Link identities for authentication
IdPs and SPs must be able to communicate about users.
Yet, in some cases, the IdP chooses to communicate a minimum of information about an authenticated user;
for example, a generated, opaque NameID that cannot directly be used
to locate to an identity in the SP identity store.
PingOne Advanced Identity Cloud can use these pseudonym identifiers for establishing links between otherwise unrelated accounts, by requiring that the user authenticates to the SP using a linking authentication mechanism.
First authentication to the SP
The following list describes the sequence of events that occurs the first time a user attempts to authenticate to the PingOne Advanced Identity Cloud SP:
-
Accessing the SP.
A user attempts to access a service and is redirected to PingOne Advanced Identity Cloud which acts as the SP, specifying the SAML 2.0 service in the login URL.
For example, a journey containing the SAML2 Authentication node:
https://<tenant-env-sp-fqdn>/am/XUI/#login/&service=spSAMLJourney -
Authentication at the IdP.
PingOne Advanced Identity Cloud redirects the user to the IdP. The user authenticates successfully to the IdP. The IdP returns a SAML assertion to the SP.
-
SP attempts to access a federated identity.
PingOne Advanced Identity Cloud attempts to locate the identity in its user store. No link between the IdP identity and a local one is found.
-
Authenticating the user to the SP
PingOne Advanced Identity Cloud goes through a path in the journey that lets the user authenticate on the SP.
-
Identity federation.
After successful authentication at the SP, PingOne Advanced Identity Cloud writes the name ID from the assertion into the local user’s profile, creating a permanent link between the two identities.
For more information on creating permanent links between identities, refer to Enable persistent federation.
For an example of a journey that links identities, refer to SSO and SLO in Integrated Mode.
Subsequent authentications to the SP
The following list describes the sequence of events that occur during subsequent authentication attempts, after the user’s identities on the IdP and SPs have been federated:
-
Accessing the SP.
A returning user attempts to access their service and is redirected to PingOne Advanced Identity Cloud, which acts as the SP. Their login URL specifies the SAML 2.0 login service.
For example, a journey containing the SAML2 Authentication node and the Write Federation Information node:
https://<tenant-env-sp-fqdn>/am/XUI/#login/&service=spSAMLJourney. -
Authentication at the IdP.
PingOne Advanced Identity Cloud redirects the user to the IdP, and the user authenticates successfully at the IdP. The IdP returns a SAML assertion to the SP.
-
SP attempts to access a federated identity.
PingOne Advanced Identity Cloud attempts to locate the name ID in its user store. The search for the name ID succeeds.
When there is a match, the user does not need to log in to the SP and is given access to the service.
Link accounts persistently
If you are not using auto-federation, perform the steps in this procedure to configure a journey, similar to the following, to link accounts persistently:
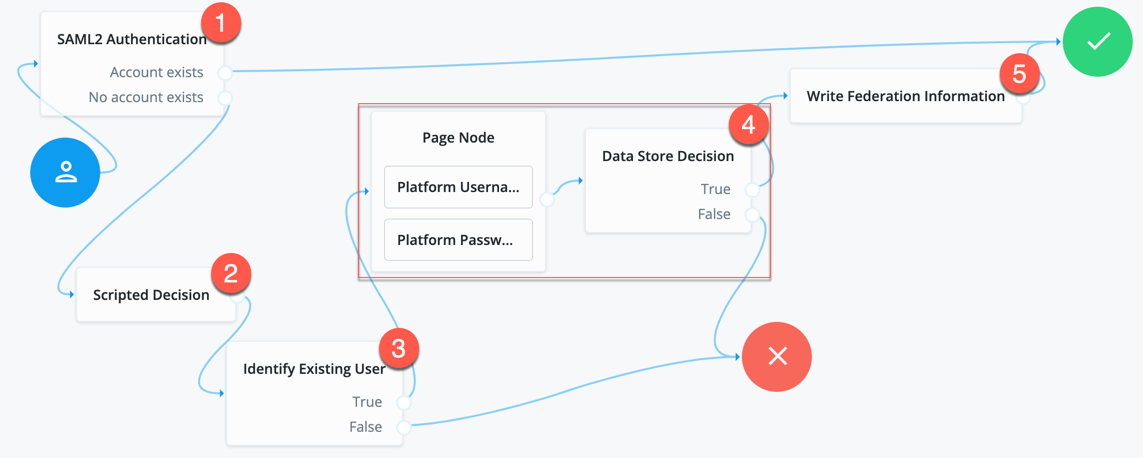
-
Add a SAML2 Authentication node.
Integrated mode is SP SSO-initiated only and SLO is not supported.
Ensure the NameID Format specified is
persistent.The node processes the assertion, makes its contents available to the journey’s shared state in the
userInfoobject, and tries to map the assertion’s nameID using theuidmapping in the SP’s assertion map.If the node finds a match, the journey continues through the
Account Existsoutput. Otherwise, the journey continues through theNo Account Existsoutput.The attribute the node uses to map the nameID is not configurable, and this example adds nodes to process the
userInfoobject and match its contents to the managed user’s schema instead. -
Add a Scripted Decision node to copy the information from the assertion to the journey’s shared state.
Example script
-
Next-generation
-
Legacy
if (nodeState.get("userInfo")) { if (nodeState.get("objectAttributes")) { nodeState.remove("objectAttributes"); } var userName=null,sn=null,mail=null; try { var attribs = nodeState.get("userInfo")["attributes"]; userName=attribs["uid"][0]; sn=attribs["sn"][0]; mail=attribs["mail"][0]; } catch (e) { logger.error("Error getting userInfo: " + e); } nodeState.putShared("objectAttributes", {"userName":userName,"sn":sn,"mail":mail}); } action.goTo("true");var fr = JavaImporter(org.forgerock.openam.auth.node.api.Action); if (nodeState.get("userInfo")) { if (nodeState.get("objectAttributes")) { nodeState.remove("objectAttributes"); } var userName=null,sn=null,mail=null; try { var attribs = nodeState.get("userInfo").get("attributes"); userName=attribs.get("uid").get(0).asString(); sn=attribs.get("sn").get(0).asString(); mail=attribs.get("mail").get(0).asString(); } catch (e) { logger.error("Error getting userInfo: " + e); } nodeState.putShared("objectAttributes", {"userName":userName,"sn":sn,"mail":mail}); } action = fr.Action.goTo("true").build();For more information, refer to Scripted decision node API functionality.
-
-
Add an Identify Existing User node to search the user with the appropriate attribute.
For example,
userName. -
Authenticate the user to the SP.
-
Add the Write Federation Information node to the successful outcome of the authentication process to create the link between the accounts.
If a transient link exists, it is converted into a persistent one.