The supported name identifiers for users who are shared between providers for single sign-on.
-
NameID Value Map – Map the NameID format to a user profile attribute, for example:
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress=mailorurn:oasis:names:tc:SAML:2.0:nameid-format:persistent=objectGUID;binary.-
Key– The Name ID format to map, for example:urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress -
Value– The profile attribute, for example:mail. -
Binary– Indicates that the profile attribute is binary and should be Base64-encoded when used as the NameID value.
If the specified NameID format is used in the protocol, the corresponding profile attribute value is used as the NameID in the Subject assertion element. This mapping overrides all the values defined in the NameID Value Map on the hosted IdP. For example, if a NameID Value Map is defined for the SP and a request is made with a specific NameID Format that only exists on the IdP, it will fail.
-
-
Disable NameID Persistence Disables the storage of NameID values at the IdP when generating an assertion for this remote SP.
Default value:
false
Secrets
-
Secret Label Identifier – Identifier used to create a secret label for mapping to a secret in the secret store.
PingOne Advanced Identity Cloud uses this label to create a specific secret label for this entity provider. The secret label takes the form
am.applications.federation.entity.providers.saml2.identifier.basicauthwhere identifier is the value of Secret Label Identifier. The label can only contain charactersa-z,A-Z,0-9, and periods (.). It can’t start or end with a period.If you change the Secret Label Identifier for a specific entity provider, any corresponding mappings are deleted, unless they’re referenced by other entity providers.
If you specify a value for Secret Label Identifier, and PingOne Advanced Identity Cloud finds a mapping to this secret label in the secret store, the value of the Password field is ignored. For basic authentication, there is no default secret label for the realm, or globally.
Basic Authentication
-
Enabled – Require authentication with the specified username and password at SOAP endpoints.
-
User Name – The username used to authenticate at SOAP endpoints.
-
Password – The password used to authenticate at SOAP endpoints.
If you specify a value for Secret Label Identifier, and PingOne Advanced Identity Cloud finds a mapping to this secret label in the secret store, the value of the Password field is ignored. For basic authentication, there is no default secret label for the realm, or globally.
Assertion Processing
Services
The following properties appear under the Services tab:
SP Service Attributes
- Single Logout Service
-
The endpoints to manage SLO depending on the SAML binding.
- Manage NameID Service
-
The endpoints to manage NameIDs depending on the SAML binding.
- Assertion Consumer Service
-
The endpoints to consume assertions, where the order corresponds to the index of the URL in the standard metadata.
Advanced settings
Request Processing
- Skip Endpoint Validation For Signed Requests
-
When enabled, PingOne Advanced Identity Cloud doesn’t verify assertion consumer service (ACS) URLs in SAML authentication requests. The ACS URL can contain dynamic query parameters, for example.
The SAML 2.0 specification requires ACS URL verification. When you enable this, the SP must digitally sign the authentication request; in Assertion Content > Signing and Encryption > Request/Response Signing, enable Authentication Requests Signed. If PingOne Advanced Identity Cloud receives an unsigned authentication request, it returns an error.
SAE Configuration
- SP URL
-
The endpoint to manage SAE requests.
- SP Logout URL
-
The SP endpoint to process global logout requests.
IDP Proxy
- IDP Proxy enabled
-
When enabled, authentication requests from the SP can be proxied.
- Proxy all requests
-
When enabled, PingOne Advanced Identity Cloud proxies every authentication request from the SP, even if the
Scopingelement is missing.Set IDP Proxy enabled for this setting to take effect.
- Introduction enabled
-
When enabled, use introductions to find the proxy IdP.
This property requires a non-default SAML2IDPProxyFRImpl implementation.
- Use IDP Finder
-
When enabled, PingOne Advanced Identity Cloud uses the IDP finder service to determine the proxy IDP.
- Proxy Count
-
The maximum number of proxy identity providers. PingOne Advanced Identity Cloud sets the specified value in the
Scopingelement of proxied authentication requests.Enable Proxy all requests for this setting to take effect.
- IDP Proxy List
-
A list of URIs for preferred proxy IdPs.
Circle of trust
To edit circle of trust settings, go to Native Consoles > Access Management > Realms > Realm Name > Applications > Federation > Circle of Trust > Circle of Trust Name.
- Name
-
String to refer to the circle of trust.
You can’t change its Name after creation.
- Description
-
Short description for the circle of trust.
- Status
-
Whether this circle of trust is operational.
- Entity Providers
-
Known hosted and remote IdPs and SPs participating in this circle of trust.
- SAML2 Writer Service URL
-
SAML 2.0 service to write IdP entity identifiers to common domain cookies after successful authentication for IdP discovery; for example:
https://[.var]##<tenant-env-fqdn>##/am/saml2writer. - SAML2 Reader Service URL
-
SAML 2.0 service to read ID entity identifiers from common domain cookies for IdP discovery; for example:
https://[.var]##<tenant-env-fqdn>##/am/saml2reader.