Plan for Advanced Identity Cloud
To plan for your organization’s future using the cloud, you need a comprehensive, enterprise-grade identity platform that supports your priorities, such as:
-
Intuitive usability
-
Extensive customizations
-
Detailed configuration options
-
Wide-range of functionality
-
Operational ease
The Advanced Identity Cloud checklist highlights the top 10 considerations and best practices for your PingOne Advanced Identity Cloud strategy.
As you consider implementing Advanced Identity Cloud in your organization, the topics in the plan for Advanced Identity Cloud section (also referred to as the Adoption Framework Guide) provide guidance to help you effectively integrate the Advanced Identity Cloud services into your business environment.
Your transition into Advanced Identity Cloud does not have to be a hard transition. It can be a phased approach. For example, you can migrate a key business application into Advanced Identity Cloud and then transition other applications later.
|
There are functional differences between Advanced Identity Cloud and self-managed Ping Identity Platform. Learn more about migrating from a self-managed version of Ping Identity Platform to Advanced Identity Cloud in the knowledge base article FAQ: Functionality differences when moving to Advanced Identity Cloud. Learn more about which Ping Identity downloadable components are compatible with Advanced Identity Cloud in the knowledge base article What downloadable components are compatible with Identity Cloud? |
The framework evolved from the best practices of Ping Identity employees, partners, and customers to help customers adopt Advanced Identity Cloud services. Proficiency in deploying, customizing, and administering the Advanced Identity Cloud is essential for the successful adoption of the Advanced Identity Cloud services. ForgeRock University offers training to architect, build, and deploy your identity solution using the Ping Identity platform.
| The topics in the Plan for Advanced Identity Cloud section use Software to SaaS (S2S) to refer to the process of migrating customers from a self-managed deployment to Advanced Identity Cloud. |
Create an implementation team
The successful adoption is dependent on establishing a project implementation team with the following roles or expertise:
-
Project sponsor
-
Project manager
-
Implementation engineers
-
UI developers
-
JavaScript developers
-
Enterprise architect
-
Operations
-
Performance testing
Gather project information
Timely gathering of the following information is essential:
-
Current project plan and important milestones
-
Enterprise architecture diagrams
-
Target system access and authentication methods
-
Directory service information and data model (such as business units, user roles, groups, object hierarchy)
-
Descriptions of existing identity and access management processes, procedures, and logic (such as sequence diagrams)
-
Current and planned technical changes within the timeframe of the project
-
Identity onboarding and offboarding flows
-
Relevant system access and approval groups, as well as associated authority levels
Adoption phases
The adoption of Advanced Identity Cloud services is best accomplished using existing products, proven methods, and reusable tools built from global field experience, in the following phases:
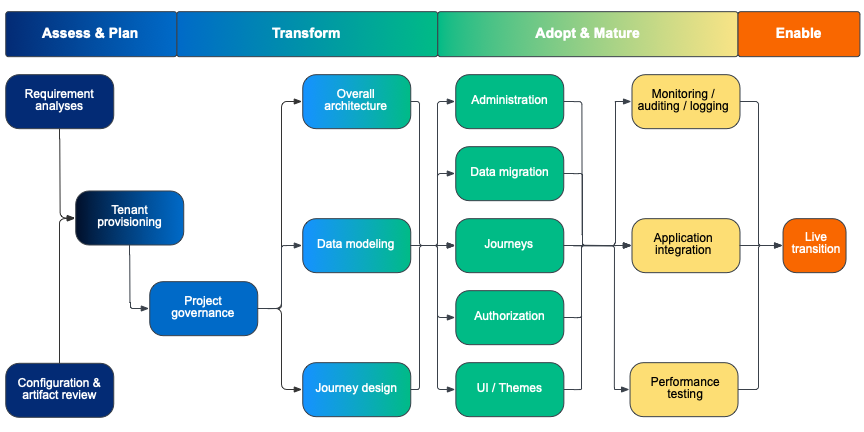
-
-
Analyze functional and nonfunctional requirements
-
Review most significant use cases for phase 1
-
Review existing Ping Identity platform configurations for S2S movement
-
Provision tenants and set up project governance
-
-
-
Define overall architecture
-
Define required data models
-
Define migration path for application data and solution configurations
-
-
-
Set up basic administration interfaces
-
Migrate data
-
Migrate configurations leveraging proven migration toolsets (for S2S)
-
Define journeys
-
Integrate applications
-
-
-
Set up operational and monitoring interfaces
-
Perform functional and performance tests
-
Transition to Advanced Identity Cloud in phases
-
Hand over to Ping Identity support team
-
Support
Customers can access and manage the resources linked to their support subscription. Customer’s nominated administrators can manage users, access policies, and application integration. Learn about how to get started with Backstage Support in the knowledge base article Getting Started with Support.